
The 2FA application necessary to access BBVA bank accounts in Spain is impersonated by a new Android banking malware called Revive. Instead of aiming to infect consumers of various financial institutions, this trojan has a more targeted strategy that targets the BBVA bank.
Revive Malware
Revive belongs to a category of malware used for persistent campaigns, as it was developed and tailored for a specific target.
This type of malware is quite different from other Android banking trojans, such as TeaBot or SharkBot which attack multiple banks/crypto apps installed on the infected device through their modular architecture.
When Revive is installed, it asks for authorization to use the Accessibility Service, giving it full access to the screen and the power to tap the screen and navigate. It would seem typical for a 2FA service that users are asked to enable access to SMS and phone calls when they use the app for the first time. After that, Revive continues to function as a straightforward keylogger in the background.
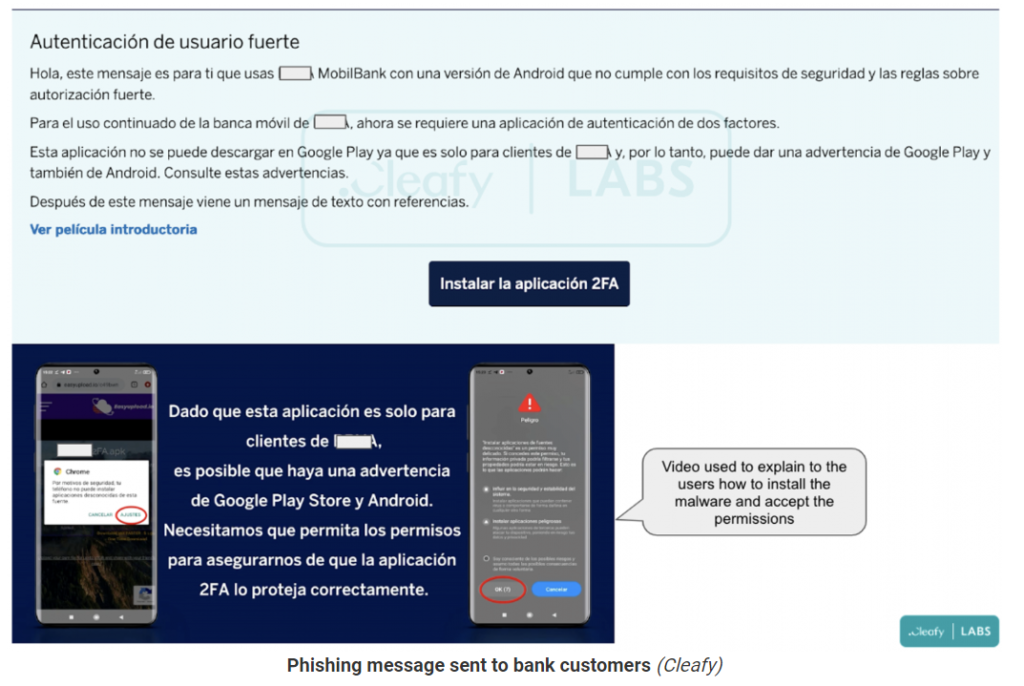
It captures whatever the user enters on the device and routinely transferring it to the C2. By doing this, the credentials will be sent to the C2 of the threat actors, and a generic homepage with connections to the targeted bank’s website.
According to Cleafy’s analysis of the new malware’s source code, it appears that Teradroid, an Android spyware with its source code published on GitHub, served as inspiration for its creators.
File Hash
- 4240473028f88a3ef54f86f1cd387f24
- cf704e63652c23c2d609e9a01659511c




