The malicious campaign leverages the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen to propagate Phemedrone Stealer. Employing sophisticated evasion techniques, it evades conventional security measures to target sensitive user information.
PHEMEDRONE STEALER CAMPAIGN EXPLOITS CVE-2023-36025
Researchers from Trend Micro discovered a malware campaign exploiting the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen. The campaign is associated with the Phemedrone Stealer, capable of extracting various sensitive data.
The infection chain starts with cloud-hosted malicious URL files, frequently camouflaged through URL shorteners. When executed, these files leverage CVE-2023-36025 to initiate the download of the malware.
The campaign focuses specifically on social media, where hackers distribute URL files disguised as innocent link shortcuts. Clicking on these links triggers a call to the GitHub repository, retrieving the necessary shellcode to download and execute the payload. While targeting social media for fraudulent activities is not novel, the use of URL files enhances the efficacy of the trick. Essentially serving as a lockpick, they simultaneously bypass user trust, spam filters, and system protection.
CVE-2023-36025: A GATEWAY FOR CYBERCRIMINALS
In summary, CVE-2023-36025 is a critical vulnerability impacting Microsoft Windows Defender SmartScreen, enabling attackers to circumvent security warnings and checks through manipulation of Internet Shortcut (.url) files.
Despite Microsoft’s patch released on November 14, 2023, cybercriminals have actively exploited this vulnerability, resulting in its inclusion in the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) list.
In the Phemedrone campaign, cybercriminals employ advanced evasion tactics by incorporating a control panel item (.cpl) file to evade Windows Defender SmartScreen. Ordinarily, users should receive a warning upon clicking the URL shortcut. However, the use of a specially crafted file variant bypasses this protection, allowing for the execution of malicious downloads in the background.
Additionally, the campaign exploits a few other well-known weaknesses in Windows, with a particular focus on vulnerabilities within the Windows Control Panel binary.
Phemedrone Stealer is disseminated through cloud hosting and URL shorteners, exploiting CVE-2023-36025 via .url file trickery. Evading Windows Defender SmartScreen, attackers use a .cpl file and MITRE ATT&CK technique T1218.002. The malware employs a DLL loader calling Windows PowerShell to download a loader from GitHub. The second-stage loader, Donut, operates in memory, targeting various applications and services to pilfer sensitive information.
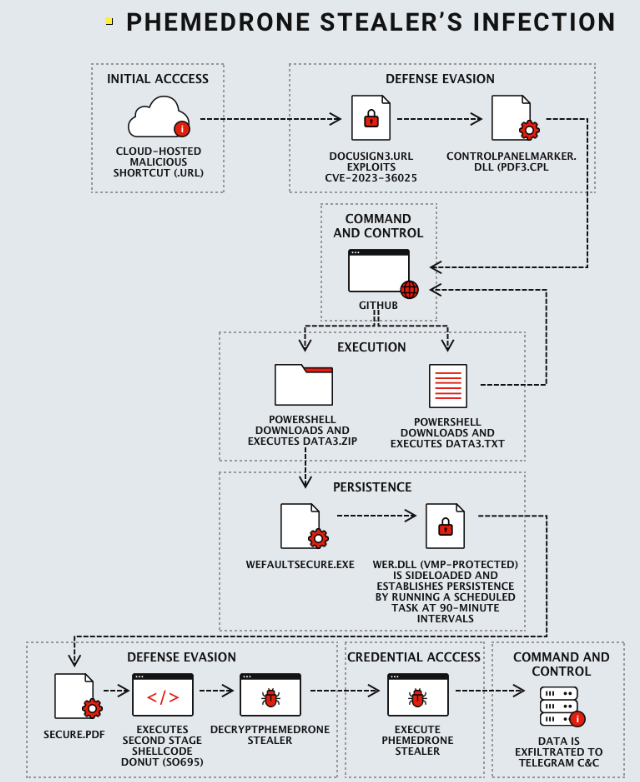
The malware gathers system information, compressing it into a ZIP file using MemoryStream and ZipStorage classes. Following this, it verifies the Telegram API token and transmits the compressed data to the attacker through the SendMessage and SendZip methods. The SendZip method utilizes an HTTP POST request to compress the data into a document and forward it to the Telegram API.
Mitigation Steps
- Keep your OS, apps, and security solution updated to stay protected against evolving cyber threats.
- Exercise caution with Internet Shortcut (.url) files, especially from unverified sources, to avoid potential malware gateways. Verify the legitimacy of URLs before opening them.
- Implement advanced security solutions with real-time monitoring to detect and neutralize malware, providing an extra layer of protection against potential threats.
IOCS
SHA256 f32964087462ba3c96a87ee8387f89de8fa605f2f5bb84cb5f754cd736683f2d 5f1a027f1c1468f93671a4c7fc7b5da00a3c559a9116f5417baa6c1f89550d9f c6765d92e540af845b3cbc4caa4f9e9d00d5003a36c9cb548ea79bb14c7e8f66 a841cd16062702462fdffdd7eef9fc3d88cde65d19c8d5a384e33066d65f9424 815b2125d6f0a5d99750614731aaad2c6936a1dc107a969408a88973f35064c0 ccd19ef6e81e936fc944ebafaefd2ad99ccd11dd15fbc7d3460726bb38237595 ea9b0dee3b7583ce60bba277e2189acb660284abf6b3b9273b6a60c85b0a5ce3 9a96406ae06b703d827fffd1f1ced0781f89ca2af6d5041721e9fbd2647c8430 22236e50b5f700f5606788dcd5ab1fb69ee092e8dffdd783ac3cab47f1f445ab 1433efd142007ce809aff5b057810f5a1919ea1e3ff740ff0fcc2fc729226be5 ad513d2cba6cc82a50ee6531b275e937480d8fee20af2b4f41da5f88e408a4e9 7c0a1e11610805bd187ef6e395c8fa31c1ae756962e26cdbff704ce54b9e678a 4ae28a44c38edc516e449ddd269b5aa9924d549d763773dcd312b48fe6bb91ab c9743e7ffb6f6978f08f86e970ddb82e24920d266b32bd242254fbf51abfe6ce c3bfaa1f52abdbb673d83af67090112dfdfe9ea8ff7a613f62bd48bace205f75 6bd8449de1e1bdd62a86284ed17266949654f758e00e10d8cd59ec4d233c32e5 4446d5b475ce8aed5244da917ae42b6cb9744ffc4efd766af8e4dee7dd5a3e19 70c23213096457df852b66443d9a632e66816e023fdf05a93b9087ffb753d916 69941417f26c207f7cbbbe36ce8b4d976640a3d7f407d316932428e427f1980b e2d19a23b19a07d35d16990e78c5cfaa3dd97b9ce92201f4db18a7da95fe6ff8 b7f53c507a1aa4254b66a883285e27b42d65ea4ea4206fe674e0d03738f52141 4ae28a44c38edc516e449ddd269b5aa9924d549d763773dcd312b48fe6bb91ab c6765d92e540af845b3cbc4caa4f9e9d00d5003a36c9cb548ea79bb14c7e8f66 f24a8b3144e89b9bececfbf76add87ddefbd19a024a85692026e97f3a9911902 e64b185c149cb523d13cb46ea3911e2c0595b6f10ae86e6a14b15e8d45c0cdcb cb58bf466675be9e11cfb404503cb122514f47b9708d033e381f28a60535812c 80f88566fda41ebc1b4e35d89748a804740bba0d03049c33c536cffd5e0491e2 4a36cc607ca5c2acc536510fd1b0ddd43a9403dac168d2420d474611909ed9e6 89caa1568fcff162086dae91e6bd34fd04facba50166ebff800d45a999d0be8b 188c72f995ebd5e1e8d0e3b9d34eeeec2ec95d4d0fee30d2ea0f317ab1596eef e326c1b9e61cca6823300158e55381c6951b09d2327a89a8d841539cad3b4df3 4da33c7fe62f71962913d7b40ff76aff9f1586e57db707b3d6b88162c051f402 ff44e502bd5ea36e17b3fc39b480e65971b36002f27fb441e4acadd6bf604a20 b7980f64f892d70b1cd72a8c80f8319f50c3c410aba4e4bc63fd6494bcb4f313 480fae3bdc2604cba846779dd7dced95b3ce036bdef629ded247771a2e4d5d58 348aea633c99e5f6a0ac7b850961be0a145a35678e5bd074b4852f7a2419f518 1c53dffcb4c474a2b08708609466e7d234d6d51139b6532af54fac5bb8d37415 b37ec923451dd15a0f68df0b392b0f1b243fe50c709de9e574ac14cf6fabdd53 f2814a4b3796fb44045c33b9d0d9972bf40478e5bc74b587486900c6cfa02f3d 5f1a027f1c1468f93671a4c7fc7b5da00a3c559a9116f5417baa6c1f89550d9f 8b73d7aa8bb8db8a9ecbf9f713934fbbb5caf4745d7a61a6f34a100c4d84fd9d 9b9ba722b314febfc44919551a03dde1539f115333183c2cb5e74b8e644ba5b3 568b4b868b225f06bb34da0dc23603c9dedccc2b319353407c814983d5322563 5ecad303475e180f8879871d8571d1a7eeb99e0b3c63cc77fdd02cb9b8c51211 d5b1214f1817a16b2bc8a76daa48c9a3c5af0e411cf4f0c17b0e364d437a454b 5f0ff1fd6ca89a0ddd3178e023dea8f79ff3c3f3d8ff7900378eb014e83ed326 40c6fa38e44e00d8cf113d0a079cd46f8b7654331f12e50d2af5a9f1ddc6d266 3a34cd3a3221d83a1cca8913b2afbb5b780027d48b44d3ce15dfe4a402064871 URLs hxxps[://]raw[.]githubusercontent[.]com/nateeintanan2527/Joyce_Data/main/DATA3[.]txt hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1175808264479449138/DocuSign3[.]url?ex=656c93c7&is=655a1ec7&hm=6e8b316f2112cfaf27bc8cf35089098e4a0f2d16054e8d199c13588c31b2e383& hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1177255995156742144/DocuSign4[.]url?ex=6571d815&is=655f6315&hm=f9e208714ffc862f97cb6363fb887f11fda0020802a020a56a571c4195114854& hxxps[://]shorturl[.]at/ixEZ7 file[://]51[.]79[.]185[.]145/pdf/data4[.]zip/pdf4[.]cpl hxxp[://]51[.]79[.]185[.]145/pdf/kay[.]zip/kay[.]cpl hxxp[://]51[.]79[.]185[.]145/pdf/data2[.]zip/pdf2[.]cpl hxxp[://]51[.]79[.]185[.]145/pdf/ hxxps[://]shorturl[.]at/flEK5 hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1167767477921513512/SecureDocuSign_pdf[.]url?ex=654f5336&is=653cde36&hm=08ea24126262ff865a1ab0c79f20e41e9e53896d9cda8e0c374c077f5a500b00& hxxps[://]shorturl[.]at/vzAD2 hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1170627585105997854/DocuSign2[.]url?ex=6559bae5&is=654745e5&hm=ab8a5d275414768c20bd9a8a0e434c4b8fe7c0bd8006c3b5f69cc80b7fe57cb1& hxxps[://]shorturl[.]at/bsuCR hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1170627584627855481/DocuSign1[.]url hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1170627584627855481/DocuSign1[.]url?ex=6559bae5&is=654745e5&hm=acf93c3a4f79068689d20d197ac297533dc28d94bb93f4ec1021c7c258c8dbda& file[://]51[.]79[.]185[.]145/pdf/data1[.]zip/pdf1[.]cpl file[://]51[.]79[.]185[.]145/pdf/data2[.]zip/pdf2[.]cpl hxxps[://]shorturl[.]at/flEK5 hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1167767477921513512/SecureDocuSign_pdf[.]url?ex=654f5336&is=653cde36&hm=08ea24126262ff865a1ab0c79f20e41e9e53896d9cda8e0c374c077f5a500b00& file[://]51[.]79[.]185[.]145/pdf/data[.]zip/docusign_pdf[.]cpl hxxps[://]shorturl[.]at/clpIO hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1171355007245893653/DocuSignDocument[.]url?ex=655c605c&is=6549eb5c&hm=2aeb65239a890e6b070957136681600ca33584e578816faeab471a5e11004538& file[://]51[.]79[.]185[.]145/pdf/data3[.]zip/pdf3[.]cpl hxxps[://]shorturl[.]at/eqxU0 hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1175808264479449138/DocuSign3[.]url?ex=656c93c7&is=655a1ec7&hm=6e8b316f2112cfaf27bc8cf35089098e4a0f2d16054e8d199c13588c31b2e383& file[://]51[.]79[.]185[.]145/pdf/kay[.]zip/kay[.]cpl hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1177255994775064717/kay[.]url?ex=6571d815&is=655f6315&hm=5edd3e4b0cc773a06fe9f1a8177f99239a105079f23eb7707c225be4867160df& hxxps[://]shorturl[.]at/dMY69 hxxps[://]cdn[.]discordapp[.]com/attachments/853270434422456330/1184415259717533726/My_Photo_Album[.]url hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1177255995156742144/DocuSign4[.]url?ex=6571d815&is=655f6315&hm=f9e208714ffc862f97cb6363fb887f11fda0020802a020a56a571c4195114854& hxxps[://]shorturl[.]at/ixEZ7 hxxps[://]cdn[.]discordapp[.]com/attachments/853270434422456330/1183676616564547624/image_reported[.]url?ex=658933c1&is=6576bec1&hm=b60477e0a798182a1dc0ea65def7305b111ce06a398667a1c567b3f9afd253b2& file[://]51[.]79[.]185[.]145/pdf/data2[.]zip/pdf2[.]cpl hxxps[://]shorturl[.]at/oORV9 file[://]51[.]79[.]185[.]145/pdf/data3[.]zip/pdf3[.]cpl hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1172211288303206400/DocuSign3[.]url?ex=655f7dd5&is=654d08d5&hm=26a68927b4c05c243d910f3a5ebcf2c6ec43bcb7f460acd45891b3b21b308cdc& hxxps[://]cdn[.]discordapp[.]com/attachments/853270434422456330/1176802586481922098/image_reported[.]url hxxps[://]shorturl[.]at/gnL15 hxxps[://]cdn[.]discordapp[.]com/attachments/1083311514368360519/1170627585680609280/DocuSign3[.]url hxxps[://]shorturl[.]at/dKOR6 hxxps[://]github[.]com/nateeintanan2527/Joyce_Data[.]git hxxps[://]github[.]com/nateeintanan2527/Data_Document[.]git hxxps[://]raw[.]githubusercontent[.]com/nateeintanan2527/Joyce_Data hxxps[://]raw[.]githubusercontent[.]com/nateeintanan2527/Data_Document IP 51[.]79[.]185[.]145
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment