
Microsoft has discovered recent activity that links the Raspberry Robin worm to human-operated ransomware attacks.
The experts noticed that threat actors tracked as DEV-0950 used Clop ransomware to encrypt the network of organizations previously infected with the worm.
Raspberry Robin is a worm that spreads over an external drive. After initial infection, it downloads its payload through msiexec.exe from QNAP cloud accounts, executes its code through rundll32.exe, and establishes a command and control (C2) channel through TOR connections.
The DEV-0950 attacks led to the deployment of the Cobalt Strike beacon. In some cases, the attackers delivered the Truebot malware between the Raspberry Robin infection and the Cobalt Strike deployment.
DEV-0206 is an access broker tracked by Microsoft, which uses malvertising campaigns to compromise networks worldwide.
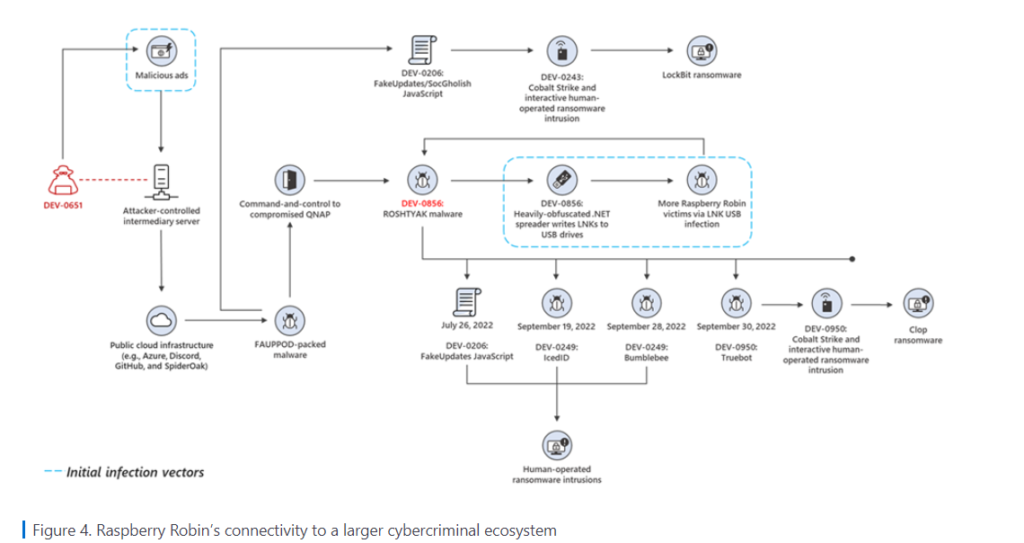
However Microsoft researchers says “DEV-0950 traditionally uses phishing to acquire the majority of their victims, so this notable shift to using Raspberry Robin enables them to deliver payloads to existing infections and move their campaigns more quickly to ransomware stages,”
The Raspberry Robin malware was first spotted in September 2021, the experts observed Raspberry Robin targeting organizations in the technology and manufacturing industries. Initial access is typically through infected removable drives, often USB devices.
The malware uses cmd.exe to read and execute a file stored on the infected external drive, it leverages msiexec.exe for external network communication to a rogue domain used as C2 to download and install a DLL library file.
Microsoft Defender have provided few mitigations to reduce the impact of threat.
Indicators of compromise (IOCs)
d1224c08da923517d65c164932ef8d931633e5376f74bf0655b72d559cc32fd2
0b214297e87360b3b7f6d687bdd7802992bc0e89b170d53bf403e536e07e396e
f18a54ba72df1a17daf21b519ffeee8463cfc81c194a8759a698709f1c9a3e87
0c435aadaa3c42a71ad8ff80781def4c8ce085f960d75f15b6fee8df78b2ac38
hxxps://codeload[.]github[.]com/downloader2607/download64_12/zip/refs/heads/main
hxxps://spideroak[.]com/storage/OVPXG4DJMRSXE33BNNPWC5LUN5PTSMRTGAZTG/shared/5392194-1-1040/Setup_64_1.zip?b6755c86e52ceecf8d806bf814690691
hxxps://dsfdsfgb[.]azureedge[.]net/332_332/universupdatepluginx84.zip
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




