RedEyes Hacking Group (aka APT37), a threat group known for its cyber espionage activities, has recently adopted a new tactic in its efforts to collect intelligence from targeted individuals.
This group is now using a sophisticated malware called “M2RAT,” which is specifically designed to evade detection by security software
M2RAT Malware :
The AhnLab Security Emergency Response Center (ASEC) just released a report showing how the RedEyes group is now using a new malware variant called “M2RAT” for their activities. This virus uses a shared memory segment to issue commands and extract data, leaving little residue on infected devices.
The attached file, when opened, directly exploits a known security vulnerability CVE-2017-8291 of the popular Hangul Office software found in South Korea. This exploit causes shellcode to run on the victim’s computer, which will then download and execute malicious code embedded in a JPEG image.
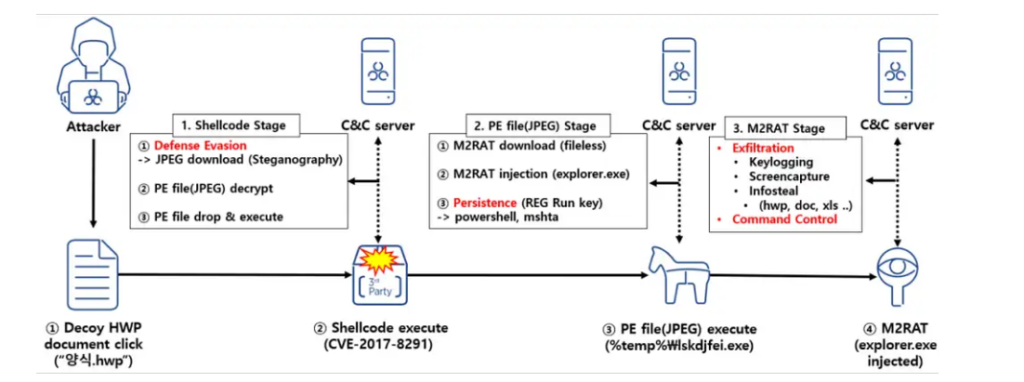
The M2RAT backdoor acts as a remote access trojan, recording user keystrokes, intercepting confidential data, executing commands on the system and capturing screenshots from the desktop.
The malware supports the following commands, which collect information from the infected device and then send it back to the C2 server for the attackers to review.
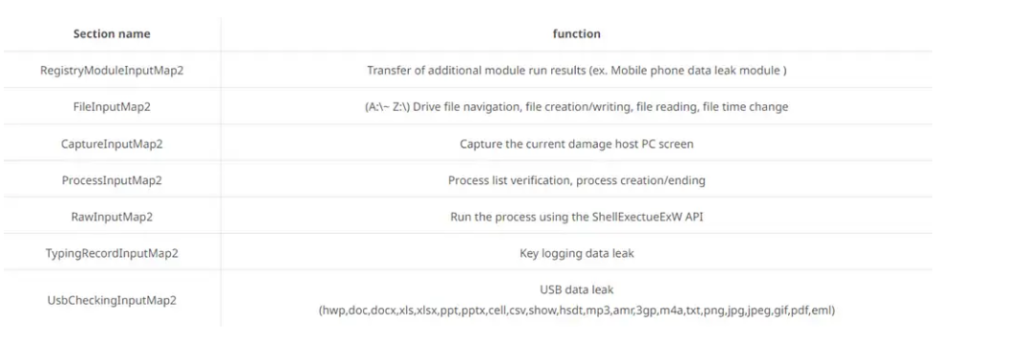
Upon detection of a portable device, a scan will be performed to identify any documents and voice recordings contained on the device. If it detects any file, it copies the detected files and later exfiltrates them to a server controlled by the attacker.
Recommendation
The most recent attacks that ASEC has noticed began in January 2023. It occurs when a hacking organization sends its intended victims phishing emails with malware attachments. An outdated EPS vulnerability is exploited as a result of the attachment (CVE-2017-8291). It is the widely popular South Korean Hangul word processor. The victim’s machine will execute the shell code as a result of the vulnerability.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment