Fake job offer — phishing campaigns delivering backdoor, targeting job professionals in LinkedIn.
LinkedIn Spear-Phishing
eSentire’s research team, the Threat Response Unit (TRU), discovered that hackers are spear-phishing victims with a malicious zip file using the job position listed on the target’s LinkedIn profile.
However, the sophisticated backdoor trojan is called “more_eggs“
In addition, more_eggs is a JavaScript backdoor. It attempts to connect to its C&C server and retrieve tasks to carry out,
For example,
“if the LinkedIn member’s job is listed as Senior Account Executive—International Freight the malicious zip file would be titled Senior Account Executive—International Freight position (note the “position” added to the end).”
Upon opening the job offer, the victim installing the fileless backdoor, more_eggs. Also, it installs additional malicious plugins and provide hands-on access to the victim’s computer.
Attack Target
According to TRU team, the target was a professional working in the healthcare technology industry.
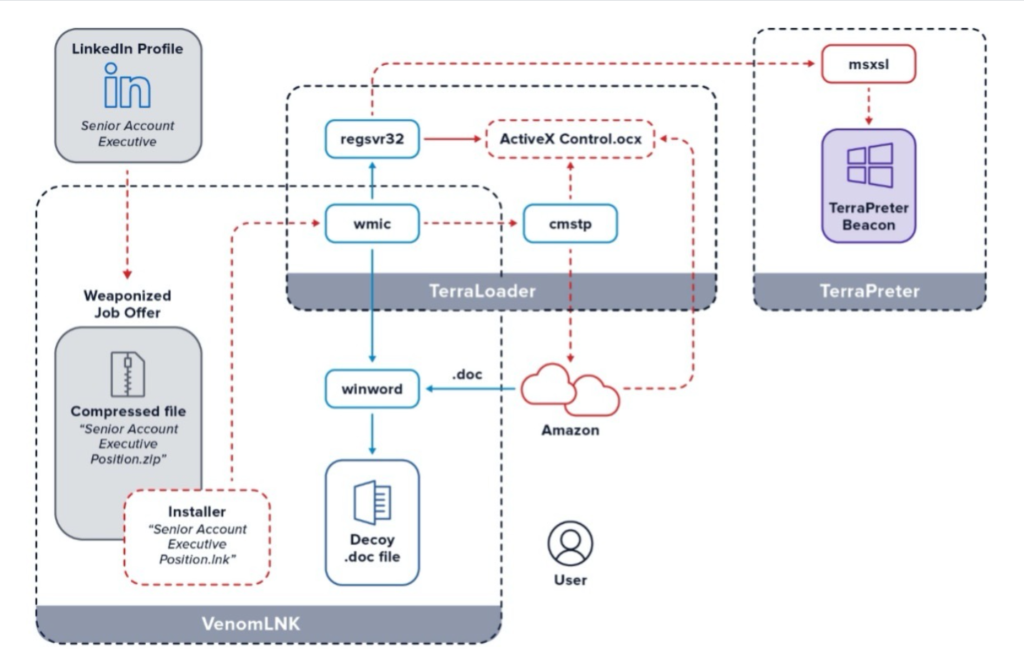
As initial stage, upon downloading and executing the alleged job file, the victim unwittingly executed VenomLNK.
Secondly, TerraLoader — VenomLNK enables the malware’s plugin loader which abuse Windows Management Instrumentation.
Which then hijacks legitimate Windows processes, cmstp and regsvr32.
After that, a decoy word document is presented to the victim — while TerraLoader is being initiated.
However, the purpose of the document to distract the victim from the ongoing background tasks of more_eggs.
TerraLoader then installs msxsl in the user’s roaming profile and loads the payload, TerraPreter, an ActiveX control (.ocx file) downloaded from Amazon Web Services.
Next, the TerraPreter connects to Command & Control server (C2)via the rogue copy of msxsl, which later might infect with ransomware, or addition malware or to exfiltrate victims data.
Security Recommendation
The researchers said “Since the COVID pandemic, unemployment rates have risen dramatically. It is a perfect time to take advantage of job seekers who are desperate to find employment”.
Further added, “Thus, a customized job lure is even more enticing during these troubled times.”
On the other hand, threat actors are also targeting various sectors including hospitals and healthcare organizations across the world.
Recommended to perform the below actions:
- Send the suspicious email to phishing@linkedin.com.
- Delete the email from your account
- Reset with strong password
- Never click links or open attachments unless you’re sure an email is legitimate.
Indicators Of Compromise
C2 beacon: d27qdop2sa027t.cloudfront[.]net
Download Server: ec2-13-58-146-177.us-east-2.compute.amazonaws[.]com
.zip hash: 776c355a89d32157857113a49e516e74
Ipconfig: cmd /v /c ipconfig /all > “C:\Users\\AppData\Local\Temp\64813.txt” 2>&1
regsvr32 /s /u “C:\Users\\AppData\Roaming\Microsoft\.ocx”
sh = new ActiveXObject(“Shell.Application”)
sh.ShellExecute(“msxsl.exe”, “.txt .txt”, “C:\Users\\AppData\Roaming\Microsoft\”, “”, 0)
evlinum js: C:\Users\\AppData\Roaming\Microsoft\57930.ocx
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment