
The OracleIV botnet malware employs various strategies, with a central emphasis on executing DDoS attacks through floods utilizing UDP and SSL protocols.
OracleIV DDoS Botnet Malware Targets Docker Engine
Cado Security Labs’ cybersecurity researchers have discovered a recently identified DDoS (Distributed Denial of Service) botnet malware called OracleIV, designed to exploit publicly accessible Docker Engine API instances.
As part of a probe, researchers uncovered a malicious campaign exploiting misconfigurations in Docker containers to distribute Python malware compiled as an ELF executable.
Lately, cybercriminals are increasingly targeting Docker Engine APIs, taking advantage of their popularity amid the rising adoption of microservices architectures. These hackers exploit unintentional Docker Engine API exposure, frequently scanning vulnerable environments to deploy malicious payloads for malicious purposes.
With the OracleIV DDoS botnet malware, attackers commence access by initiating an HTTP POST request to the Docker API, targeting the /images/create endpoint.
This request triggers a docker pull command, fetching a particular icon from Dockerhub. Subsequently, once the malicious image is obtained, a container is launched to execute actions aligning with the attacker’s objectives.
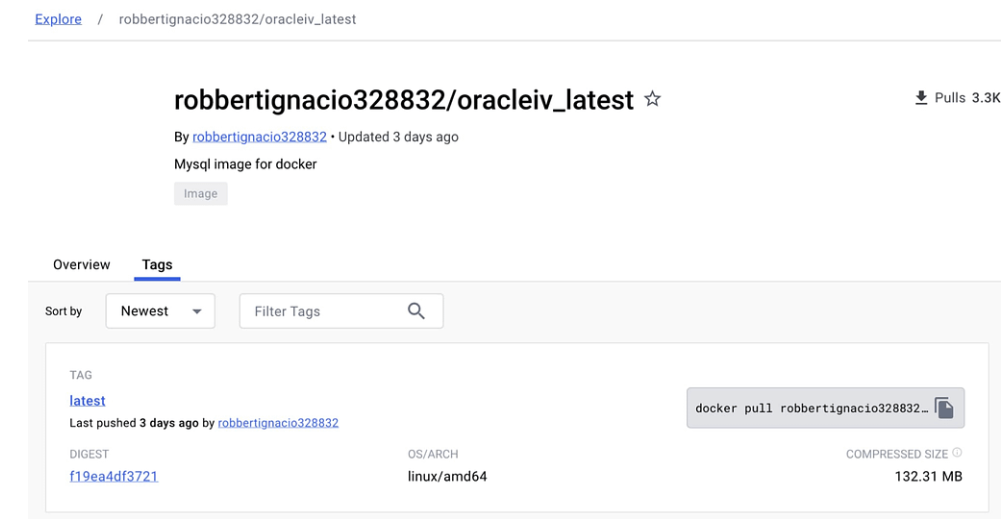
Researchers from Cado Security identified an active Dockerhub page hosting an image labeled “oracleiv_latest,” uploaded by the user “robbertignacio328832.” Despite its innocuous description as a “MySQL image for Docker,” the image harbored a concealed threat—specifically, a malicious payload named “oracle.sh.” This ELF executable functions as a DDoS bot agent. Upon deeper examination, additional commands were uncovered, indicating the retrieval of XMRig and a miner configuration file.
A static analysis of the executable unveiled a potent 64-bit ELF compiled with Cython, affirming the Python code origin of the OracleIV malware. Despite its brevity, the malware’s code incorporates multiple functions pertaining to diverse DDoS methods.
The bot establishes a connection to a Command and Control server (C2), utilizing basic authentication with a hardcoded password. Cado Security Labs observed the botnet’s actions, documenting DDoS attacks on diverse targets through UDP and SSL-based floods.
C2 commands for initiating DDoS attacks adhere to a distinct format, outlining the attack type, target IP/domain, attack duration, rate, and target port.
Although OracleIV doesn’t target the supply chain, it underscores the persistent threat posed by misconfigured Docker Engine API setups. The flexibility of containerization enables hackers to consistently deploy malicious payloads on Docker hosts.
While Cado Security has notified Docker about the malicious user, users are advised to conduct regular evaluations of images obtained from Dockerhub, underscoring the importance of remaining vigilant against potential malicious code.
In summary, the OracleIV campaign underscores the significance of fortifying online services and adopting robust network defenses. Users of Docker and comparable services are urged to routinely assess their vulnerability and implement essential precautions to guard against potential cyber threats.
Indicators of Compromise (IoCs)
| Filename | SHA256 |
| oracle.sh (embedded in container) | 5a76c55342173cbce7d1638caf29ff0cfa5a9b2253db9853e881b129fded59fb |
| xmrig (embedded in container) | 20a0864cb7dac55c184bd86e45a6e0acbd4bb19aa29840b824d369de710b6152 |
| config.json (embedded in container) | 776c6ef3e9e74719948bdc15067f3ea77a0a1eb52319ca1678d871d280ab395c |
| IP Addresses |
| 46[.]166[.]185[.]231 |
| Docker Image |
| robbertignacio328832/oracleiv_latest:lates |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




