CODESYS has launched patches to handle as many as 11 safety flaws that, if efficiently exploited, may end in info disclosure and a denial-of-service (DoS) situation, amongst others.
The vulnerability is simple to exploit and these successful exploitation leads to data leakage and arbitrary code execution.
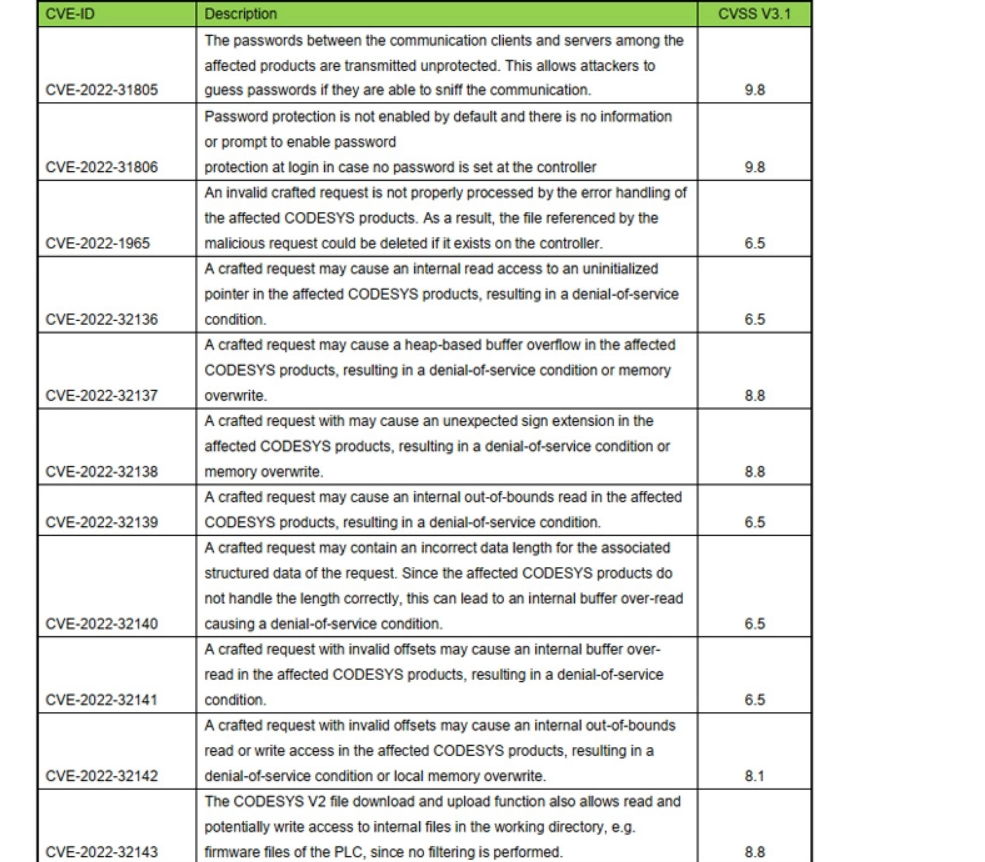
Chief among the many flaws are CVE-2022-31805 and CVE-2022-31806 (CVSS scores: 9.8). The flaw relate to the cleartext use of passwords used to authenticate earlier than finishing up operations on the PLCs .This fail to allow password safety by default within the CODESYS Management runtime system respectively.
Exploiting the weaknesses couldn’t solely enable a malicious actor to grab management of the goal PLC system, but additionally try to execute arbitrary code.
How these vulnerabilities can be exploited
An attacker does not need a username or password, having network access to the industrial controller is enough.
According to the researchers, the main cause of the vulnerabilities is insufficient verification of input data,. This may itself be caused by failure to comply with the secure development recommendations.
The most dangerous problems were revealed in the CODESYS V2.3 web server component used by CODESYS Web.
However .it’s recommended to “locate the affected products behind the security protection devices and perform a defense-in-depth strategy for network security.”
Below is the list of protection and recommendations recommended by the researchers:
- Try using secure VPN networks when remote access is required, and perform adequate access control and auditing.
- Pay attention to vendor’s security updates, and upgrade the affected products.
- Minimize the exposure of private communication ports of the affected devices and selectively close the affected ports such as 1200/1201/2455.
- recommending vendors who use CODESYS V2 Runtime to investigate themselves in time, and actively to fix and release the patched version of firmware.
- To eliminate the vulnerabilities, companies are advised to follow the recommendations in CODESYS official notices.













Leave A Comment