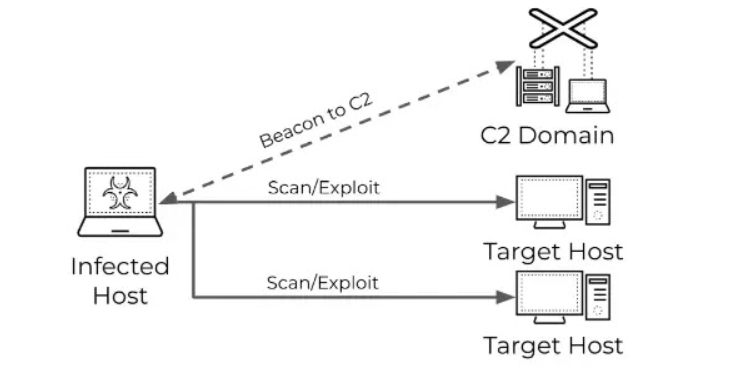
Hackers are employing malware-infected devices for scanning target networks rather than conducting direct scans. This strategy allows them to obscure their identity, circumvent geographical restrictions (geofencing), and expand their botnets.
Compromised hosts offer ample resources for conducting large-scale scans, surpassing the capacity of a single attacker machine. Effective detection systems analyze scanning patterns, such as request volume, to identify both established and new threats.
These scanning techniques uncover weaknesses in target networks, revealing open ports, software vulnerabilities, and operating system details.
Malware-Driven Scanning Attacks
Attackers exploit these vulnerabilities to gain unauthorized access or disrupt systems.
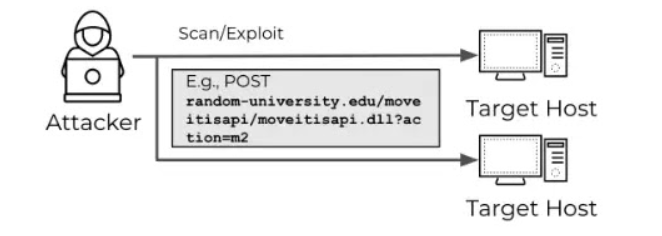
In this example, the attacker scans random-university.edu using an HTTP POST request to identify the MOVEit vulnerability (CVE-2023-34362), which, if successful, can lead to a compromise.
Examining traffic logs across various networks has revealed a notable surge in scanning activity aimed at potential vulnerabilities.
One instance saw a spike in requests (7,147 times in 2023) to endpoints linked with the MOVEit vulnerability (CVE-2023-34362). Additionally, telemetry data uncovered over 66 million requests in 2023, potentially tied to scanning activities.
Attackers employed new URLs in their exploits to evade security measures, as identified by Palo Alto Networks. Notable instances include a Mirai variant using “103.245.236[.]188/skyljne.mips” and an Ivanti vulnerability exploit attempt with “45.130.22[.]219/ivanti.js”.
In both instances, scanning requests preceded the detection of subsequent malicious payloads, underscoring the need for proactive scanning detection to mitigate threats promptly.
Attackers leverage compromised devices to conduct large-scale vulnerability scanning, evading detection while targeting various entities.
For instance, a Mirai variant exploit targets Zyxel routers, allowing for distributed attacks involving thousands of devices scanning numerous targets. Defenders must continuously patch vulnerabilities and update detection systems to counter evolving threats.
All about Ivanti Vulnerability Scanning
Chained vulnerabilities (CVE-2023-46805, CVE-2024-21887) enabled attackers to bypass authentication and execute commands in an attack campaign targeting Ivanti products.
Using the attack to harvest potential target IP addresses from a DNS logging service, attackers could execute commands and potentially gain access to vulnerable systems.
Common technologies like routers, web application frameworks, and collaboration tools are targeted, with recent attacks on Ubiquiti EdgeRouters and Cisco/NetGear routers by Russian and Chinese hackers indicating widespread vulnerability scans across various router brands.
Indicators of Compromise
IP addresses/URLs/SHAs that have hosted Mirai malware
- 45.66.230[.]32
- 85.208.139[.]73
- 87.120.88[.]13
- 95.214.27[.]244
- 103.110.33[.]164
- 103.95.196[.]149
- 103.131.57[.]59/mips
- 103.212.81[.]116
- 103.228.126[.]17
- 145.40.126[.]81/mips
- 146.19.191[.]85
- 146.19.191[.]108
- 176.97.210[.]211/mips
- 185.112.83[.]15
- 193.31.28[.]13
- 193.47.61[.]75
- 217.114.43[.]149
- 23190d722ba3fe97d859bd9b086ff33a14ae9aecfc8a2c3427623f93de3d3b14
Domain and URL associated with Ivanti vulnerability scans
- dnslog[.]store
- hxxp://45.130.22[.]219/ivanti.js
- 137.220.130[.]2/doc
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment