Russian threat group APT29 targeted German political parties with a new backdoor, WINELOADER, via spear-phishing emails containing malicious links to ZIP files on compromised websites.
These ZIP files deployed an HTA initiating a multi-stage infection chain, delivering WINELOADER, which communicates with command and control servers and employs evasion techniques.
All about WINELOADER Malware
To counter the APT29 campaign, security teams must grasp these TTPs and the WINELOADER backdoor to enhance detection capabilities. APT29 utilizes spear-phishing emails with a malicious PDF attachment disguised as a wine-tasting invitation, tricking victims into downloading a ZIP file containing an HTA (wine.hta or invite.hta).
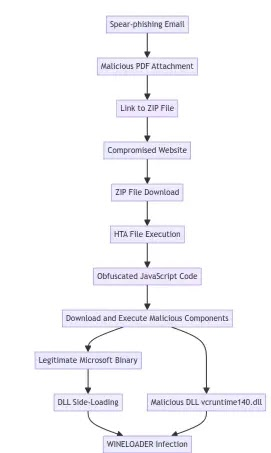
The HTA employs obfuscated JavaScript, potentially obfuscated with obfuscator.io, to download and execute a legitimate but vulnerable Microsoft binary (sqlwriter.exe or sqldumper.exe) alongside a malicious DLL (vcruntime140.dll). The legitimate binary sideloads the malicious DLL, establishing the initial foothold for the WINELOADER infection.
The Splunk Threat Research Team devised an Atomic Red Team test to replicate the initial access of the WINELOADER campaign, omitting the data exfiltration tools. This test involves an HTA triggering a base64-decoded payload (invite.zip) containing a DLL (gup.exe), mirroring the side-loading behavior. Additionally, it injects sqlwriter.exe into a benign vcruntime140.dll to mimic real-world attacks.
By running and analyzing this test, security teams can assess their ability to detect APT29 TTPs, enhancing their analytics, response processes, and overall security posture.
The HTA file exploits a DLL side-loading vulnerability by writing the Base64-encoded content of a malicious ZIP file (invite.zip) to a text file (invite.txt) on the system. It then decodes the text file back to a ZIP and extracts its contents.
Before executing the payload, likely a malicious DLL named gup.exe, it triggers a user prompt, “Are You Ready?” If the user clicks “OK,” the DLL is loaded and likely spawns calc.exe as a test. Finally, a message box confirms successful DLL side-loading with the Atomic logo.
WINELOADER exploits legitimate applications like SQLWriter.exe or Sqldumper.exe through DLL side-loading by loading a malicious vcruntime140.dll that triggers code execution. The code decrypts a hidden data block using the RC4 algorithm with a key stored within the malicious DLL itself, allowing WINELOADER to gain initial functionality on a compromised system.
Researchers analyzed a malicious DLL file (vcruntime140.dll) containing a variant of WINELOADER malware, which is encrypted with the RC4 algorithm and hides critical components like API names and strings to avoid detection.
After decryption, the malware connects to its command and control server (C2) and downloads additional malicious components, as revealed in the report, which also provides the C2 server addresses and user-agent strings used by the malware.













Leave A Comment