
In the course of a security assessment of its game development studios, Microsoft identified four vulnerabilities in Perforce Helix Core Server. These vulnerabilities have the potential to be exploited remotely by unauthenticated attackers, leading to Denial-of-Service (DoS) or, in some cases, granting an attacker full control of a system.
The Perforce Helix Core Server, commonly referred to as ‘Perforce Server,’ functions as a widely adopted source code management platform employed across various industries, including gaming, government, military, technology, and retail.
Microsoft disclosed vulnerabilities to Perforce in late August, prompting an investigation that led to the reservation of CVE IDs by late October. Perforce subsequently released patches addressing the four vulnerabilities in early November 2023.
Details of Perforce Server Vulnerabilities (CVE-2023-35767, CVE-2023-45319, CVE-2023-5759, and CVE-2023-45849)
Critical vulnerability CVE-2023-45849 (CVSS score 9.8) allows unauthenticated attackers to execute code as LocalSystem on Windows OS. This highly privileged account provides access to local resources, system files, and registry settings.
The flaw arises from mishandling the user-bgtask RPC command by the Perforce Server, which, in its default configuration, permits remote execution of commands, including PowerShell scripts, by unauthenticated attackers.
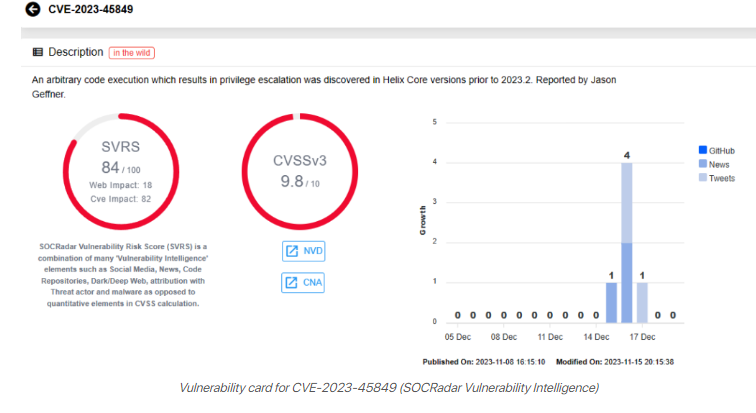
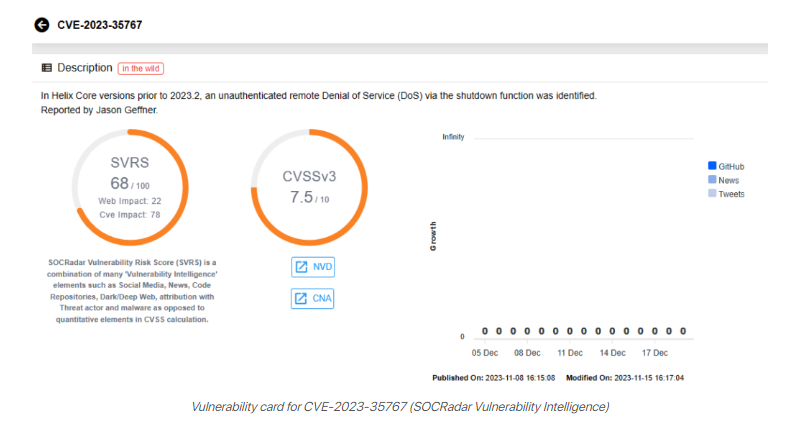
The remaining three vulnerabilities, with CVSS scores of 7.5 each, can lead to Denial-of-Service (DoS) attacks:
CVE-2023-35767 and CVE-2023-45319 permit unauthenticated attackers to initiate DoS via remote commands. The final vulnerability, CVE-2023-5759, is exploitable through RPC header manipulation.
No instances of these vulnerabilities being exploited have been identified by Microsoft. However, vigilance is crucial, especially for the critical vulnerability (CVE-2023-45849).
Exploitation of this flaw can lead to the installation of backdoors, unauthorized access to sensitive information, alterations to system settings, and potential complete control of a system running a vulnerable Perforce Server version.
Additionally, attackers could pivot to connected infrastructure, extending the potential impact of CVE-2023-45849 beyond the vulnerable component and posing a risk to software supply chains.
How to Secure Perforce Server Against the Vulnerabilities?
While Microsoft has not identified any ongoing exploitation attempts, users are strongly advised to update their Perforce Server to version 2023.1/2513900 to mitigate the risk of potential exploitation.
Microsoft also recommends adhering to Perforce’s guidance and adopting security measures, including:
- Regularly monitoring and applying patches for third-party software.
- Utilizing a VPN and/or an IP allow-list to restrict communication with your Perforce Server.
- Issuing TLS certificates to verified Perforce users and deploying a TLS termination proxy in front of the Perforce Server to validate client TLS certificates before allowing connections.
- Logging all access to your Perforce instance, both through network appliances and the server itself.
- Configuring alert systems to promptly notify IT administrators and the security team in case of process crashes.
- Employing network segmentation to limit the potential for attackers to pivot within your network.




