The digital landscape is witnessing a rise in sophisticated ransomware attacks, specifically remote encryption attacks. While the technology itself is not novel, it resembles a YouTube video uploaded a decade ago that is currently gaining recommendations. This article delves into the intricacies, evolution, and effective countermeasures against these attacks.
WHAT ARE REMOTE ENCRYPTION ATTACKS?
Remote encryption attacks involve unauthorized access to a system or network, where the attacker employs encryption techniques to encrypt files or data remotely. The aim is often to render the victim’s data inaccessible, holding it hostage until a ransom is paid. These attacks can be carried out through various vectors, including phishing emails, malicious links, or exploiting vulnerabilities in software or systems.
Once the attacker gains control, they encrypt critical files, demanding payment for the decryption key. Effective cybersecurity measures, such as regular software updates, employee training, and robust access controls, are crucial to mitigate the risk of remote encryption attacks.
Attackers are adopting the remote encryption model, using a compromised device to encrypt data on other devices within the same network. This method stands out as it can easily bypass common security solutions by leveraging a device not under their control.
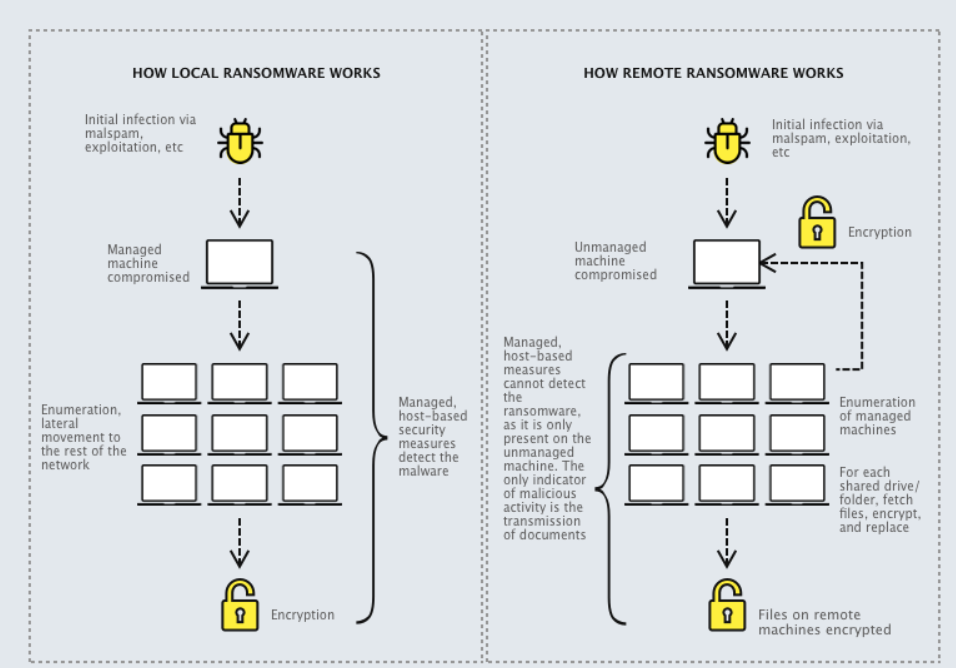
It’s commonplace for employees to access their workstations remotely from home. This situation presents a significant advantage for hackers as home computers or laptops are often not monitored by EDR/XDR or other security solutions.
Exploiting this vulnerability, adversaries can run malware on these devices, encrypting data within the corporate network while evading detection. To encrypt additional files, they simply seek out another remote connection, compromise the target system, and repeat the process.
The report indicates that approximately 60% of ransomware attacks employ remote encryption, with 80% of compromises originating from unmanaged devices. Notably, ransomware families like Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal extensively use this technique. It’s worth noting that this technology is not novel, as evidenced by CryptoLocker in 2013, which specifically targeted network shares.
The challenges in combating ransomware include non-traditional programming languages, the ransomware-as-a-service (RaaS) model, and targeting systems beyond Windows. Moreover, attacks are often launched outside regular hours, complicating detection and incident response efforts.
ANTI-RANSOMWARE METHODS
- Regular Backups:
- Maintain frequent and secure backups of critical data to facilitate quick recovery in case of a ransomware attack.
- Security Awareness Training:
- Educate employees on recognizing phishing emails and avoiding clicking on suspicious links or unknown attachments.
- Patch and Update Systems:
- Keep operating systems, software, and applications updated with the latest security patches to address vulnerabilities.
- Network Segmentation:
- Implement network segmentation to restrict the lateral movement of ransomware within the infrastructure.
- Endpoint Protection:
- Deploy robust endpoint security solutions with anti-malware and advanced threat detection capabilities.
- Email Security:
- Utilize advanced email security solutions to filter out phishing emails and malicious attachments.
- Multi-Factor Authentication (MFA):
- Implement MFA to enhance access security and mitigate the risk of unauthorized access.
- Incident Response Plan:
- Develop and regularly test an incident response plan for a swift and effective response to ransomware incidents.
- Application Whitelisting:
- Use application whitelisting to allow only approved applications, preventing the execution of unauthorized programs.
- Ransomware Decryption Tools:
- Stay informed about available decryption tools provided by security vendors to recover files without paying ransom.













Leave A Comment