A bug that Google patched, could allow hackers to see your private documents.
Google Docs Bug:
Google Docs is an online word processor that lets you create and format documents and work with other people.
Earlier this year, Security researcher Sreeram KL, discovered this bug on July 9.
Moreover, Sreeram awarded $3133.70, as part of Google’s Vulnerability Reward Program.
In his report, he mentiond “I was able to hijack Google Docs screenshot of any document exploiting postmessage misconfiguration and a browser behavior.”
Working:
An option – “Send feedback” or “Help Docs improve“, many of Google’s products allow users to send feedback along with an option to include a screenshot.
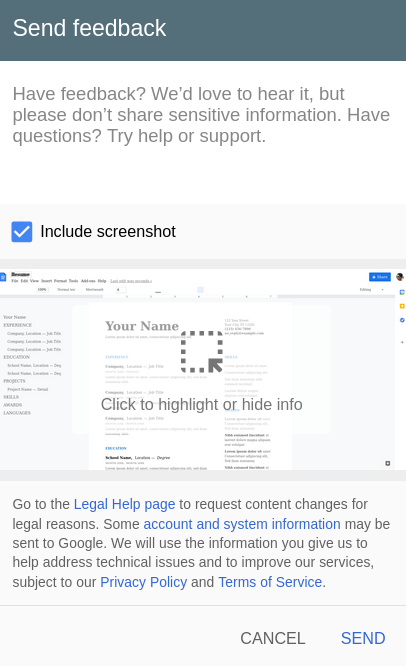
Screenshot — automatically loaded to highlight specific issues.
In addition, the feedback feature deployed on Google’s main website (“www.google.com”) and integrated into other domains via an iframe element, Instead of duplicating the same functionality across its services.

Whenever a screenshot of the Google Docs window is included, Google docs send RGB values of its every pixels to the main iframe www.google.com via postmessage.
However, which ultimately constructs the image and sends it back in Base64 encoded format.
These messages were passed to “feedback.googleusercontent.com,” thus allowing an attacker:
- to modify the frame to an arbitrary, external website,
- also, steal and hijack Google Docs screenshots — uploaded to Google’s servers.
Notably, the flaw stems from a lack of X-Frame-Options header in the Google Docs domain.
It is possible to change the target origin of the message and exploit the cross-origin communication between the page and the frame contained in it.
Importantly, the attack requires some form of user interaction — i.e. clicking the “Send feedback” button.
Attackers can exploit easily by:
- embedding a Google Docs file in an iFrame on a rogue website
- hijacking the feedback pop-up frame to redirect the contents to a domain of the attacker’s choice.
Security concerns raise when failing to provide a target origin during cross-origin communication, which exfiltrates data to a malicious site.
Follow Us on: Twitter, Instagram, Facebook to get latest security news!













Leave A Comment