Threat actors are using the recently disclosed zero-day ProxyLogon vulnerabilities — installing a new strain of ransomware called DEARCRY in Exchange servers.
Zero-Day Exchange Vulnerability
Earlier this month, Microsoft revealed that four zero-day vulnerabilities being exploited by HAFNIUM threat actors in the wild.
Where these four zero-day vulnerabilities are chained together:
- to gain access to Microsoft Exchange servers
- steal email
- and, plant further malware for increased access to the network.
However, researchers in some knowledge forum raised a question — “Could the unpatched Exchange Servers from Zero-Day vulnerability campaign — open the pathway for ransomware infections?”
Yes, the researchers fear became a reality where threat actors are using the vulnerabilities to install the DearCry ransomware.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!
DearCry Ransomware
Microsoft researcher Phillip Misner tweeted “Microsoft observed a new family of human operated ransomware attack customers – detected as Ransom:Win32/DoejoCrypt.A,”.
Further added, “Human operated ransomware attacks are utilizing the Microsoft Exchange vulnerabilities to exploit customers.”
Certainly, the attack started March 9 after users began submitting their encrypted files and a new ransom note on ransomware identification site ID-Ransomware, according to Michael Gillespie the creator of the site.
Also, Gillespie after reviewing the submissions the submitted files are almost all of them are from Microsoft Exchange servers. Microsoft security researcher Phillip Misner confirmed that the DearCry.

Attack WorkFlow
According Palo Alto, Exchange Server’s new variant of ransomware exploit ProxyLogon vulnerability for initial access.
Firstly, DearCry runs a service named “msupdate” once launched, it is not native to the Windows operating system. Where once ransomware finishes its encryption process, the service is later removed.
Secondly, the ransomware will begin to encrypt files once they match the following extensions on the victims computer:
.TIF .TIFF .PDF .XLS .XLSX .XLTM .PS .PPS .PPT .PPTX .DOC .DOCX .LOG .MSG .RTF .TEX .TXT .CAD .WPS .EML .INI .CSS .HTM .HTML .XHTML .JS .JSP .PHP .KEYCHAIN .PEM .SQL .APK .APP .BAT .CGI .ASPX .CER .CFM .C .CPP .GO .CONFIG .PL .PY .DWG .XML .JPG .BMP .PNG .EXE .DLL .CAD .AVI .H.CSV .DAT .ISO .PST .PGD .7Z .RAR .ZIP .ZIPX .TAR .PDB .BIN .DB .MDB .MDF .BAK .LOG .EDB .STM .DBF .ORA .GPG .EDB .MFSNext, It will append the .CRYPT extension to the file’s name when encrypting victim’s files
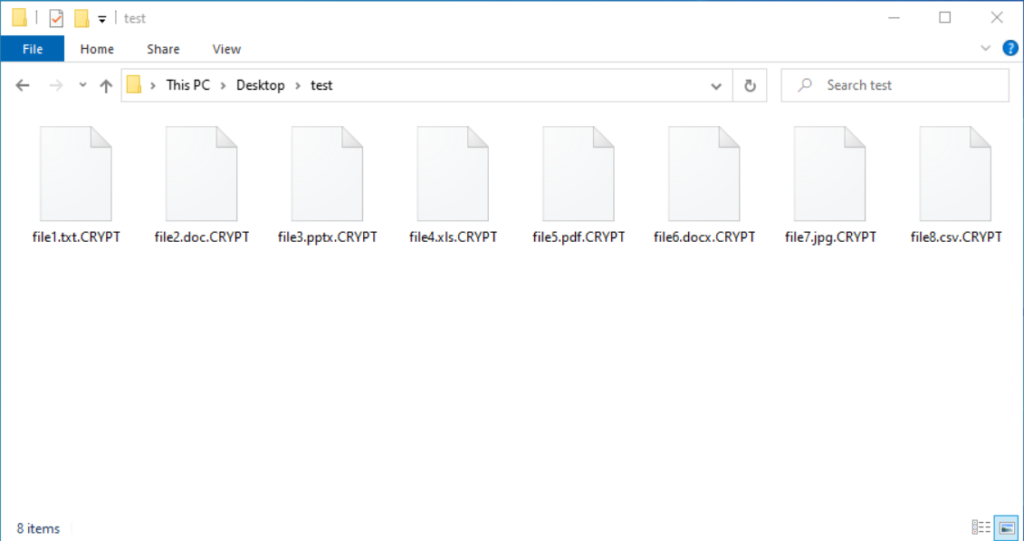
When executed, DearCry ransomware uses AES-256 and RSA-2048 to encrypt victim files, while also modifying file headers to include the string ‘DEARCRY!’

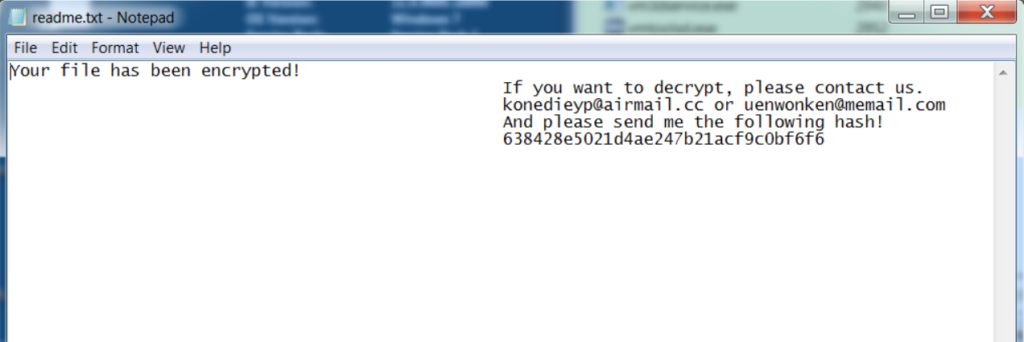
Further as part of Ransomware workflow, DearCry deploys a ransom note to the victim’s desktop, a note includes two email addresses
- konedieyp@airmail[.]cc
- uenwonken@memail[.]com
that the victim is asked to contact, and as well as a request for a provided hash to be sent.
Security Recommendation
According to Palo Alto Networks, there are still approximately 80,000 Exchange servers that cannot directly apply the recent security updates.
In short, not only to protect mailboxes from being stolen but to prevent them from being encrypted all organizations are strongly recommended to apply the patches as soon as possible.
And also to create offline backups of their Exchange servers.
Indicators Of Compromise
SHA256 Hash:
2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bff
e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6
feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33ede
FDEC933CA1DD1387D970EEEA32CE5D1F87940DFB6A403AB5FC149813726CBD65
10BCE0FF6597F347C3CCA8363B7C81A8BFF52D2FF81245CD1E66A6E11AEB25DAFile Name:
readme.txtEmails:
konedieyp@airmail.cc
uenwonken@memail.comRansom Note Text:
Your file has been encrypted!
If you want to decrypt, please contact us.
konedieyp@airmail.cc or uenwonken@memail.com
And please send me the following hash!
[victim id]












Leave A Comment