Cuttlefish is a recently discovered malware platform that has been active since at least July 2023. It specifically targets networking equipment such as enterprise-grade small office/home office routers.
The latest campaign has been ongoing from October 2023 to April 2024. Furthermore, 99% of the malware’s targets were located in Turkey, with over 600 unique IP addresses identified, primarily belonging to two telecom firms. Victims outside Turkey were clients of global satellite phone providers and a US-based data center.
The malware’s code overlaps with HiatusRAT, which targeted individuals interested in the People’s Republic of China.
However, this malware diverges in victimology and includes additional functionalities such as DNS and HTTP hijacking for connections to private IP space.
‘Cuttlefish’ Zero-Click Malware
Cuttlefish malware is primarily designed to steal authentication details from web requests, allowing threat actors to bypass anomalous sign-in-based analytics through stolen credentials.
To extract data from web requests, the threat actor establishes a proxy or VPN tunnel from the compromised networking equipment and utilizes stolen credentials to access targeted resources.
The initial access vector of this malware campaign remains unclear. However, upon exploitation, the threat actor deploys a bash script on the compromised host to transmit the details to the C2 server.
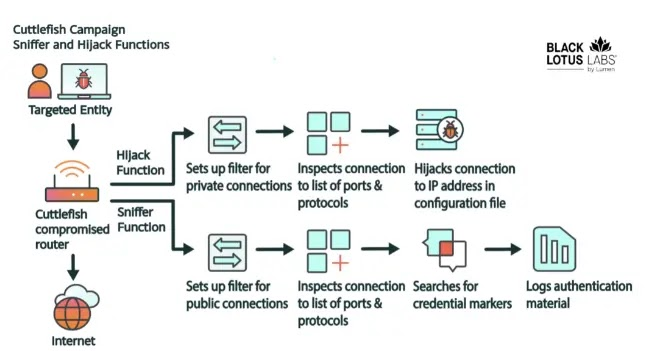
The bash script also downloads and executes Cuttlefish malware, which initiates a multi-step process to install a packet filter for inspecting all outbound connections. This includes details on specific ports, protocols, and destination IP addresses. All rules and configurations are specified in the configuration file sent to the C2 server.
The malware is instructed to hijack traffic to specific private IP addresses and sniff traffic to public IP addresses to steal credentials. Compromising networking equipment offers various avenues to manipulate routes, hijack connections, and employ sniffing to steal authentication and gain access to the cloud ecosystem with stolen credentials.
To elaborate, the malware consists of various files and functionalities including:
- Bash script files
- Primary payload, Cuttlefish
- Retrieval of rulesets
- Credential harvesting
- Logger and data transmission
- Hijack functionality
- VPN functionality
- Private proxy functionality
The bash script enumerates the device, collecting information like directory listings, /etc and /etc/config contents, running processes, active connections, and drive mounts. This data is compressed as a TAR file named “co.tmp.tar.gz” and uploaded to the C2 server.
Once exfiltrated, the TAR file is deleted, and the bash script downloads the trojan from the payload server, saving it in the /tmp directory as “.timezone.” The “.” prefix helps the threat actor escape the “ls” command.
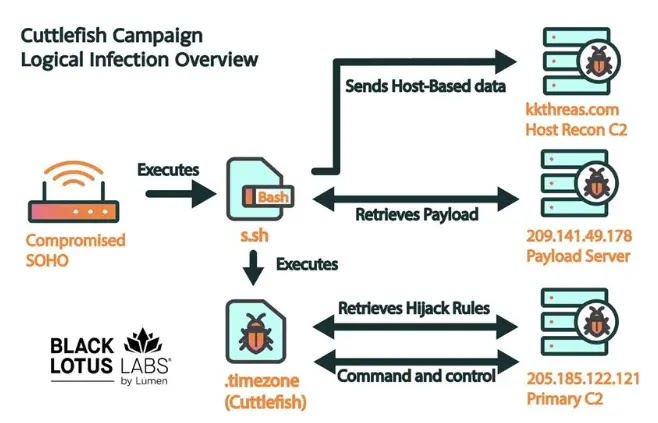
The primary payload, Cuttlefish, is executed, binding only to port 61235 to ensure a single instance runs. If another process uses the port, it displays an error message. It then checks for the “.timezone” file dropped earlier, attempting to execute it with the bash command “/tmp/.timezone -a -b 5000 -z -d.” In the latest version, “.timezone” is replaced with “.putin,” and multiple commands have been added to the malware.
If the file exists, the malware overwrites the uuid with its contents. The RuleSet retrieval function establishes a secure connection to the C2 server for downloading and updating the ruleset.
The payload output is saved to “/tmp/config.js” for parsing and updating parameters. After configuration, the malware spawns two threads: one for tracking heartbeat time and the other for monitoring traffic on selected interfaces.
The credential harvesting feature extracts credentials from web requests, while the VPN feature employs the “n2n” open-source project. In contrast, the hijacking function utilizes commands like http_hijack_heartime. The proxy function is built on the “socks_proxy” open-source project. Black Lotus Researchers have published a comprehensive report detailing the malware’s functionalities, files, and source code.
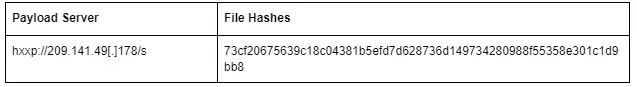
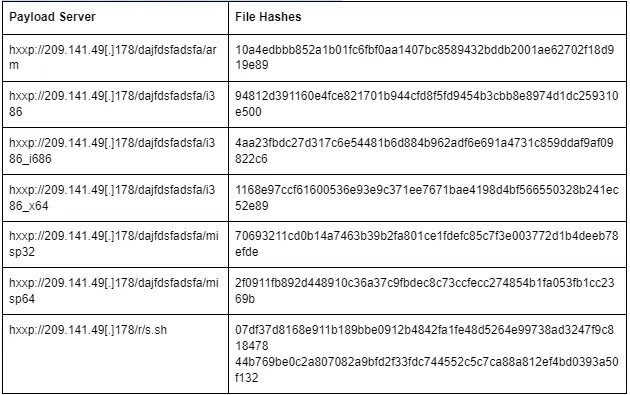
Indicators Of Compromise
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment