PaloAlto Threat Research Team Unit 42 identifies and confirm HoeflerText popups started delivering RAT malware to Google Chrome users
EITest campaign was delivering Spora & Mole ransomware’s but recently the campaign spreading the new RAT which targets google chrome users in the similar fashion.
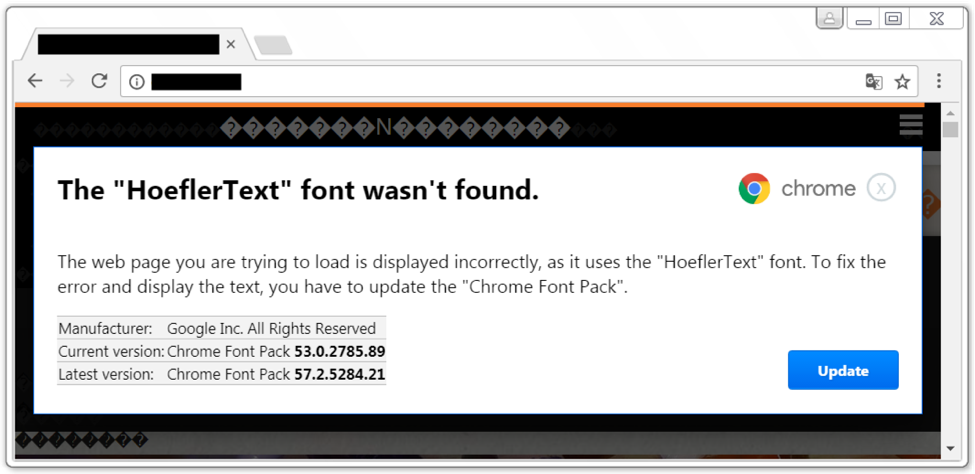
The variant is designed in a way:
- If the victim is using IE, Injected script leads to the fake anti-virus alert
- If Victim is using google Chrome it leads to HoeflerText popups which ask the user to download the Font and installs Net Support Manager RAT
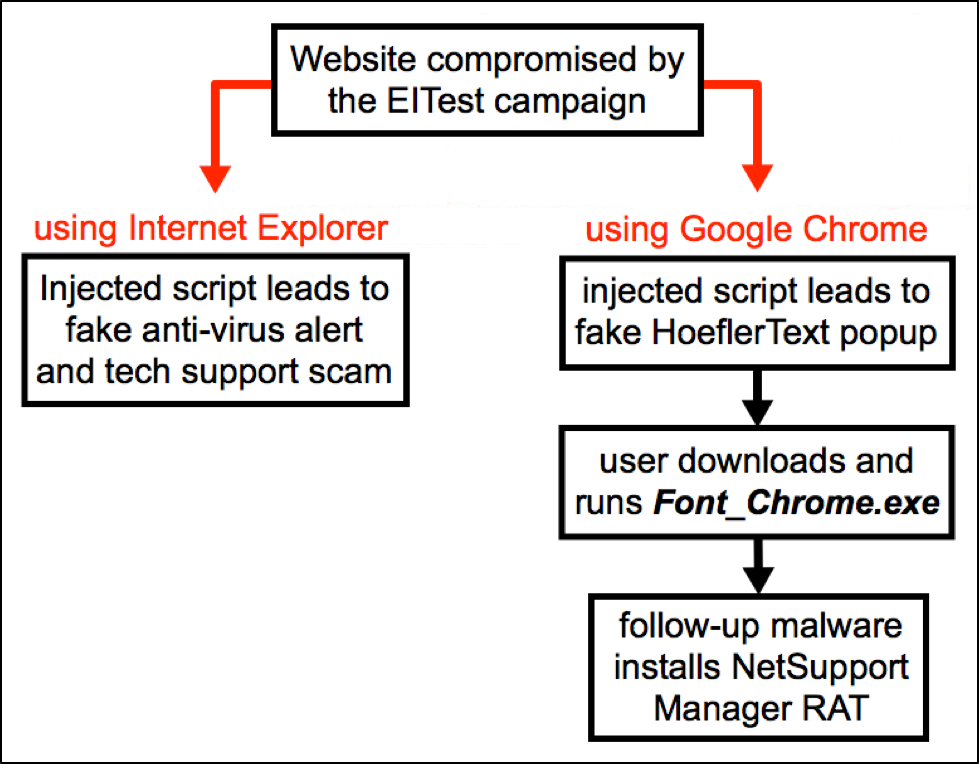
This is an ongoing threat and researchers are yet to identify why the campaign started spreading RAT rather spreading Ransomware’s. But RAT has the direct visibility into the victim’s network if it’s successful. So that hackers can play more with the compromised network. Thus might be the reason the campaign started sending RAT’s.
Also the research team released the Indicators of Compromise [IOC’s] which required immediate block in your environment
URL’s to BLOCK:
- hxxp://demo.ore.edu[.]pl/book1.php
- boss777[.]ga
- pudgenormpers[.]com
- invoktojenorm[.]com
- hxxp://94.242.198[.]167/fakeurl.htm
- hxxp://94.242.198[.]168/fakeurl.htm
Additional URL’s:
- 46.248.168[.]49 port 80 – demo.ore.edu[.]pl – GET /book1.php
- 51.15.9[.]99 port 80 – boss777[.]ga – GET /HELLO.exe
- 51.15.9[.]99 port 80 – boss777[.]ga – GET /joined1.exe
- 51.15.9[.]99 port 80 – boss777[.]ga – POST /JS/testpost.php
- DNS query for pudgenormpers[.]com, resolved to 94.242.198[.]167
- DNS query for invoktojenorm[.]com, resolved to 94.242.198[.]168
- 94.242.198[.]167 port 1488 – POST hxxp://94.242.198[.]167/fakeurl.htm
- 94.242.198[.]168 port 1488 – POST hxxp://94.242.198[.]167/fakeurl.htm
SHA 256 Value:
- 23579722efb0718204860c19a4833d20cb989d50a7c5ddd6039982cf5ca90280
- 8cbbb24a0c515923293e9ff53ea9967be7847c7f559c8b79b258d19da245e321
- 463bef675e8e100eb30aeb6de008b9d96e3af6c3d55b50cc8a4736d7a11143a0
- 8188732c8f9e15780bea49aced3ef26940a31c18cf618e2c51ae7f69ef53ea10
Files to Watch in your environment
- C:\Users\[username]\AppData\Roaming\AppleDesk1
- C:\Users\[username]\AppData\Roaming\AppleDesk2
If the above found in your environment deploy the incident management process / cyber investigation to identify your environment standing and don’t get compromise yourself, neither DON’T BE A VICTIM.













Leave A Comment