Cybercriminals are fabricating counterfeit websites containing software installers that have been infected with a downloader malware named Fruity. Their objective is to deceive unsuspecting users into unwittingly downloading this trojan, which can subsequently install remote trojan tools such as Remcos RAT.
Fruity Trojan
As reported by cybersecurity vendor Doctor Web, the deceptive software encompasses a range of tools designed for fine-tuning CPUs, graphic cards, and BIOS, in addition to other PC hardware-monitoring applications.
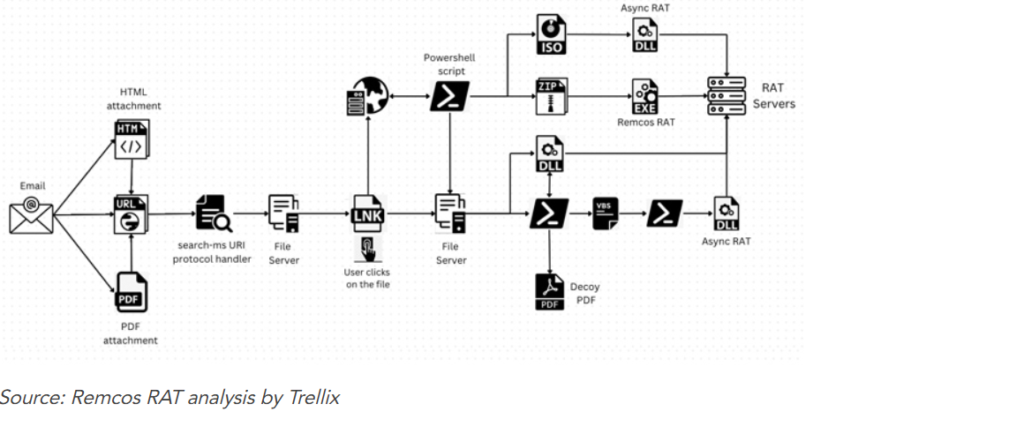
The precise method utilized to gain initial access remains unclear, but it might involve phishing, drive-by downloads, or malicious ads. When victims visit the counterfeit site, they are prompted to download a ZIP installer package.
Inside the installer, along with the genuine software, the Fruity trojan is placed. This Python-based malware disguises itself by embedding within an MP3 file and using steganography to conceal two executables and shellcode.
“This clever technique masks the fact that the user is receiving remote files, creating an illusion of trust. Consequently, the user is more likely to open the file, assuming it belongs to their system, and inadvertently execute malicious code,” explained a security analyst at Trellix.
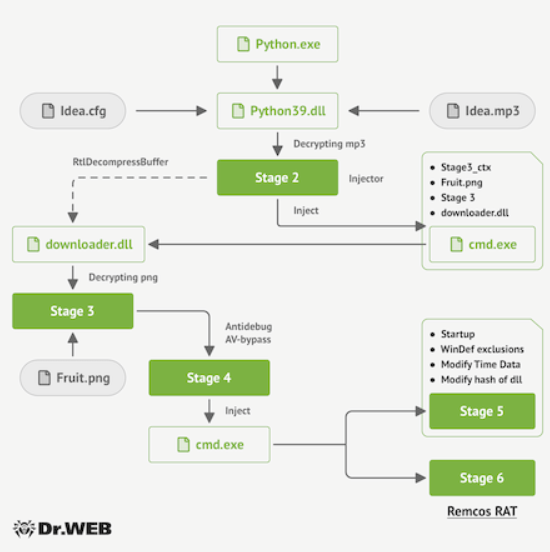
The attack sequence presents the risk of distributing various types of malware. Hence, it becomes essential to adhere to the principle of downloading software exclusively from reputable sources.
Coincidentally, Bitdefender has disclosed information about a malspam campaign that delivers the Agent Tesla malware, aiming to collect sensitive data from compromised endpoints.
A series of recent attacks known as Nitrogen involves distributing fake ISO files through deceptive ads that mimic download pages for popular applications like AnyDesk, WinSCP, Cisco AnyConnect, Slack, and TreeSize.
During their presence within the victim’s network, the attackers’ main objective is to acquire credentials, establish persistence on critical systems, and steal data, ultimately aiming for extortion.













Leave A Comment