
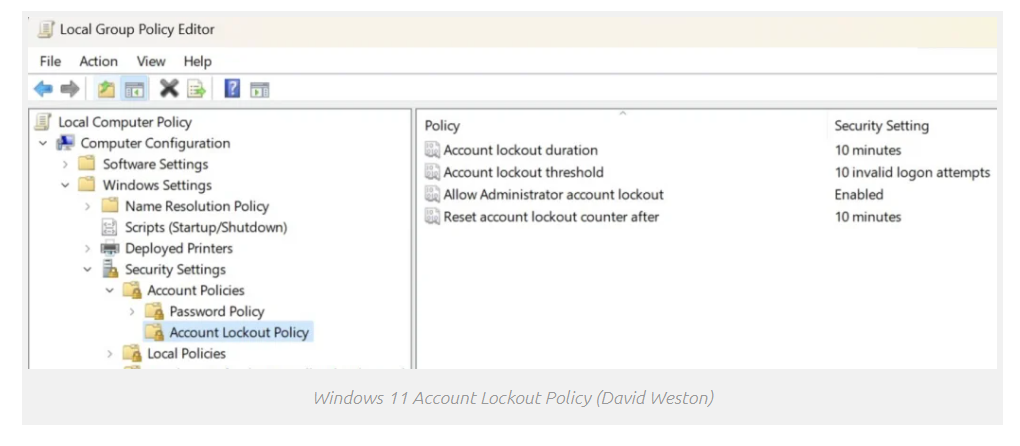
Recent Windows 11 builds come with the Account Lockout Policy policy enabled by default which will automatically lock user accounts (including Administrator accounts) after 10 failed sign-in attempts for 10 minutes.
Brute-force attacks involve inputting a massive number of passwords consecutively, most commonly relying on automation and scripts or extracting them from a dictionary file. As the Account Lockout Policy blocks accounts that input the wrong password 10 times in a row, it could defeat brute-forcing.
Windows 11 Policy
The new policy can be found in Windows 11 Insider Preview Build 22528.1000 and newer. Users have the option of changing not only the number of incorrect password entries that trigger a lock out, but also how long an account should be locked for.
This will help prevent Remote Desktop Services brute force attempts used by threat actors to gain unauthorized access to systems.
According to the FBI, RDP breaches are responsible for roughly 70-80% of all network breaches leading to ransomware attacks.
“A locked account cannot be used until you reset it or until the number of minutes specified by the Account lockout duration policy setting expires,” Microsoft explains.
The account lockout policy is also available on Windows 10, and Weston says it is being backported to Windows Server builds as well.
However, Microsoft, in its documentation, warns of potential denial-of-service (DoS) attacks that could be orchestrated by abusing the Account lockout threshold policy setting.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!





