Two-tailed Scorpion, a hacking group known for its cyberattacks in the Middle East had recently been found to pose itself as legitimate messaging applications such as Telegram and Threema to infect Android devices with a new, previously undocumented malware.
These threat actors are known due to its use of Windows and Android components for their operations. The malware variant has been tracked as Android/SpyC23.
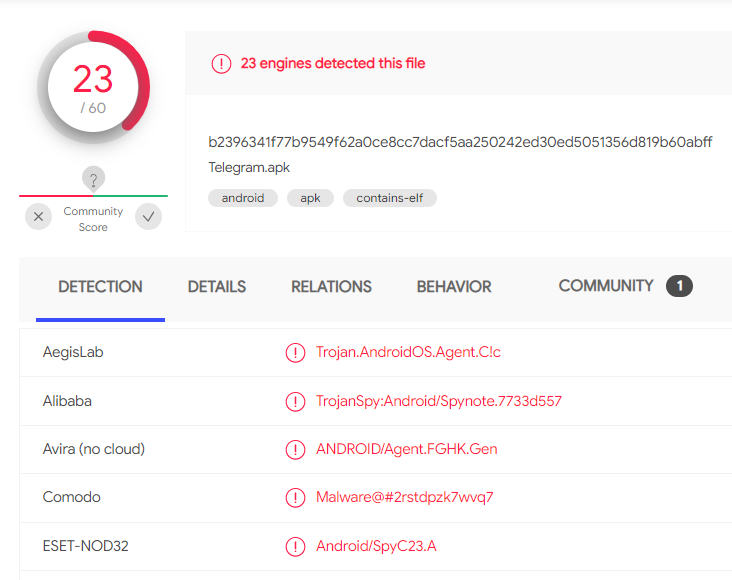
Two-tailed Scorpion was first detected by Qihoo 360 in 2017. Months after, Palo Alto Networks and several other security firms described other versions of the mobile malware.
According to the VirusTotal service, no security vendor besides ESET detected the sample back then. In cooperation with Malware Hunter Team, ESET recognized the malware to be part of the APT-C-23 toolkits.

The “DigitalApps” store, contained both malicious and clean items. The non-malicious items would redirect users to another unofficial Android app store, serving legitimate apps. The malware was hidden in apps posing as AndroidUpdate, Threema, and Telegram. The latter two of these lures also downloaded the impersonated apps with full functionality along with the malware.

Once an app has been installed from the ‘DigitalApps’ App Store the remote attackers will pretty much have control of your device and will be able to do the following:
- Take pictures
- Record audio, Restart Wi-Fi
- Exfiltrate call logs, SMS message, contacts
- Download files to the device
- Delete files from the device
- Steal files with particular extensions (pdf, doc, docx, ppt, pptx, xls, xlsx, txt, text, jpg, jpeg, png)
- Uninstall any app installed on the device
- Steal APK installers of apps installed on the device
- Hide its icon
- Get credit balance of SIM on the device (it can get a balance by making a call to three different cellular operators: Jawwal, Wataniya, Etisalat)
Interestingly, the downloads were limited by needing to enter a six-digit coupon code. This may be a way to prevent those not targeted by the group from installing the malware and hence keep a lower profile. The malware communicates with its command-and-control (C2) server to register the newly infected victim and transmit the device information.
The malware’s live C&C servers typically pose as websites under maintenance, all using the same logo.
Recommendations
- Do not download any Apps from “DigitalApps”
- Download Apps only from the official Google Play Store
- Recommended to scrutinizing the app’s developer, double-checking the permissions requested
- Using a trustworthy and up-to-date mobile security solution.
Indicators of Compromise (IoCs)
ESET detection name
Android/SpyC23.A
Hashes
9e78e0647e56374cf9f429dc3ce412171d0b999e
344f1a9dc7f8abd88d1c94f4323646829d80c555
56f321518401528278e0e79fac8c12a57d9fa545
9e1399fede12ce876cdb7c6fdc2742c75b1add9a
6f251160c9b08f56681ea9256f8ecf3c3bcc66f8
91c12c134d4943654af5d6c23043e9962cff83c2
78dd3c98a2074a8d7b5d74030a170f5a1b0b57d4
1c89cea8953f5f72339b14716cef2bd11c7ecf9a
e79849c9d3dc87ff6820c3f08ab90e6aeb9cc216
C&Cs
https://linda-gaytan[.]website
https://cecilia-gilbert[.]com
https://david-gardiner[.]website
https://javan-demsky[.]website
Distribution URL
https://digital-apps[.]store













Leave A Comment