Researchers discovered REF4578, an intrusion set that exploits vulnerable drivers to disable EDRs for crypto mining and deploys the GHOSTENGINE malware.
GHOSTENGINE manages the machine’s modules, primarily using HTTP to download files from a configured domain, with a backup IP if the domain is unavailable. It also uses FTP with embedded credentials as a backup protocol.
GHOSTENGINE Malware
Elastic Security Labs reports that the REF4578 intrusion began on May 6, 2024, with a PE file named Tiworker.exe masquerading as the genuine Windows TiWorker.exe.
Telemetry recorded alarms indicating the use of a known vulnerable driver.
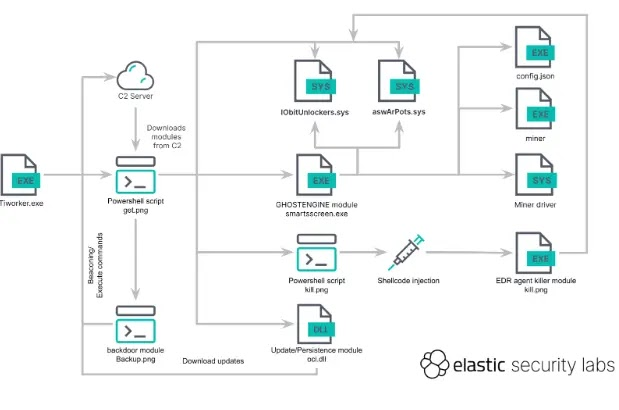
When executed, this file downloads and runs a PowerShell script that controls the entire intrusion process. Analysis shows it uses a hardcoded PowerShell command to fetch an obfuscated script called get.png, which then downloads additional tools, modules, and configurations from the attacker’s C2 server. The script attempts to disable Windows Defender, enable remote services, and clean Windows event log channels.
To establish persistence, get.png creates the OneDriveCloudSync, DefaultBrowserUpdate, and OneDriveCloudBackup scheduled tasks as SYSTEM.
GHOSTENGINE installs modules to check for software updates, build security tools, and create a backdoor. The smartscreen.exe module’s main function is to terminate EDR agent processes before setting up a cryptocurrency miner.
“The ultimate goal of the REF4578 intrusion set was to gain access to an environment and deploy a persistent Monero crypto miner, XMRig,” researchers said.
Recommendation
Therefore, it is crucial to prevent and detect the following early actions:
- Suspicious PowerShell execution
- Execution from unusual directories
- Privilege escalation to system integrity
- Deployment of vulnerable drivers and related kernel mode services
IOCS
| Observable | Type | Name | Reference |
|---|---|---|---|
2fe78941d74d35f721556697491a438bf3573094d7ac091b42e4f59ecbd25753 | SHA-256 | C:\Windows\Fonts\smartsscreen.exe | GHOSTENGINE EDR controller module |
4b5229b3250c8c08b98cb710d6c056144271de099a57ae09f5d2097fc41bd4f1 | SHA-256 | C:\Windows\System32\drivers\aswArPots.sys | Avast vulnerable driver |
2b33df9aff7cb99a782b252e8eb65ca49874a112986a1c49cd9971210597a8ae | SHA-256 | C:\Windows\System32\drivers\IObitUnlockers.sys | Iobit vulnerable driver |
3ced0552b9ecf3dfecd14cbcc3a0d246b10595d5048d7f0d4690e26ecccc1150 | SHA-256 | C:\Windows\System32\oci.dll | Update/Persistence module (64-bit) |
3b2724f3350cb5f017db361bd7aae49a8dbc6faa7506de6a4b8992ef3fd9d7ab | SHA-256 | C:\Windows\System32\oci.dll | Update/Persistence module (32-bit) |
35eb368c14ad25e3b1c58579ebaeae71bdd8ef7f9ccecfc00474aa066b32a03f | SHA-256 | C:\Windows\Fonts\taskhostw.exe | Miner client |
786591953336594473d171e269c3617d7449876993b508daa9b96eedc12ea1ca | SHA-256 | C:\Windows\Fonts\config.json | Miner configuration file |
11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5 | SHA-256 | C:\Windows\Fonts\WinRing0x64.sys | Miner driver |
aac7f8e174ba66d62620bd07613bac1947f996bb96b9627b42910a1db3d3e22b | SHA-256 | C:\ProgramData\Microsoft\DeviceSync\SystemSync\Tiworker.exe | Initial stager |
6f3e913c93887a58e64da5070d96dc34d3265f456034446be89167584a0b347e | SHA-256 | backup.png | GHOSTENGINE backdoor module |
7c242a08ee2dfd5da8a4c6bc86231985e2c26c7b9931ad0b3ea4723e49ceb1c1 | SHA-256 | get.png | GHOSTENGINE loader |
cc4384510576131c126db3caca027c5d159d032d33ef90ef30db0daa2a0c4104 | SHA-256 | kill.png | GHOSTENGINE EDR termination module |
download.yrnvtklot[.]com | domain | C2 server | |
111.90.158[.]40 | ipv4-addr | C2 server | |
ftp.yrnvtklot[.]com | domain | C2 server | |
93.95.225[.]137 | ipv4-addr | C2 server | |
online.yrnvtklot[.]com | domain | C2 server |













Leave A Comment