A recently uncovered espionage threat actors are targeting the employees majoring in the mergers and acquisitions to facilitate a mass email collection from the victim’s environments. Also focusing on the large corporate data of transactions.
The Mandiant is constantly keeping tabs on the activities of the new group under the name of UNC3524. without many clues left behind, the threat actor is expected to be an existing group.
However, a few intrusions intersect with the Russian-based espionage, including both EWS impersonation and SPN credential addition.
Initial Compromise
After gaining initial access though unknown means. UNC3524, deploys an open-source SSH client-Server Software “QUIETEXIT” – a novel backdoor traced by Mandiant.
By targeting trusted systems within victim environments that do not support any type of security tooling, UNC3524 was able to remain undetected in victim environments for at least 18 months.
What is QUIETEXIT ?
The QUIETEXIT backdoor, works like a reversed SSH Client-Server. That is, once the backdoor establishes a connection, the threat actor can use any of the options available to an SSH client, including proxying traffic via SOCKS. QUIETEXIT has no persistence mechanism.
But, It was observed that UNC3524 install a run command as well as hijack legitimate application-specific start-up scripts to enable the backdoor to execute on system start-up.
The level of planning indicates that UNC3524 understands incident response processes and tried to make their C2 traffic appear as legitimate to anyone that might scroll through DNS or session logs.
Mandiant says all QUIETEXIT C2 domains observed by them used Dynamic DNS providers. Dynamic DNS allows for threat actors to update the DNS records for domains in a near seamless fashion. When the C2s where inactive.
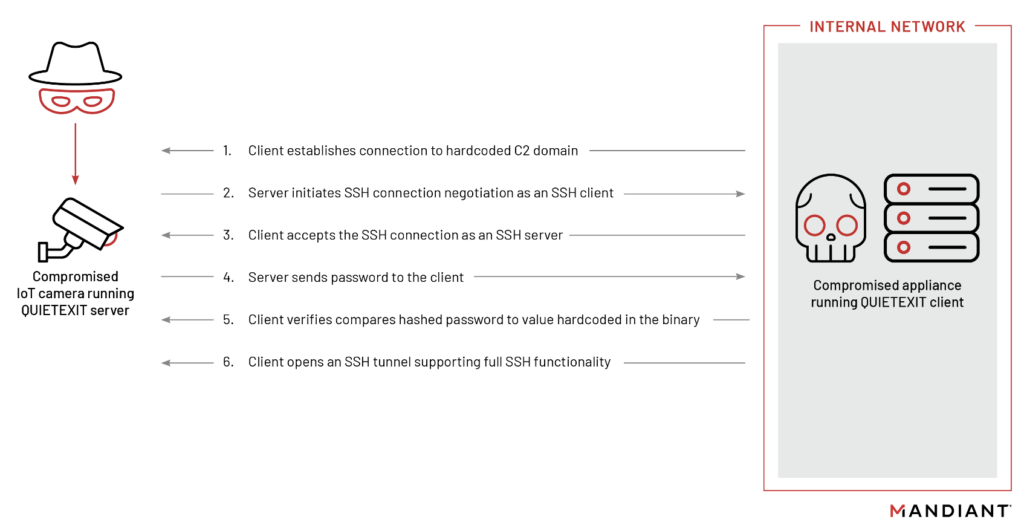
The Second Backdoor
In some cases, the threat actor has a second backdoor, as an alternate means to have access in the victim environments. The second backdoor is REGEORG, a web shell that creates a SOCKS proxy, going with UNC3524’s preference for a tunneling malware.
They also took care to name the file so that it blends in with the application running on the compromised server. This web shell is only used when QUIETEXIT backdoors stopped functioning and only to re-establish QUIETEXIT on another system in the network.
Lateral Movement
After establishing a foothold in the network UNC3524, demonstrated a very low malware footprint and instead relied on built-in Windows protocols. By tunneling over SOCKS through QUIETEXIT, the threat actor can execute tools to steal data from their own computer, leaving no traces of the tooling itself on victim computers.

To perform lateral movement to systems of interest, UNC3524 used a customized version, WMIEXEC. WMIEXEC uses Windows Management Instrumentation to establish a semi-interactive shell on a remote host.
Once UNC3524 successfully obtained privileged credentials to the victim’s mail environment, they began making Exchange Web Services (EWS) API requests to either the on-premises or online environment.
UNC3524’s use of compromised appliances makes host-based hunting and detection extremely difficult. he best opportunity for detection remains in network-based logging, specifically monitoring traffic at the layer 7 level. Finally, large volumes of network traffic originating from the “management” interfaces of appliances such as NAS arrays and load balancers should be investigated as suspicious as well.
“UNC3524 targets opaque network appliances because they are often the most unsecure and unmonitored systems in a victim environment. Organizations should take steps to inventory their devices that are on the network and do not support monitoring tools. Organizations can also take steps to use network access controls to limit or completely restrict egress traffic from these devices.” Mandiant said.
Indicators of Compromise
Malware : QUIETEXIT Dynamic DNS
- cloudns.asia
- dynu.net
- mywire.org
- webredirect.org
Malware : REGEORG GitHub version
MD5 – ba22992ce835dadcd06bff4ab7b162f9
SHA1 – 3d4dcc859c6ca7e5b36483ad84c9ceef34973f9a
SHA256 – 7b5e3c1c06d82b3e7309C258dfbd4bfcd476c8ffcb4cebda76146145502a5997













Leave A Comment