Access for Hundreds of C-level (like CEO, CFO, etc) executives is sold for $100 to $1500 per account, depending on the company size and executive role.
Data Sold On Underground Forum:
A threat actor is currently selling passwords for the email accounts of hundreds of C-level executives at companies across the world.
Further ZDNet this week learned, The data is being sold on a closed-access underground forum for Russian-speaking hackers named Exploit.in

A source has agreed to contact the seller to obtain samples, has confirmed the validity of the data.
Moreover, obtained valid credentials for two high-profile accounts, the CEO of a US medium-sized software company and the CFO of an EU-based retail store chain.
Follow Us on: Twitter, Instagram, LinkedIn to get latest security news!
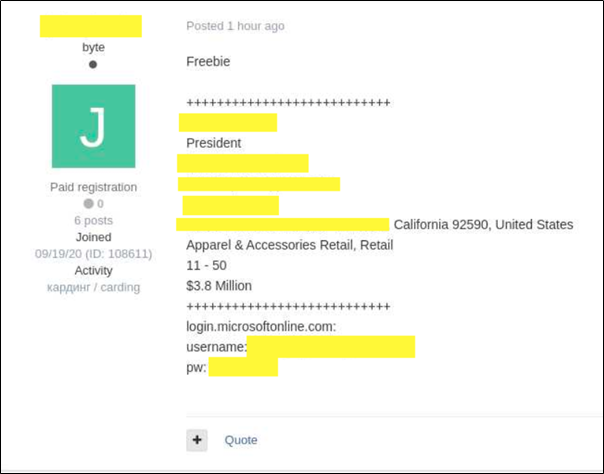
Sample Account Data:
The seller refused to share how he obtained the log-in credentials but said he had hundreds more to sell.
Above all, The threat actor is selling email and password combinations for Office 365 and Microsoft account of high-level executives occupying functions such as:
- CEO – chief executive officer
- COO – chief operating officer
- CFO – chief financial officer or chief financial controller
- CMO – chief marketing officer
- CTOs – chief technology officer
- President
- Vice president
- Executive Assistant
- Finance Manager
- Accountant
- Director
- Finance Director
- Financial Controller
- Accounts Payables
Importantly depending on the size of the company and role, the access to accounts sold for prices ranging from $100 to $1,500.
Info-Stealer — Trojan:
According to KELA, a threat intelligence firm, the same threat actor had previously expressed interest in buying “Azor logs” — Info-stealer Trojan.
However, Info-Stealer logs almost always contain usernames and passwords that the trojan extracts from browsers found installed on infected hosts.
In addition, KELA Product Manager Raveed Laeb told ZDNet “Compromised corporate email credentials can be valuable for cybercriminals, as they can be monetized in many different ways,”
Firstly, Using these credentials the attackers can perform the following:
- Manipulate employees into wiring them large sums of money
- As part of an extortion scheme, used in order to access sensitive information
- Moreover, to gain access to other internal systems
- on the other hand, to move laterally in the organization and conduct a network intrusion
In short, The easiest way of preventing hackers from monetizing any type of stolen credentials is to use two-step verification (2SV) or two-factor authentication (2FA) solution for your online accounts.













Leave A Comment