Autodesk Drive serves as a cloud-based data-sharing platform for organizations, facilitating document and file sharing. It accommodates various file formats, including 2D and 3D data files such as PDFs, accessible with a subscription to other Autodesk products.
A recent discovery reveals a new attack campaign exploiting the Autodesk hosting platform to distribute malicious PDF files, initiating phishing attacks targeting victims for the explicit purpose of harvesting Microsoft login credentials.
Hackers exploit Autodesk Drive
Threat actors, as reported by Cyber Security News, have utilized compromised email accounts to seek out and target fresh victims, leveraging these accounts to embed Autodesk links in emails, thereby reducing suspicion among recipients.
Furthermore, emails originating from these compromised accounts include authentic email signature footers.
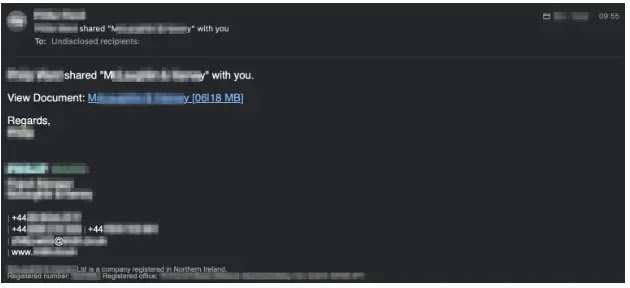
When victims click on the Autodesk Drive links in these emails, they are directed to view the PDF document, typically featuring the sender’s name and their affiliated company, aimed at bolstering trust in the phishing attempt.
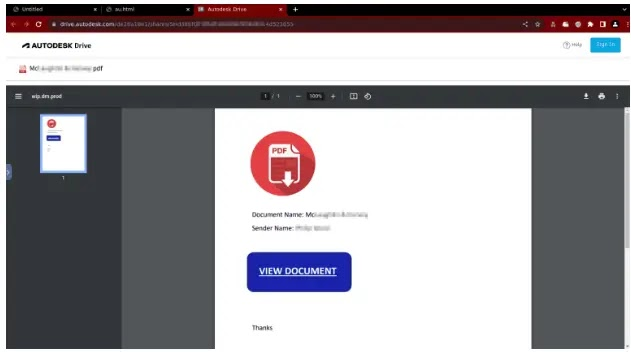
The PDF link includes a “VIEW DOCUMENT” option, leading to a phishing link resembling a Microsoft login form, prompting victims to enter their credentials.
After submitting their credentials, users are redirected to a real estate investment book on Microsoft’s OneDrive, creating the impression of legitimacy. However, the credentials were harvested by threat actors via the spoofed form.
With the victim’s Microsoft credentials, threat actors can infiltrate sensitive company data and launch further phishing attacks targeting privileged Microsoft accounts.
Additionally, a notable pattern emerged: the phishing emails varied in language.
This observed behavior suggests that threat actors automated the phishing emails, adapting the language based on the sender’s locale.
Further evidence supporting this theory was a similar phishing email from a Canadian manufacturing company, using French in the PDF.
Organizations and employees should stay vigilant against phishing attacks. Furthermore, it’s essential to verify the URL of every login form before entering credentials.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment