A new wave of cyber espionage has highlighted BPFDoor, a stealthy malware used to secretly access and control networks.
Trend Micro links BPFDoor to a state-backed APT group called Earth Bluecrow (also known as Red Menshen).It uses reverse shells and advanced packet filtering to target sectors like telecom, finance, and retail in countries including South Korea, Hong Kong, Myanmar, Malaysia, and Egypt.
BPFDoor Malware
BPFDoor, also known as Backdoor.Linux.BPFDOOR, is a powerful backdoor that uses BPF—a low-level packet filtering tool in the Linux kernel. While it works like a rootkit, its real strength is staying hidden from firewalls and standard network scans.
It activates when it receives special “magic sequences” — unique byte patterns in network packets that tell it what to do.
BPFDoor hides itself by changing its process name, not listening on open ports, and avoiding security logs.
These stealth features make it ideal for long-term spying, letting attackers stay inside a network for a long time without being noticed.
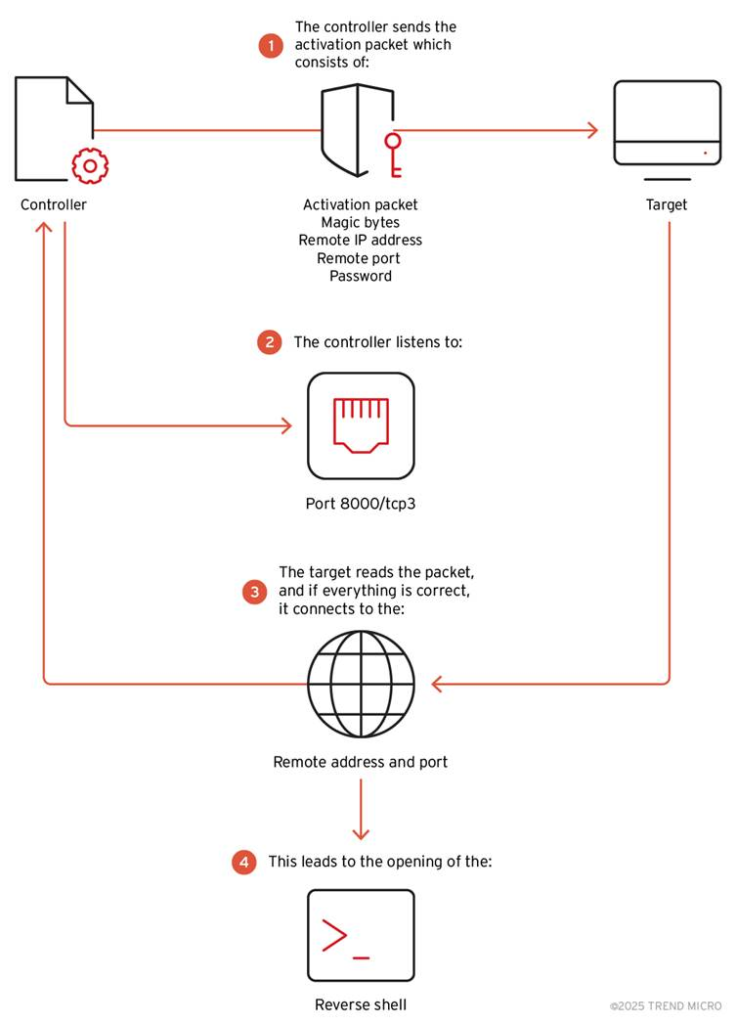
Reverse Shell Technique and Lateral Movement
BPFDoor uses reverse shells to quietly take control of infected systems.
A reverse shell lets attackers run remote commands by flipping the usual communication flow—making the infected server reach out to the attacker. This helps them move deeper into the network and access more systems or sensitive data.
Hackers use a custom tool to launch these reverse shells over TCP, UDP, or ICMP protocols. Once active, the malware connects back to the attacker while avoiding standard security checks.
BPFDoor can open an encrypted reverse shell to give attackers remote access to an infected system. Its controller lets them change settings like passwords, magic bytes, and destination ports, allowing the malware to be easily customized. This flexibility helps Earth Bluecrow adapt its attacks to different industries and regions.
BPFDoor mainly targets Linux servers in key sectors like telecom, finance, and retail. Recent attacks hit companies in South Korea, Myanmar, Egypt, and Malaysia. Security teams should watch for unusual TCP, UDP, or ICMP traffic with suspicious patterns linked to BPFDoor.
BPFDoor’s stealth and use of reverse shells make it a serious threat to organizations. As Earth Bluecrow improves its tactics, companies need stronger defenses. Quick detection, fast response, and proactive security are key to staying protected.













Leave A Comment