Operators of the StrRAT and Ratty distant entry trojans (RAT) are operating a brand new marketing campaign utilizing polyglot MSI/JAR and CAB/JAR information to evade detection from safety instruments.
What is polyglot files?
Polyglots, in a security context, are files that are a valid form of multiple different file types. Polyglot files are often used to bypass protection based on file types.
RAT Malware Campaign
One notable case that has been employed since 2018, which can also be what Deep Intuition noticed within the newest RAT distribution marketing campaign, is the mixture of JAR and MSI codecs right into a single file.
JAR information are archives recognized as such by a file at their finish, whereas in MSI, the file sort identifier is a “magic header” in the beginning of the file, so menace actors can simply mix the 2 codecs right into a single file.
The polyglots used on this marketing campaign are unfold by Sendgrid and URL shortening companies like Cutt.ly and Rebrand.ly, whereas the fetched StrRAT and Ratty payloads are saved in Discord.
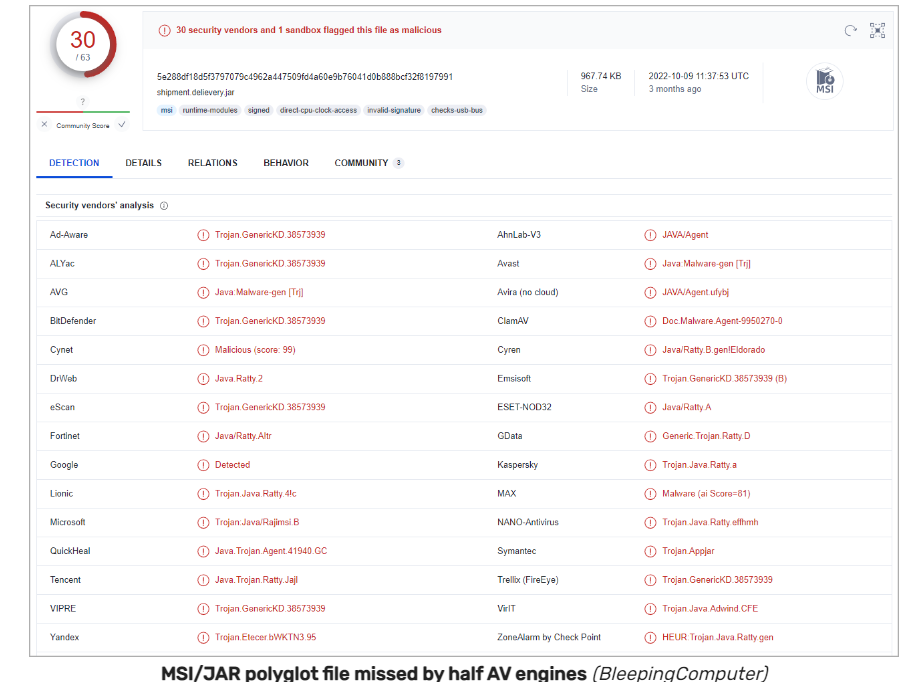
By way of detection, the CAB/JAR polyglots return six positives out of 59 AV engines on Virus Whole, whereas 30 safety distributors determine the MSI/JAR polyglots. Therefore, the detection charge ranges between 10% and 50%.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment