In South Korea, attackers distribute malware disguised as cracked software, including RATs and crypto miners, and register themselves with the Task Scheduler for persistence. Even after initial removal, the Task Scheduler triggers PowerShell commands to install new variants, persisting as the commands continuously change, leaving unpatched systems vulnerable to information theft, proxy abuse, and cryptocurrency mining.
Malicious actors are using file-sharing platforms to distribute malware disguised as cracked MS Office. During infection, the malware retrieves the download URL and target platform, potentially enabling tailored attacks and evasion of detection.
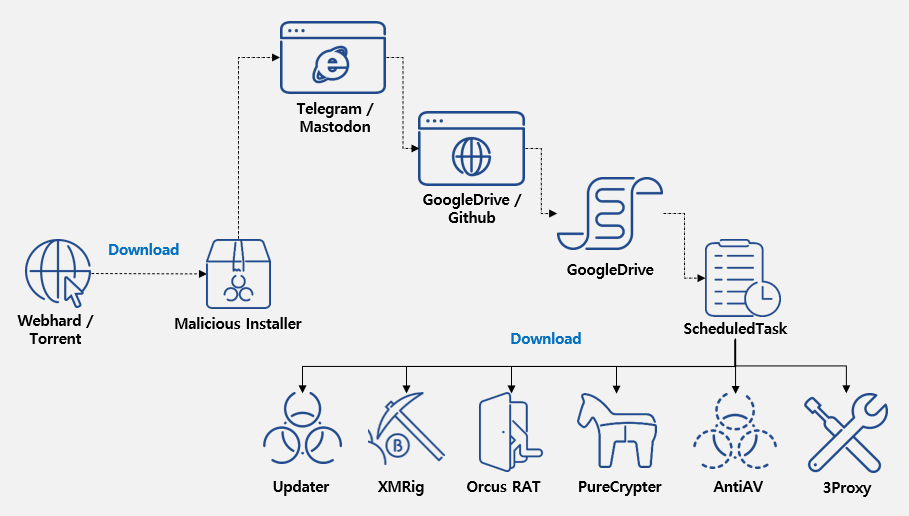
Newer versions feature two Telegram URLs and a Mastodon URL, each linked to a string associated with a Google Drive or GitHub URL.
The threat actor conceals malicious PowerShell commands within these cloud storage locations, employing Base64 encoding for further obfuscation. Once executed, these commands install additional malware strains.
The updater malware, “software_reporter_tool.exe,” uses a PowerShell script for downloading and maintaining persistence.
It creates a malicious executable at “C:\ProgramData\KB5026372.exe” and utilizes a compromised 7zip installation (“C:\ProgramData\Google\7z.exe”) to decompress a password-protected archive from GitHub or Google Drive (password: “x”), employing tactics mirroring those of a previous campaign.
Furthermore, the updater registers with the Task Scheduler for uninterrupted operation post-reboot, with the scheduled task initiating the PowerShell script for ongoing updates and possible malware installation.
The attackers deployed Orcus RAT and XMRig on the compromised system. Orcus RAT can steal information via keylogging, webcam, and screenshot capture, while XMRig mines cryptocurrency.
XMRig is set to pause mining during resource-intensive tasks and terminate processes that compete for resources, like security software installers. Meanwhile, 3Proxy converts the infected machine into a proxy server by adding a firewall rule and injecting itself into a legitimate process.
ASEC reports that PureCrypter downloads and executes additional payloads, while AntiAV malware disrupts security products by altering their configuration files.
Attackers distribute malware camouflaged as popular Korean software (Windows, MS Office, Hangul) via file-sharing platforms. The malware evades detection with regular updates and employs the Task Scheduler for persistence, resulting in recurrent infections even after removal.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment