
Attackers got an eye on the Victims O365 credentials in real-time as they enter their credentials into the phishing page, by using Authentication API’s.
Authentication API:
The processes of certifying the identity of users trying to access resources on the server and this is what is known as API authentication.
Authentication APIs are used by apps and services running on the users’ behalf to access their data. Office 365 requires app registrations to use APIs – but registrations require only an email address, making them seamless for attackers to leverage. Some additional configuration for the app also requires users to specify a website to “receive” authentication info.
The Phishing Email:
On Friday, a senior executive of an International firm received a phishing email with the statement in the Email body – “Find enclosed Payment Remittance Report’ as of 7/11/2020 2:53:14 a.m. Thank you for your business!” and points to an attachment, which looks like a text file.
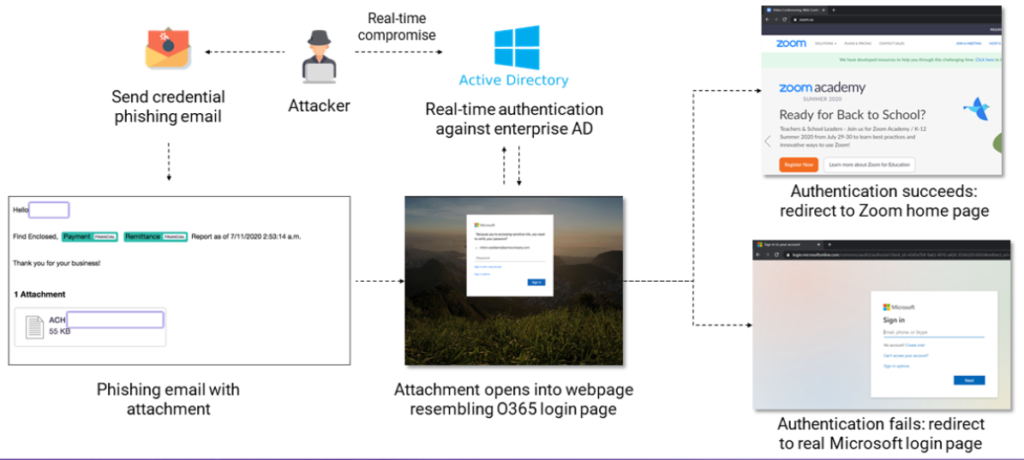
On opening the attachment, it launches a web page looks like legitimate Office 365 login page.
Researchers at Armorblox, a company protecting against targeted email attacks, analyzed the phishing attempt and noticed that the hackers verified the credentials immediately after getting them using Office 365 APIs.
“Our threat researchers verified the real-time nature of the site by updating the script with a test login and a dummy password and saw a failed login attempt from Provo, Utah in the Azure Active Directory Sign-In portal. As expected, the IP address (162.241.120.106) that attempted the sign-in is the same endpoint the phishing script sends the credentials” – Armorblox.
On further investigation:
- The Email has been sent from amazonses.com, the Amazon Simple Email Service. The DKIM and SPF checks have passed – i.e. the sender IP address matches amazonses.com.
- If authentication is successful, the user is redirected to zoom.com.
- If authentication fails, the user is redirected to login.microsoftonline.com. This could be a way to hide the phishing attack as just another failed sign-on attempt at the Office 365 portal.
- If the entered password text is empty or too short, the user is forced to retry.
In their blog post today, ArmorBlox says that checking the validity of the logins for AD authentication allows the attacker to adapt their next step; and if successful, they can compromise the account before any remediation action, establishing a foothold that could make cleaning operations more difficult.
Recommendations:
Security Awareness is the key to destroy any kind of targeted phishing attack combined with continuous phishing email protection on your exchange and O365 email suites.








Hi folks, just came across your posts, really like your works!
helpful site
I seriously love your site.. Pleasant colors & theme.
Did you create this website yourself? Please reply back as I’m attempting to create
my very own site and would love to learn where you got this from or what the theme is named.
Many thanks!
Hi, I do believe this is a great website. I stumbled upon it ;
) I am going to return once again since I bookmarked it.
Money and freedom is the best way to change, may you be rich and continue to help others.