AVrecon malware infects 70,000 Linux routers, forming a botnet for bandwidth theft and a hidden residential proxy service.
AVrecon malware
Recently, a Linux-based Remote Access Trojan (RAT) was brought to light by security researchers at Lumen Black Lotus Labs.
This insidious RAT has managed to infiltrate small-office/home-office (SOHO) routers, operating covertly and evading detection for over two years.
This multi-year campaign has reached a worrying scale, involving over 70,000 distinct IP addresses from 20 countries communicating with 15 unique second-stage command-and-control servers (C2s) within a 28-day period. Additionally, approximately 41,000 nodes have been persistently infected.
Once infected, the malware transmits the router’s information to an embedded command-and-control (C2) server, which then instructs the compromised device to establish communication with a separate set of servers called second-stage C2 servers.
Security researchers identified 15 such second-stage control servers, which have been operating since at least October 2021, based on x.509 certificate information.
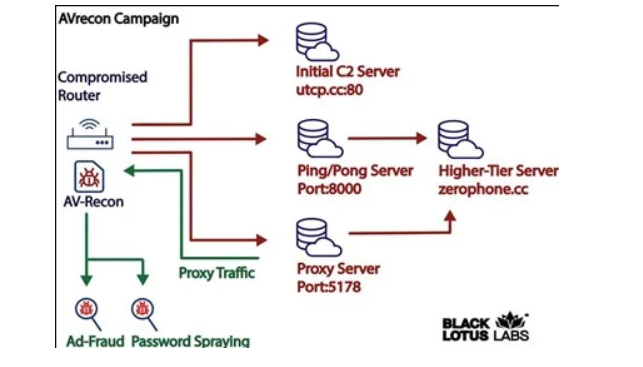
Lumen’s Black Lotus security team successfully neutralized the AVrecon threat by null-routing the botnet’s command-and-control (C2) server using their backbone network.
This action effectively severed the connection between the malicious botnet and its central control server, greatly impeding its capacity to carry out malicious activities.
The concern lies in threat actors being able to compromise these devices, which would grant them access to incorporate the compromised routers into their attack infrastructure. This would serve as a launching point for them to infiltrate internal networks, as cautioned by CISA.
The severity of this threat is amplified by the fact that SOHO routers typically fall outside the conventional security perimeter, significantly impeding defenders from detecting malicious activities.
In a joint advisory released by the Five Eyes cyber security agencies (including the FBI, NSA, and CISA) in May, it was revealed that the Chinese cyber espionage group Volt Typhoon employed a similar approach.
They utilized hacked ASUS network equipment, Cisco, D-Link, Netgear, FatPipe, and Zyxel SOHO devices to create a covert proxy network, concealing their malicious actions within legitimate network traffic.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment