Since November 2023, the Cactus ransomware gang has been exploiting vulnerable Qlik Sense servers, leveraging multiple vulnerabilities including CVE-2023-41266 (Path Traversal), CVE-2023-41265 (HTTP Request Tunneling), and CVE-2023-48365 (Unauthenticated Remote Code Execution).
What is Qlik Sense Servers
Qlik Sense is a data analytics platform developed by Qlik, a software company specializing in business intelligence (BI) and data visualization. Qlik Sense allows users to create interactive dashboards and visualizations, analyze data from various sources, and gain insights to make informed decisions. It supports self-service analytics, enabling users to explore data and create personalized reports without extensive technical expertise.
Technical Analysis
Cyber Security News reports that threat actors targeted Qlik Sense servers by exploiting software vulnerabilities and deceiving victims with fabricated narratives.
However, according to Shadowserver reports, over 5,200 internet-exposed Qlik servers exist, with more than 3,100 vulnerable to exploitation by the Cactus group. In the Netherlands, 241 systems were identified, with 6 already compromised by threat actors. The process of identifying the server list and compromised servers entailed multiple research steps.
An existing Nuclei template is accessible for identifying vulnerable QlikSense servers online.
Researchers, however, utilized the “product-info.json” file to pinpoint vulnerable servers, as it contains crucial details like release labels and version numbers, providing insight into the specific QlikSense server version in use.
Additionally, the release label parameter contains details such as “February 2022 Patch 3,” indicating the latest update applied to the Qlik Sense server along with the corresponding advisory. To extract this data from the product-info.json file, you can utilize the following cURL command.
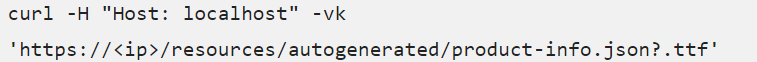
The command uses a .ttf file to point the request. Font files are accessible without authentication on Qlik Sense servers, with “Host: localhost” used to bypass HTTP 400 errors.
A patched server responds with “302 Authenticate at this location,” while a vulnerable server reveals file information with a “200 OK” response.
Furthermore, a “302” response or a release label parameter containing “November 2023” signifies a non-vulnerable server.
Discovering Compromised Qlik Sense Servers
Arctic Wolf states that the Cactus ransomware group redirects command output to a TTF file named qle.ttf, sometimes using the qle.woff file. These exploit files are accessible without authentication.
Upon inspection, approximately 122 servers were found to contain these specific files. The United States has the highest count with 49 servers, followed by Spain with 13, Italy with 11, the UK with 8, and Germany and Ireland each with 7. Additionally, there are 6 servers located in the Netherlands.
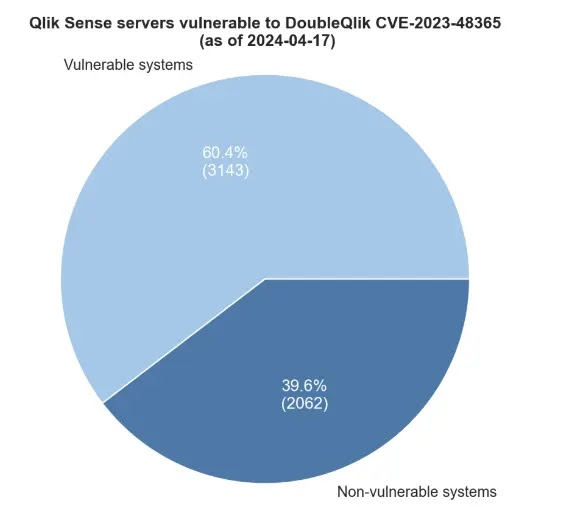
Organizations and QlikSense server users are advised to upgrade to the latest versions as per security advisories to mitigate the risk of exploitation by threat actors.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment