Hackers are once again using fake Google Chrome updates as means to infect unsuspecting users with malware.
According to NTT security analyst Rintaro Koike, the attack starts off with the threat actor compromising websites to inject a Javascript script that runs when a visitor comes to the website and shows a screen stating that the visitor needs to update their Chrome browser version.
How hacked sites are spreading malware:
The scripts themselves are delivered through Pinata IPFS (Interplanetary File System) which helps hide the origin server hosting the malicious scripts making blacklisting ineffective.
These scripts might also download additional scripts based on whether or not the visitor is among the campaign’s target audience.
After presenting the user with the fake update message, the script automatically downloads a ZIP file disguised as the Chrome update the user needs to install. However, this ZIP file actually contains a Monero miner. Once launched, it copies itself to the Chrome root directory as updater.exe. It then launches a legitimate executable called conhost.exe to carry out a process injection attack and runs straight from the system memory.
According to his analysis VirusTotal, the malware exploits the BYOVD (“Bring Your Own Vulnerable Driver”) to exploit one defect on WinRing0x64.sys and gain SYSTEM privileges on device you.
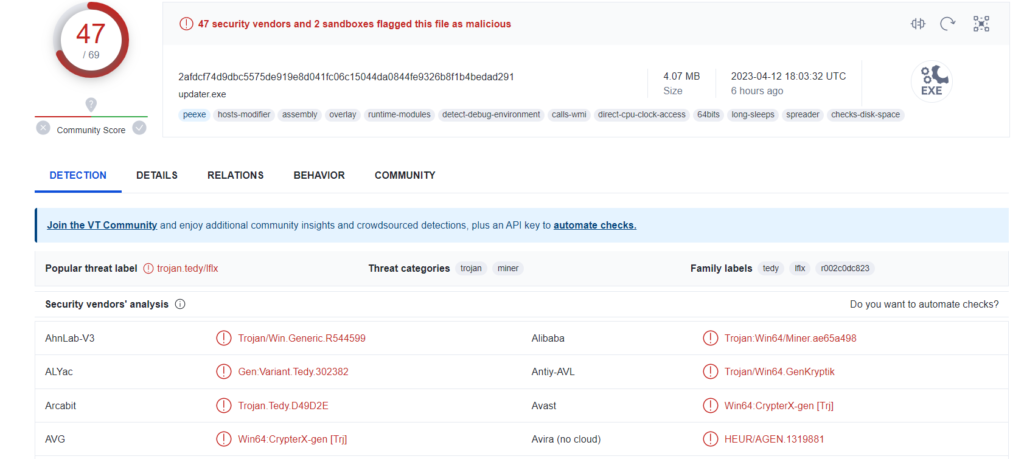
Unsuspecting users that fall for this trick end up installing a Monero miner on their PC instead of a legitimate Chrome update.
How to stay safe from malware spread through fake google chrome updates
- Besides keeping Chrome updated and avoiding pop-ups telling you to update your browser, you should also be using one of the best antivirus software solutions on your PC to help fend off malware infections and other cyberattacks.
- Your computer is only a part of the defense strategy you must employ. Malware can exploit many vulnerabilities, including unsecured networks. Luckily, you can guarantee that each network you connect to is safe.
- Even if you do have antivirus software, consider adding a Virtual Private Network on top of your security firewall. Indeed, the antivirus software can remove the virus, whereas a VPN can prevent the infection from getting into your device.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment