
Emotet is a Trojan that is primarily spread through spam emails (malspam). The infection may arrive either via a malicious script, macro-enabled document files, or malicious link.
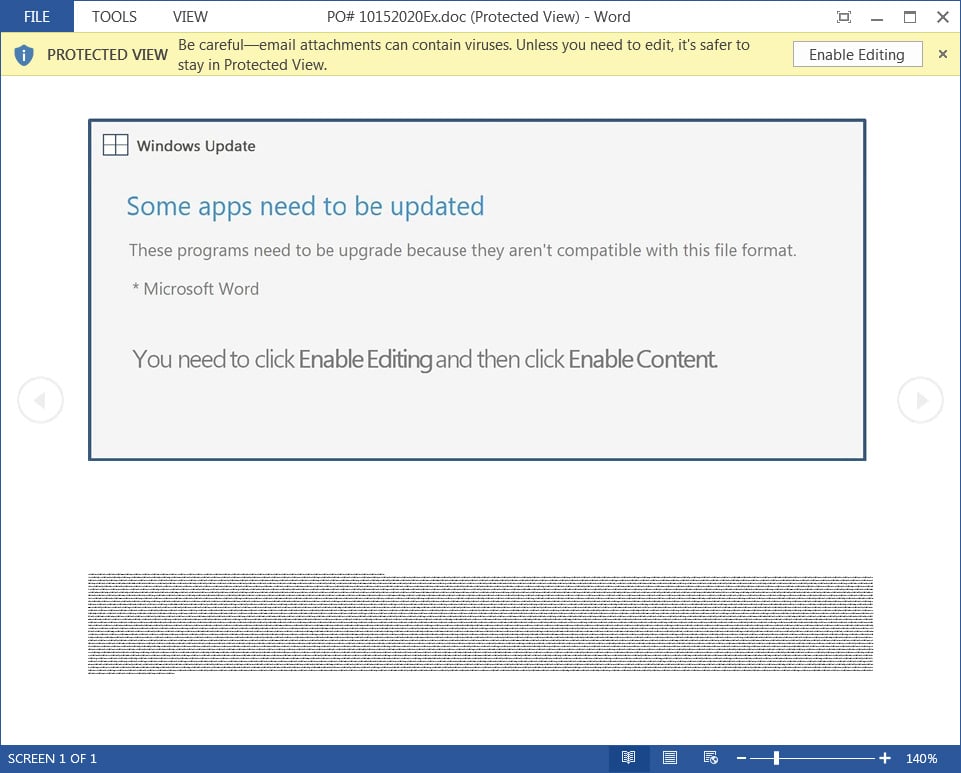
Emotet emails may contain messages like a familiar branding designed as a legitimate Windows Update telling you to upgrade Microsoft Word and ultimately leads to a ransomware attack on a victim’s network.
According to a report by Bleeping Computer, the botnet now comes with a malicious attachment claiming to be from Windows Update.
Attached to these spam emails are malicious Word (.doc) attachments or links to download one. The word document also tricks users with various document templates, pretending to be created on iOS devices, Windows 10 Mobile, or that the document is protected by prompting them to press “Enable Editing” and “Enable Content” to preview the document. Such that the macros will be executed to be downloaded and install the Emotet malware on the Victim’s computer.
Once after enabling macros in a malicious word document, a PowerShell command was executed that downloaded and executed the Emotet executable from hacked WordPress sites.
Emotet trojan is considered the most widely infecting malware that is targeting user’s current time. Moreover, it is also notably harmful as it also installs other harmful malware like Trickbot and QBot.
Emotet can even spot when it’s being run in a virtual machine and lay dormant in a bid to thwart anti-malware developers.
To avoid it, never open email attachments unless you know what they are (Emotet can make it appear as if the message is coming from one of your contacts if they’ve been infected), never enable macros in Word, and make sure you’re running a decent, up-to-date anti-malware program. With a fundamental thing provided with Security steps and tools to protect against such malware in your environment.








I know this site offers quality depending articles and other stuff