A new malware, named Jupyter that steals information’s from the user, and also the malware is used to create a backdoor on the infected device.
Introduction to Jupyter Malware:
An Infostealer is a trojan that is created to gather and ex-filtrate sensitive information from an infected system.
However, there is a large variety of infostealer’s active in the wild, some are independent, and some act as a modular part of a larger task such as a Banking Trojan (Trickbot) or a RAT.
Jupyter is an infostealer that primarily targets Chromium, Firefox, and Chrome browser data. Delivering the stealer starts with downloading an installer (Inno Setup executable) in a ZIP archive that poses as legitimate software
Installer Evades From Detection for Last 6 Months:
A variant of the malware emerged during an incident response engagement in October at a University in the U.S. But forensic data indicates that earlier versions have been developed since May.
Researchers at cybersecurity company Morphisec discovered that the developers of the attack kit were highly active, some components receiving more than nine updates in a single month, and went fully undetected on the VirusTotal scanning platform for the last six months.
Above all, Jupyter is .NET-based and its focal point are on stealing data from browsers like: Chromium, Mozilla Firefox, and Google Chrome – cookies, credentials, certificates, autocomplete information.
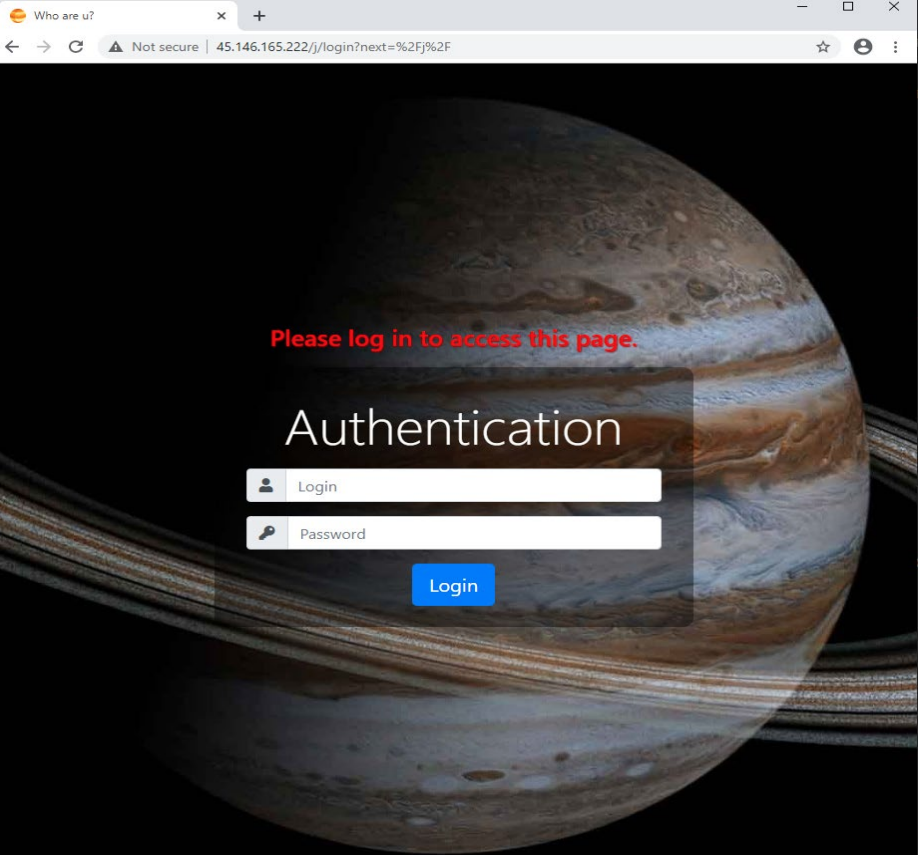
The Targeted Workflow:
However, Jupyter its attack chain, delivery, and loader demonstrate additional capabilities for full backdoor functionality. These include:
- a C2 client
- download and execute malware
- execution of PowerShell scripts and commands
- hollowing shellcode into legitimate windows configuration applications.
From what Morphisec observed, the initial installers that start the attack chain pose as Microsoft Word documents and use the following names:
- The-Electoral-Process-Worksheet-Key.exe
- Mathematical-Concepts-Precalculus-With-Applications-Solutions.exe
- Excel-Pay-Increase-Spreadsheet-Turotial-Bennett.exe
- Sample-Letter-For-Emergency-Travel-Document
The installers run legitimate tools like Docx2Rtf and Magix Photo Manager to create a diversion while dropping in the background two PowerShell scripts, one encoded and decoded by the other.
Indicators Of Compromise:
Zip:
- 02a52b218756fa65e9fd8a9acb75202afd150e4c
- ce9d62978c8af736935af5ed1808bfc829cbb546
- 591f33f968ed00c72e2064e54ccb641272681cb4
C2:
- 45.135.232[.]131
- 45.146.165[.]222
- 45.146.165[.]219
- 91.241.19[.]21
- gogohid[.]com
- spacetruck[.]biz
- blackl1vesmatter[.]org
- Mixblazerteam[.]com
- vincentolife[.]com/j
- On-offtrack[.]biz
and more.
“The client then downloads the next stage, a PowerShell command that executes the in-memory Jupyter .NET module,” Morphisec explains.













Leave A Comment