In recent years, zero-day exploits and attacks have emerged as prominent threats. Leveraging unknown vulnerabilities within software, these attacks are nearly impossible to detect and prevent. Zero-day attacks can result in severe consequences, enabling attackers to gain control of systems, pilfer data, or install malware.
WHAT IS A ZERO-DAY ATTACK?
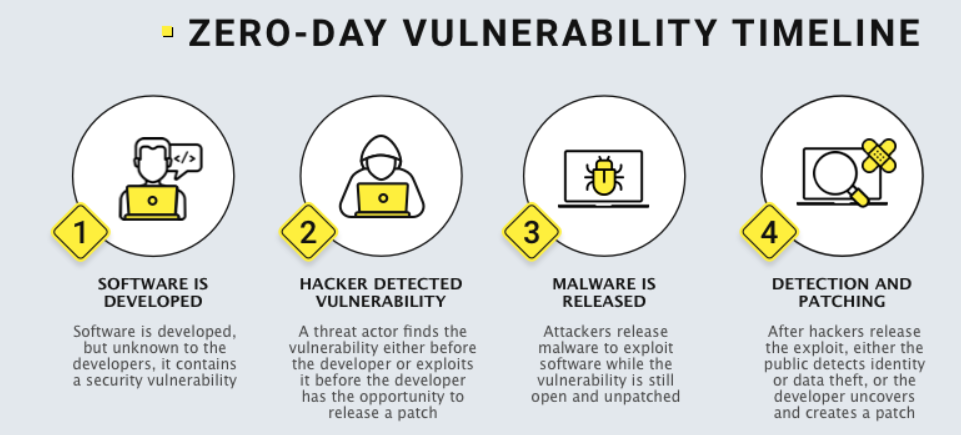
A zero-day attack is a type of cyber threat that takes advantage of a software vulnerability unknown to the developer or vendor. Attackers exploit this undisclosed weakness before a fix or patch is available, making it challenging for security measures to detect or prevent such attacks. Zero-day attacks can target various applications, posing a significant challenge for cybersecurity professionals.
Cyber attackers exploit undisclosed vulnerabilities in programs or operating systems to execute their code more effectively. The frequently utilized exploits include those enabling remote code execution and privilege escalation, granting attackers extensive control within the compromised environment. These sophisticated attacks are typically directed at corporations, given their possession of more valuable data.
Exploiting a breach without raising alarms or attracting attention is made simple when the only individual aware of it is the criminal who discovered it. Even advanced EDR solutions may err by overlooking actions from trusted programs without recognizing their potential malicious intent. Hence, opting for an endpoint protection application capable of preventing zero-day attacks is a prudent choice.
IDENTIFYING AND ADDRESSING ZERO-DAY EXPLOITS AND ATTACKS
Identifying and addressing zero-day exploits and attacks involves several key steps:
- Continuous Monitoring: Implement robust monitoring systems to detect unusual patterns or behaviors within your network and systems. Real-time monitoring can help identify potential zero-day exploits early on.
- Anomaly Detection: Utilize anomaly detection tools and machine learning algorithms to identify deviations from normal system behavior. Unusual network traffic, unexpected file modifications, or abnormal user activities can be indicators of zero-day exploits.
- Threat Intelligence Feeds: Subscribe to threat intelligence feeds to stay informed about emerging threats and vulnerabilities. These feeds provide up-to-date information on potential zero-day exploits, enabling proactive measures.
- Behavioral Analysis: Employ behavioral analysis tools that can identify malicious activities based on behavior rather than known signatures. This approach is effective against previously unseen threats.
- Patch Management: Regularly update and patch software and systems to address known vulnerabilities. While this doesn’t directly identify zero-day exploits, it reduces the attack surface and makes it harder for attackers to find and exploit vulnerabilities.
- User Training and Awareness: Educate users about phishing attacks and social engineering tactics, as these are common entry points for zero-day exploits. Users should be cautious about clicking on suspicious links or downloading attachments from unknown sources.
- Network Segmentation: Implement network segmentation to limit the impact of potential exploits. Isolating critical systems and data can prevent lateral movement within the network.
- Incident Response Plan: Develop and regularly update an incident response plan that includes procedures for addressing zero-day exploits. This ensures a coordinated and efficient response when an attack is detected.
- Endpoint Protection: Utilize advanced endpoint protection solutions that employ heuristics, behavioral analysis, and other advanced techniques to identify and block zero-day exploits.
- Collaboration: Engage with cybersecurity communities, share threat intelligence, and collaborate with industry peers to stay informed about evolving threats and effective mitigation strategies.
Organizations have faced persistent challenges in patch management, partly due to the sheer volume of patches requiring attention. In 2021 alone, more than 20,000 vulnerabilities were addressed, adding to the complexity of staying abreast of all the necessary updates.
Ignoring timely updates, many users believe they can postpone software updates for days or weeks without consequences. This practice poses significant risks, often underestimated by users. Additionally, patch management receives minimal emphasis in security awareness training, despite the Department of Homeland Security advising the application of critical patches within 15 days of release.
Identifying critical patches can pose a dilemma for security teams. They adhere to internal testing procedures to verify the reliability of patches before deployment, considering potential bugs or ineffectiveness that could cause harm. Additionally, IT teams have established processes to monitor and track patch deployments, ensuring comprehensive coverage to prevent any device or system from being left unpatched.
HOW TO PROTECT AGAINST ZERO-DAYS?
Protecting against zero-days involves implementing a multi-faceted approach:
- Up-to-Date Security Measures:
- Ensure all security software, including antivirus and intrusion detection systems, is updated regularly.
- Network Segmentation:
- Implement network segmentation to limit the impact of potential zero-day exploits, isolating critical systems.
- User Training:
- Educate users on recognizing phishing attempts and suspicious activities to minimize the risk of falling victim to zero-day attacks.
- Behavioral Analysis:
- Use behavioral analysis tools to identify anomalous activities and behaviors that may indicate a zero-day attack.
- Threat Intelligence Feeds:
- Subscribe to threat intelligence feeds to stay informed about emerging threats and vulnerabilities, including potential zero-days.
- Patch Management:
- Regularly update and patch software to reduce the attack surface and address known vulnerabilities, minimizing the risk of exploitation.
- Zero-Day Threat Detection Tools:
- Utilize advanced threat detection tools designed to identify patterns associated with zero-day attacks.
- Endpoint Protection:
- Employ robust endpoint protection solutions with heuristic and behavioral analysis capabilities to detect and prevent zero-day exploits.
- Incident Response Plan:
- Develop a comprehensive incident response plan that includes procedures specific to handling zero-day attacks, ensuring a swift and effective response.
- Collaboration:
- Engage with cybersecurity communities, share threat intelligence, and collaborate with industry peers to enhance awareness and preparedness against zero-day threats.
- Continuous Monitoring:
- Implement continuous monitoring of network traffic, user activities, and system behaviors to detect unusual patterns indicative of potential zero-day exploits.
- Security Updates and Best Practices:
- Stay informed about security updates, industry best practices, and recommended security configurations to strengthen overall defense against zero-day vulnerabilities.













Leave A Comment