Microsoft addressed a critical vulnerability in its Power Platform after criticism for a delayed response. Tenable reported the vulnerability on March 30, 2023, and an official fix was issued in August. The vulnerability specifically impacts Power Platform Custom Connectors using Custom Code, allowing customers to write code for their custom connectors.
What is the potential impact of Microsoft Power Platform vulnerability?
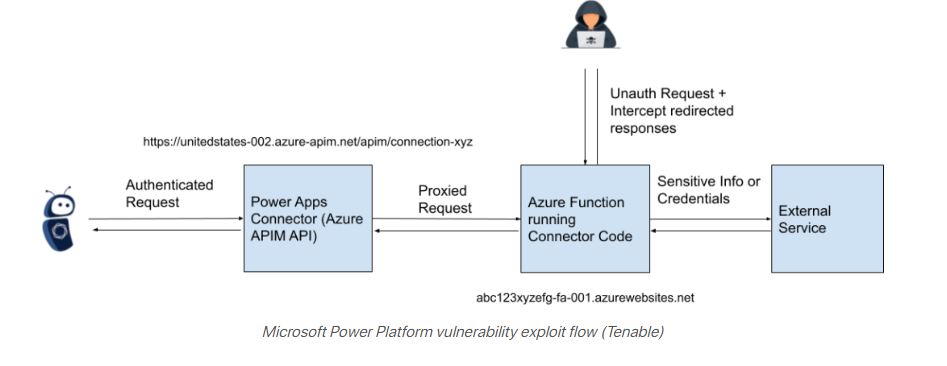
Microsoft warned that the vulnerability could potentially grant unauthorized access to Custom Code functions in Power Platform custom connectors, risking information disclosure if sensitive data or secrets were embedded in those functions.
Tenable also noted that the vulnerability might allow limited, unauthorized access to cross-tenant applications and sensitive data, including authentication secrets.
What causes the vulnerability in Microsoft Power Platform?
Tenable attributes the issue to insufficient access control on Azure Function hosts utilized in Microsoft’s Power Platform custom connectors.
The problem arises from unsecured API endpoints that allow requests to the Azure Function without requiring authentication, potentially enabling attackers to intercept OAuth client IDs and secrets used for communication with other services.
Recommendation
To protect against the Microsoft Power Platform vulnerability, consider implementing the following recommendations:
- Apply the official fix: Ensure that you have applied the official fix provided by Microsoft promptly to address the vulnerability.
- Keep software up-to-date: Regularly update the Microsoft Power Platform and all associated components to benefit from the latest security patches and enhancements.
- Monitor security advisories: Stay informed about security advisories and updates from Microsoft to be aware of potential vulnerabilities and their resolutions.
- Enforce strong access controls: Implement strict access controls for Azure Function hosts to prevent unauthorized access to sensitive functions and data.
- Enable authentication for API endpoints: Configure API endpoints to require proper authentication and authorization before processing requests.
- Regular security assessments: Conduct regular security assessments, code reviews, and penetration testing to identify and address potential vulnerabilities proactively.
- Implement network security measures: Utilize firewalls, intrusion detection and prevention systems, and other network security tools to monitor and protect against malicious activities.
- Educate users and developers: Raise awareness among users and developers about security best practices, potential risks, and how to report suspicious activities.
- Limit privileges: Limit the privileges assigned to users and applications, allowing access only to the necessary resources and functions.
- Implement multi-factor authentication (MFA): Enforce the use of MFA to add an additional layer of security and prevent unauthorized access.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment