OUTLINE
The Emerging growth of the Digital Currencies also develops the need of protection from unforeseen hazards. The “LemonDuck” botnet, already in existence, is now targeting the Docker APIs for Crypto Currency mining. It is an anonymous mining operation that uses the proxy tools and disables the Alibaba Cloud Defense system to Stay under the hood while the job is getting done
HOW DOES LEMONDUCK MINES?
Since Docker is mainly used to run container workloads in the cloud, a misconfigured cloud instance can expose a Docker API to the internet. This exposed Docker is targeted by LemonDuck to get the initial Access and then run a malicious container in it by using the custom ENTRYPOINT to download a “core.png”, which acts as a prime by setting a Linux cronjob inside the container. Next, this cronjob downloads another disguised file “a.asp” which is originally a bash file. This a.asp is the actual payload that takes a few more steps, and proceeds to download and starts the mining operation after triggering the cronjob, such as

The Alibaba Cloud Defense System monitors the cloud instances for malicious contents once the agent is installed on a host or container. LemonDuck’s a.asp file has the capability to disable aliyun service thus evading the detection by the cloud provider.
Finally, this a.asp file downloads and runs XMRig as “xr” file that mines the cryptocurrency. Further, the configuration file used by XMRig indicates the use of a crypto mining proxy pool. [Proxy pools help in hiding the actual crypto wallet address where the contributions are made by current mining activity run by other groups.]
SSH – LATERAL MOVEMENT
LemonDuck skips mass scanning the public IP ranges for exploitable attack surface, but instead tries to move laterally by searching for Secure Shell (SSH) keys on filesystem. This is one of the reasons this campaign was not evident as other mining campaigns run by other groups. Once SSH keys are found, the attacker uses those to log in to the servers and run the malicious scripts as discussed earlier
SELF-SIGNED CERTIFICATIONS
With the image provided below, it is known that the domain has a self-signed certificate installed with a validation period of May 2021 to May 2022. This proves, the domain is currently in action.
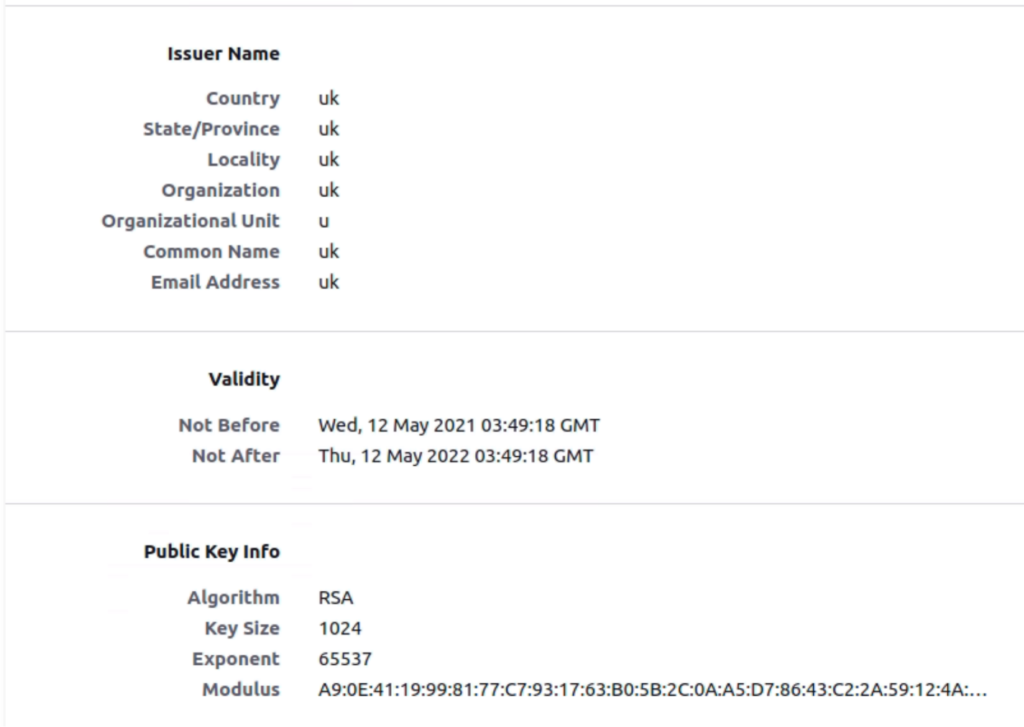
Attackers usually run a single campaign from a single Command & Control (C2) server, but intriguingly, In LemonDuck, there are multiple campaigns running that target the Windows as well as the Linux platform.
The domain – “t.m7n0y[.]com” associated with LemonDuck is analyzed and it is found that multiple campaigns are targeting Windows and Linux platforms simultaneously
The below image reveals the dropper files used in multiple campaigns.

RECOMMENDATIONS
Organizations needs to ensure that the Threat Intelligence Capabilities are Enriched / Updated to detect such attacks in their environment
If not, you can bind yourself with such Threat Intelligence Products to ensure, early detection and prevention could be performed automatically
Defer No Time, Delays have Dangerous Ends.
William Shakespeare




![Nifty[.]com Infrastructure Exploited in Phishing Attack](https://firsthackersnews.com/wp-content/uploads/2023/10/Phishing-Attacks_-Recognize-and-Avoid-Email-Phishing-1-500x383.jpg)








Leave A Comment