XWorm is a recent addition to the remote access trojan family, quickly establishing itself as one of the most enduring global threats.
Since its initial detection by researchers in 2022, XWorm has undergone several major updates, markedly augmenting its capabilities and cementing its long-term resilience.
The analyst team at ANY.RUN encountered the latest iteration of the malware and seized the opportunity to dissect it, delving into the intricacies of XWorm’s configurations and mechanics. Here’s a glimpse into their methodology and their discoveries.
The XWorm sample’s source
The particular sample was located within ANY.RUN’s extensive malware database, which houses comprehensive analysis reports for files and links uploaded by users to the public mode sandbox.
The analysis results unveiled that the sample’s initial distribution occurred through MediaFire, a file-hosting service. The malware was concealed within a password-protected RAR archive.
Upon execution, the threat was instantly detected by Suricata rules and identified as XWorm.

XWorm’s Tactics, Techniques, and Procedures (TTPs)
The sandbox report brought to light various techniques employed by the sample:
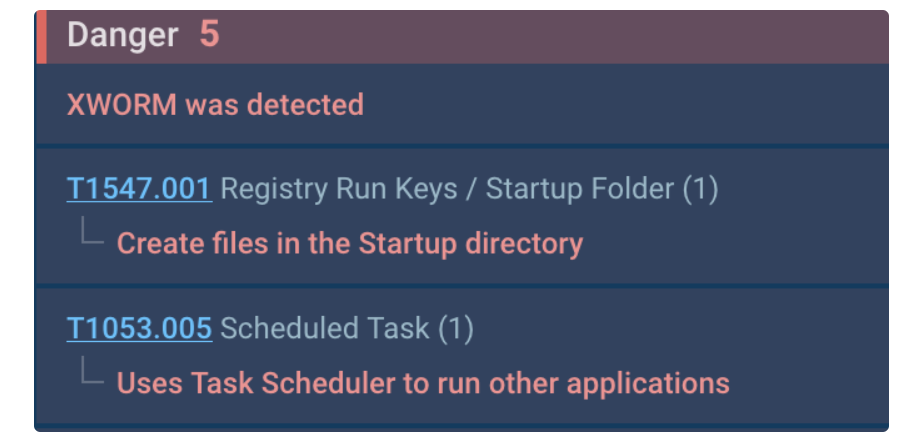
MITRE T1547.001: XWorm inserted its shortcut into the Startup directory.
MITRE T1053.005: It leveraged the task scheduler to initiate self-restarts, employing the “/RL HIGHEST” parameter to gain elevated privileges.
MITRE T1074.001: The software was positioned within the Public directory.
MITRE T1571: The malware attempted to establish a connection with a remote server, but it received no response.
XWorm’s failed attempt to evade sandbox analysis
Because the first analysis report was a few days old, the team chose to retest the sample in the sandbox to look for any new actions.
However, when they started it, the malware crashed very quickly. After a brief examination, it became clear that the sample was now asking a special service if it was operating in a virtual sandbox.
In essence, the XWorm developers added a trick to avoid detection, causing the malicious software to stop running as soon as it detected a virtualized environment.
To address this issue, the team activated the Residential Proxy feature in the sandbox settings. This function substitutes the datacenter IP address of the virtual machine with one from a legitimate internet service provider, tricking the malware into believing it is operating on a real user’s device.
After rerunning the sample with Residential Proxy enabled, XWorm was successfully executed and began its activity.
Static analysis of the new XWorm variant
After gathering essential sandbox data, analysts initiated the static analysis phase. They loaded the sample into Detect it Easy (DIE), a standard tool for initial malware analysis. DIE promptly identified it as a .NET version of XWorm.
Next, the team used dnSpy, a .NET debugger, to examine the file, uncovering extensive obfuscation within the binary. Despite employing Heuristic scanning, DIE was unable to identify the packer.
Employing de4dot, a .NET deobfuscator and unpacker, also did not have any effect.
Extraction of XWorm’s configuration
Subsequently, the analysts located a constructor resembling a settings block and employed a function to modify certain field values within it. In this process, the malware initially computed an MD5 hash from a value found in the presumed settings section.
Following this, it duplicated the derived value into a temporary array twice, albeit with an off-by-one error causing the MD5 to be partially copied only once. The team utilized this array as a key for decrypting incoming base64 strings using AES in ECB mode.
Additionally, they identified that the field in use was a mutex. For a comprehensive breakdown of this entire procedure, refer to ANY.RUN’s blog article titled “XWorm: Technical Analysis of a New Malware Version.”
Conclusion
Gaining configurations for the latest malware is essential but often time-consuming. To streamline this process, consider running your samples through the ANY.RUN sandbox, where you can access the required information within seconds.













Leave A Comment