GitLab has issued security patches (16.11.1, 16.10.4, and 16.9.6) for both Community and Enterprise Editions, emphasizing the importance of upgrading to these versions to mitigate vulnerabilities.
Scheduled bi-monthly patch releases are complemented by ad-hoc critical patches for high-severity vulnerabilities. Vulnerability details are disclosed 30 days after patch release. For affected installations, immediate upgrade is advised across all deployment types, unless explicitly exempt.
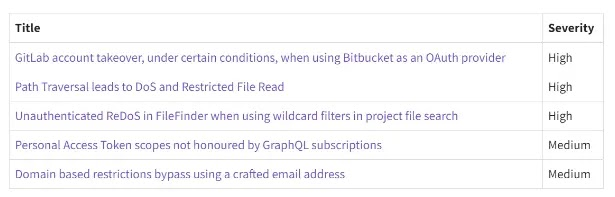
Several vulnerabilities demanding immediate attention were detected. In certain scenarios, an attacker could potentially hijack a GitLab account by utilizing Bitbucket for OAuth authentication (High severity).
GitLab versions preceding 16.9.6, 16.10.4, and 16.11.1 are susceptible to an account takeover via Bitbucket OAuth integration. An attacker with a Bitbucket account could potentially seize control of a connected GitLab account under certain conditions.
The critical issue (CVE-2024-4024) has been resolved in the latest GitLab releases, discovered internally by the GitLab security team.
An update concerning Bitbucket authentication is underway. Users are advised to sign in to GitLab with Bitbucket credentials before May 16th, 2024, to automatically relink accounts. After this date, manual relinking will be necessary.
Users with mismatched email addresses between GitLab and Bitbucket should log in using their GitLab username and password to re-link Bitbucket.
Versions prior to 16.9.6, 16.10.4, and 16.11.1 are vulnerable to two high-severity attacks. A path traversal flaw (CVE-2024-2434, CVSS: 8.5) enables unauthenticated attackers to potentially access restricted files and crash the application (DoS).
Additionally, a separate vulnerability (CVE-2024-2829, CVSS: 7.5) in project file search allows a specially crafted wildcard filter to trigger a denial-of-service attack.
Upgrading to the latest GitLab version is crucial to mitigate these risks.
Versions prior to 16.9.6, and certain subsequent versions, harbor two vulnerabilities. The first (CVE-2024-4006) arises from GraphQL subscriptions failing to adequately enforce Personal Access Token scopes, potentially granting unauthorized data access.
In the second (CVE-2024-1347), a meticulously crafted email address could circumvent domain-based restrictions on groups or instances, now resolved in the latest GitLab releases.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment