Researchers have recently uncovered a novel ransomware variant known as 3AM. Their inquiry unveiled that the initial documented instance of this ransomware emerged when malicious actors replaced it with LockBit ransomware during an unsuccessful cyber assault.
Ordinarily, ransomware affiliates possess an array of tools at their disposal for executing attacks. Similarly, this fresh strategy illustrates their capability to wield multiple ransomware strains, persistently pursuing their targets to guarantee the triumph of their assaults.
In this particular case, the attackers first tried to use LockBit but couldn’t, so they used 3AM instead.
Symantec’s report suggests that while it’s not the first time attackers have tried using two different ransomware strains, it’s still a new approach. The fact that a LockBit affiliate turned to 3AM as a backup might attract the attention of other malicious actors. This suggests the possibility of encountering 3AM in future attacks.
This phenomenon also highlights the increasing independence of ransomware affiliates from operators, and could pave the way for a new trend in ransomware attacks.
On the same day we released this post, the 3AM (ThreeAM) Ransomware group unveiled their leak sites and included six organizations on their list of victims, comprising five from the United States and one from Malaysia.
It remains uncertain whether this occurrence was a deliberate publicity move or simply a coincidence for the group, given that they surfaced just as the researchers pinpointed the strain.
Outline of a 3AM Ransomware Attack
3AM is a recently created ransomware coded in Rust, functioning as a 64-bit executable capable of running various commands. These commands have the power to stop applications, hinder backup procedures, and deactivate security software.
Researchers found that the 3AM ransomware only encrypts specific files and adds “.threeamtime” to their names, while also attempting to delete Volume Shadow (VSS) copies.
Following encryption, the ransomware generates a TXT file named “RECOVER-FILES” in each scanned folder, containing the ransom note:
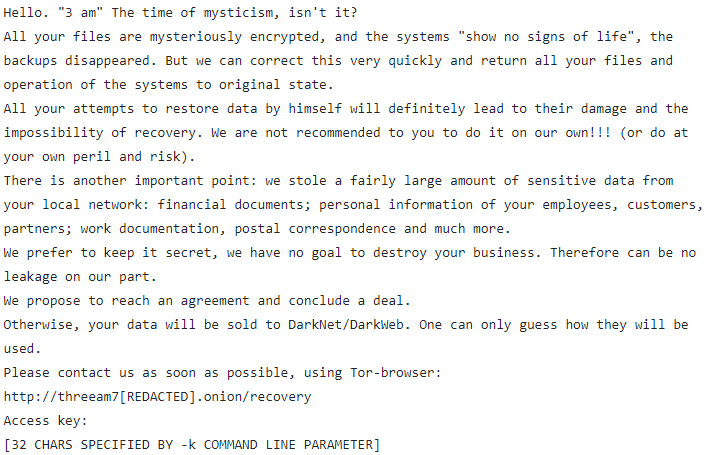
Symantec researchers found that during the unsuccessful LockBit attack, threat actors used the 3AM ransomware on three computers in the target organization’s network, but they were unsuccessful on two of them.
The attackers were seen using the post-exploitation tool Cobalt Strike and running reconnaissance commands like “whoami,” “netstat,” “quser,” and “net share” to move through the network. To stay undetected, the attackers created a new user and employed the Wput tool to send files to their FTP server.
Following a successful attack, the attackers wait for the victims to reach out. They utilize a TOR support portal for 3AM to engage in negotiations regarding ransom payments with the victims.
Indicators of Compromise (IoCs) Related to 3AM Ransomware
File hash (SHA256):
- 079b99f6601f0f6258f4220438de4e175eb4853649c2d34ada72cce6b1702e22 (LockBit)
- 307a1217aac33c4b7a9cd923162439c19483e952c2ceb15aa82a98b46ff8942e (3AM)
- 680677e14e50f526cced739890ed02fc01da275f9db59482d96b96fbc092d2f4 (Cobalt Strike)
- 991ee9548b55e5c815cc877af970542312cff79b3ba01a04a469b645c5d880af (Cobalt Strike)
- ecbdb9cb442a2c712c6fb8aee0ae68758bc79fa064251bab53b62f9e7156febc (Cobalt Strike)
Network indicators:
- 185.202.0[.]111
- 212.18.104[.]6
- 85.159.229[.]62
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment