BlackBerry initially reported a new iOS LightSpy malware, but Huntress researchers discovered it as a macOS variant targeting Intel or Apple Silicon with Rosetta 2-enabled devices.
This led to media confusion, as Apple’s recent spyware alert likely referred to Pegasus spyware, and there’s no evidence of an iOS version in this finding. The researchers also found an Android version (WyrmSpy) but concentrated on the macOS variant in this paper, offering detection rules for further inquiry.
LightSpy Malware Attack
Analysis indicates that the LightSpy sample exclusively targets MacOS, as the binaries are compiled for the x86_64 architecture, incompatible with iPhones’ ARM architecture. This can be confirmed using the “file” command on both platforms.
Surprisingly, the implant structure remains consistent across both versions, utilizing a dropper to load subsequent dynamic libraries (dylibs) containing core malicious functionalities.
MacOS LightSpy appears more advanced than its iOS counterpart, employing a plugin manifest to store C2 information, enhancing flexibility and reducing detection.

While both versions display developer artifacts, macOS LightSpy indicates a more structured development process.
Identified developer machines (“mac” and “air”) suggest ongoing refinement by LightSpy’s creators.
The macOS variant begins with a dropper that verifies a running instance using a PID file and retrieves its configuration from the binary itself, containing server locations and encryption keys.
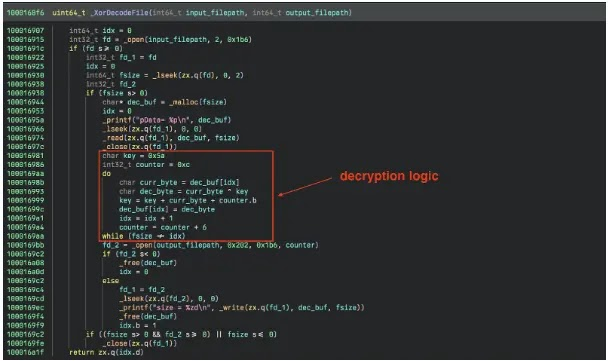
The dropper retrieves a manifest file containing details and encrypted hashes before downloading plugins. Once the core implant is downloaded, its integrity is verified against a server-side record. Both plugins and the core are XOR-encrypted with a rolling key, enabling analysts to examine plugin functionality by reversing this encryption method.
In the second stage of the implant process, plugin loading and utilization are managed. Here, the implant queries the device for details using the DeviceInformation class and gathers standard device information.
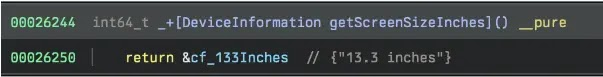
According to Huntress, the macOS version of this class omits phone-specific data such as IMEI and IMSI numbers. Additionally, certain tasks, like getScreenSizeInches, exhibit different behavior: while the iOS version provides device-specific dimensions, the macOS version returns a generic value.
Despite these differences, communication with the C2 server persists over WebSockets using the open-source SocketRocket library, maintaining functionalities like heartbeats, command exchange, and status updates.
The examined iOS implant downloads 10 additional plugins, each assigned a unique ID, to execute various malicious tasks. These include AudioRecorder for capturing audio, Browser for potential interaction with web browsers, and CameraShot for taking pictures.
Additionally, there are plugins with obfuscated names (identified by “aaa”) likely corresponding to functionalities such as basic system information gathering, software information gathering, location data retrieval, and potentially targeting specific iOS apps like WeChat, QQ, and Telegram.













Leave A Comment