Originally focused on Latin America, the banking trojan Mispadu has broadened its scope to Europe, employing phishing emails and malicious URLs to pilfer credentials. The attackers leverage these stolen credentials to conduct subsequent phishing campaigns, rendering Mispadu a notable threat.
Even with its geographic expansion, Mexico continues to be the primary target, witnessing thousands of stolen credentials since April 2023. The infection chain involves multiple stages, with the main alterations occurring in the initial phases.
Mispadu banking malware
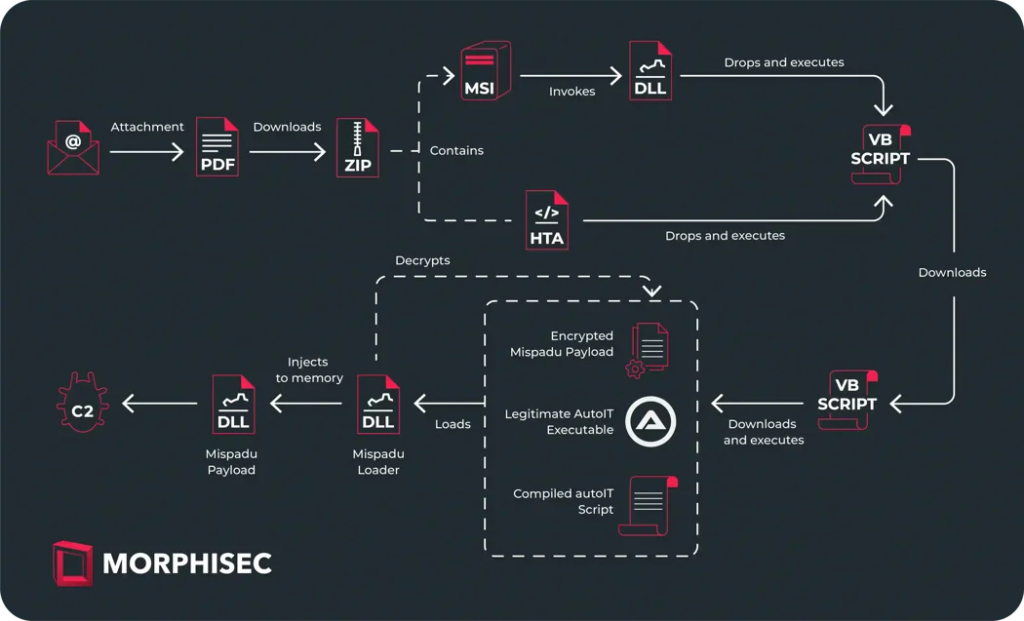
The phishing email masquerades as an invoice notification with a PDF attachment. Clicking a button within the PDF initiates the download of a ZIP file from a shortened URL, likely hosting the malicious payload, according to Morphisec.
VB Script Stages
The malware arrives in the form of either an MSI or HTA file, both of which ultimately execute a first-stage VB script. The MSI utilizes a custom DLL function to decrypt a concealed command, dropping the script, while the HTA employs a similar process.
To evade detection, the VB script operates in memory and verifies the User-Agent string for “(MSIE)” to ensure it is being executed by Internet Explorer.
If validated, it communicates with a command-and-control server to obtain the subsequent stage payload, which remains consistent regardless of the initial MSI or HTA infection method.
The extensively obfuscated script examines system data to detect virtual machines by comparing them to known virtual machine profiles, verifies language settings, and refrains from executing on machines named “JOHN-PC.” If these checks are successful, the script downloads three obfuscated files.
According to the Morphisec report, the first decrypts the final Mispadu payload, while the second decrypts an archive containing a compiled AutoIT script. This script, when executed by a third downloaded and decrypted legitimate AutoIT executable, loads a DLL that decrypts and injects the final Mispadu payload into memory.
The decompiled AutoIT script snippet injects malicious code by initially loading a DLL containing decryption logic. It proceeds to decrypt a payload previously downloaded by a VB script, before calling an exported function from the DLL.
The decrypted payload, presumably malware, is injected into a legitimate Windows process, such as attrib.exe or RegSvcs.exe. This camouflages the malicious code, increasing its difficulty to detect.
Mispadu’s ultimate payload employs genuine tools, such as WebBrowserPassView and MailPassView, to pilfer passwords from web browsers and email clients.
By actively monitoring user activity and seeking out specific strings tied to finance and email applications, it can target over 200 different services for credential theft. Stolen data is uploaded to a command-and-control server (C2) in two parts: firstly, email client credentials and browser passwords, and secondly, a compilation of harvested email addresses. These are likely utilized to fuel subsequent phishing attacks.
An attacker uses two C2 servers:
One server is dedicated to delivering initial attack payloads, while another is utilized for credential theft. The former constantly changes, whereas the latter remains consistent across campaigns.
Examination of stolen credentials unveils a persistent attack since April 2023, with over 60,000 files presently stored on the exfiltration server.













Leave A Comment