To steal data from victims and update itself to perform additional malicious activities — Telegram exploited by Remote Access Trojan
ToxicEye Trojan Exploits Telegram
Operators of a new Remote Access Trojan (RAT) are exploiting the Telegram service to maintain control of their malware.
Telegram is a communications channel and instant messaging service used by over 500 million monthly active users, where criminals are increasingly using Telegram for malware control, because it offers several advantages compared to conventional web-based malware administration.
However, recently Check Point Research (CPR) seen a new 130 attacks using a new multi-functional remote access trojan (RAT) dubbed ‘ToxicEye.
On the other hand, If the user opens the attachment, ToxicEye on installing on the victim’s PC and performs a range of exploits including
- Stealing data
- Deleting or transferring files
- Killing processes on the PC
- Hijacking the PC’s microphone and camera to record audio and video
- Encrypting files for ransom purposes
and more withoud the victim’s knowledge.
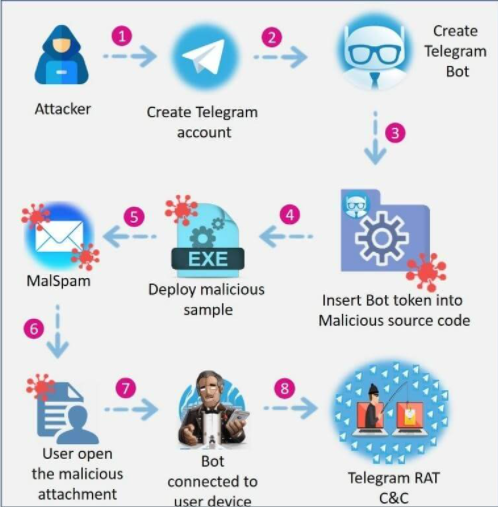
ToxicEye – Infection Chain
The attack chain begins with ToxicEye operators creating a Telegram account and a bot.
A Telegram bot account is a special remote account with which:
- users can interact by Telegram chat
- or by adding them to Telegram groups
- or by sending requests directly from the input field by typing the bot’s Telegram username and a query.
Certainly, the bot is embedded into the ToxicEye configuration file and compiled into an executable file – paypal checker by saint.exe
Any victim infected with this payload can be attacked via the Telegram bot which connects user’s device back to the attacker’s C&C via Telegram.
In addition, this telegram rat can be downloaded and run by opening a malicious document seen in the phishing emails called solution.doc and by pressing on “enable content.”
RAT Trojan Functionality
Obviously, every RAT using this method has its own functionality, according to researchers below are the key capabilities:
- Data stealing features – the RAT can locate and steal passwords, computer information, browser history and cookies.
- File system control – Deleting and transferring files, or killing PC processes and taking over the PC’s task manager.
- I/O hijacking – the RAT can deploy a keylogger, or record audio and video of the victim’s surroundings via the PC’s microphone and camera, or hijack the contents of the clipboard.
- Also, Ransomware features – the ability to encrypt and decrypt victim’s files.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!
Trojan Identification
To spot if you have been infected:
- Search for a file called C:\Users\ToxicEye\rat.exe
- Monitor the traffic generated from PCs in your organization to a Telegram C&C
- Beware of attachments containing usernames
- Undisclosed or unlisted recipient(s)
- Always note the language in the email
- Deploy an automated anti-phishing solution
Indicators Of Compromise
| Telegram RAT project | Samples (sha1) | Protection |
| Telegram Rat 2020 | 173542ba9f3a6b6da172572668b8d105f16eef48 e3a2b905d8d5587d2a123b5b4097df574e9d22c5 ed013c93d22c5c36a425f2aa58c6b7a4c8175c7f | RAT.Win.TelegramRat.A |
| Toxic eye 2020 | 2f452f001efd48f76a67c2f880d926e040775048 3de600dfcc588de8b4a190bc421dd854e29722c5 46396bab68ee8940b35e00840da95d3eac12a1d5 | RAT.Win.ToxicEye.A RAT.Wins.ToxicEye.B |
| Rat via Telegram 2019 | 11cb873cfea6055966ddf78bd3e0c1194586ddac | RAT.Win.TelegramRat.B |
| Teleshadow3 2019 | 75f737f1291552a5d44204d30809831e2c29e44f | RAT.Win.TelegramRat.C |
| MASAD 2017 | 42c30dc551a3cb3bc935c0eae79b79f17942e439 | RAT.Win.ChatC2.A |