Avast researchers recently uncovered GuptiMiner, an aged malware. It leverages the eScan antivirus update system to surreptitiously implant backdoors and cryptocurrency mining software into users’ computers and extensive corporate networks. This discovery underscores cybercriminals’ efforts to circumvent contemporary security protocols. Let’s delve deeper into this development.
GUPTIMINER EXPLOITS
Avast experts examined GuptiMiner, a malware active since 2018, targeting corporate networks with backdoors and concealed cryptomining. Employing a multi-stage infection process, the malware initiates by intercepting antivirus updates via man-in-the-middle (MitM) assaults, enabling attackers to replace authentic updates with malicious ones.
Avast alerted eScan and India CERT about the discovered vulnerability, successfully patched on July 31, 2023. However, as users seldom employ multiple antivirus programs, it hampers the ability to fully detect and analyze GuptiMiner’s operations.
The malware employs a sophisticated infection process. Initially, it intercepts eScan antivirus updates. During the download process, an attacker intervenes, replacing the legitimate update with a malicious version. Subsequently, eScan decompresses and downloads the package, initiating a chain of infection via a DLL. This DLL facilitates further downloads and code execution by the virus.
Following this, GuptiMiner employs a sideloading method to insert malicious code into trusted processes, ensuring its invisibility to antivirus systems. Additionally, the malware communicates with remote command and control (C2) servers to receive instructions and updates. This grants attackers control over infected systems, enabling the execution of further malicious activities or cryptocurrency mining operations.
HOW GUPTIMINER OPERATES
The GuptiMiner analysis unveiled its utilization of sophisticated methods to install and conceal its presence on systems. Key techniques encompassed sideloading DLL, altering system files, and employing forged digital signatures to feign legitimacy.
Furthermore, GuptiMiner’s distinguishing trait is its capacity to modularize infections, involving DNS queries to the attacker’s DNS servers and extracting data from seemingly innocuous images. In addition to its primary function of installing backdoors, GuptiMiner unexpectedly disseminates the XMRig miner for Monero cryptocurrency mining.
The malware is potentially associated with Kimsuky, a prominent North Korean hacking group, suggesting potential state sponsorship and highly organized attacks. Given North Korean hackers’ previous interest in cryptocurrency, this revelation isn’t entirely unexpected.
During GuptiMiner analysis, researchers uncovered two distinct types of backdoors, each tailored to serve specific functions within a meticulously orchestrated and expansive campaign targeting corporate networks.
The initial type of backdoor, a modified PuTTY Link, scans SMBs on the local network. This enables lateral movement, granting access to potentially vulnerable systems running Windows 7 and Windows Server 2008, thus exploiting vulnerabilities in legacy operating systems.
The second type of backdoor is multifunctional and modular, receiving commands from the attacker to install extra modules. Its focus lies in locating and pilfering locally stored private keys and cryptocurrency wallets. This tactic enables attackers to surveil infected systems over extended periods and trigger supplementary malicious functionalities as needed.
Indicators of Compromise
Domains
| Domain |
| _spf.microsoft[.]com |
| acmeautoleasing[.]net |
| b.guterman[.]net |
| breedbackfp[.]com |
| crl.microsoft[.]com |
| crl.peepzo[.]com |
| crl.sneakerhost[.]com |
| desmoinesreg[.]com |
| dl.sneakerhost[.]com |
| edgesync[.]net |
| espcomp[.]net |
| ext.microsoft[.]com |
| ext.peepzo[.]com |
| ext.sneakerhost[.]com |
| gesucht[.]net |
| gesucht[.]net |
| globalsign.microsoft[.]com |
| icamper[.]net |
| m.airequipment[.]net |
| m.cbacontrols[.]com |
| m.gosoengine[.]com |
| m.guterman[.]net |
| m.indpendant[.]com |
| m.insomniaccinema[.]com |
| m.korkyt[.]net |
| m.satchmos[.]net |
| m.sifraco[.]com |
| ns.bretzger[.]net |
| ns.deannacraite[.]com |
| ns.desmoinesreg[.]com |
| ns.dreamsoles[.]com |
| ns.editaccess[.]com |
| ns.encontacto[.]net |
| ns.gravelmart[.]net |
| ns.gridsense[.]net |
| ns.jetmediauk[.]com |
| ns.kbdn[.]net |
| ns.lesagencestv[.]net |
| ns.penawarkanser[.]net |
| ns.srnmicro[.]net |
| ns.suechiLton[.]com |
| ns.trafomo[.]com |
| ns.trafomo[.]com |
| ns1.earthscienceclass[.]com |
| ns1.peepzo[.]com |
| ns1.securtelecom[.]com |
| ns1.sneakerhost[.]com |
| p.bramco[.]net |
| p.hashvault[.]pro |
| r.sifraco[.]com |
| spf.microsoft[.]com |
| widgeonhill[.]com |
| www.bascap[.]net |
Mutexes
| Mutex |
| ESOCESS_ |
| Global\Fri Aug 13 02:17:49 2021 |
| Global\Fri Aug 13 02:22:55 2021 |
| Global\Mon Apr 19 06:03:17 2021 |
| Global\Mon Apr 24 07:19:54 2023 |
| Global\Mon Feb 27 08:11:25 2023 |
| Global\Mon Jun 14 03:22:57 2021 |
| Global\Mon Mar 13 07:29:11 2023 |
| Global\Mon Mar 22 09:16:00 2021 |
| Global\Sun Jun 13 08:22:07 2021 |
| Global\Thu Aug 10 03:25:11 2023 |
| Global\Thu Aug 12 02:07:58 2021 |
| Global\Thu Feb 23 08:37:09 2023 |
| Global\Thu Mar 25 02:03:14 2021 |
| Global\Thu Mar 25 09:31:19 2021 |
| Global\Thu Nov 2 08:21:56 2023 |
| Global\Thu Nov 9 06:19:40 2023 |
| Global\Tue Apr 25 08:32:05 2023 |
| Global\Tue Mar 23 02:37:32 2021 |
| Global\Tue Oct 10 08:07:11 2023 |
| Global\Wed Aug 11 09:16:37 2021 |
| Global\Wed Jan 5 09:15:56 2022 |
| Global\Wed Jun 2 09:43:03 2021 |
| Global\Wed Mar 1 01:29:48 2023 |
| Global\Wed Mar 23 08:56:01 2022 |
| Global\Wed Mar 23 09:06:36 2022 |
| Global\Wed May 10 06:38:46 2023 |
| Global1 |
| GlobalMIVOD_V4 |
| GMCM1 |
| MIVOD_6 |
| MTX_EX01 |
| Mutex_ONLY_ME_V1 |
| Mutex_ONLY_ME_V2 |
| Mutex_ONLY_ME_V3 |
| PROCESS_ |
| SLDV014 |
| SLDV02 |
| SLDV024 |
| SLDV04 |
| SLDV10 |
| SLDV11 |
| SLDV13 |
| SLDV15 |
| SLDV17 |
| SLDV22 |
| SLDV26 |
Stage 0 – Installation Process
| IoC | Note |
| http://update3[.]mwti[.]net/pub/update/updll3.dlz | |
| c3122448ae3b21ac2431d8fd523451ff25de7f6e399ff013d6fa6953a7998fa3 | C:\Program Files\eScan\VERSION.DLL |
| 7a1554fe1c504786402d97edecc10c3aa12bd6b7b7b101cfc7a009ae88dd99c6 | updll65.dlz |
Stage 1 – PNG Loader
| IoC | Note |
| ff884d4c01fccf08a916f1e7168080a2d740a62a774f18e64f377d23923b0297 | |
| ext.peepzo[.]com | |
| crl.peepzo[.]com | |
| ns1.peepzo[.]com | |
| http://www.deanmiller[.]net/m/ | |
| 294b73d38b89ce66cfdefa04b1678edf1b74a9b7f50343d9036a5d549ade509a | |
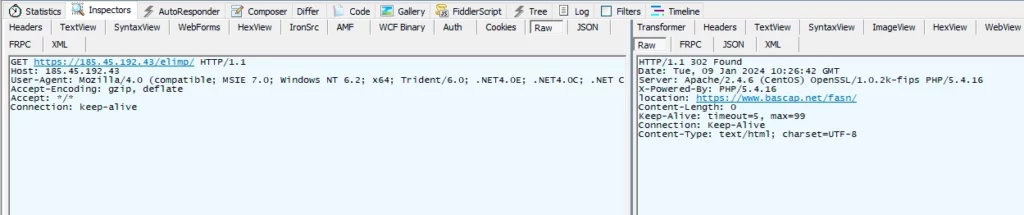
| 185.45.192[.]43/elimp/ | |
| 6305d66aac77098107e3aa6d85af1c2e3fc2bb1f639e4a9da619c8409104c414 | |
| SYSTEM\CurrentControlSet\Control\Arbiters\Class | Registry |
| SYSTEM\CurrentControlSet\Control\CMF\Class | Registry |
| SYSTEM\CurrentControlSet\Control\CMF\CORE | Registry |
| SYSTEM\CurrentControlSet\Control\CMF\DEF | Registry |
| SYSTEM\CurrentControlSet\Control\CMF\Els | Registry |
| SYSTEM\CurrentControlSet\Control\CMF\ASN | Registry |
| SYSTEM\CurrentControlSet\Control\MSDTC\BSR | Registry |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!












Leave A Comment