Palo Alto Networks alerts customers to a critical command injection vulnerability in PAN-OS GlobalProtect feature, scoring the maximum 10/10 on CVSS. Fixes are underway, the company reports.
PAN-OS COMMAND INJECTION VULNERABILITY
On April 12, 2024, Palo Alto Networks issued a report on CVE-2024-3400, a critical vulnerability in their PAN-OS, the foundation of their widely-used firewall solutions. Exploiting this flaw grants adversaries root-level access, prompting significant concern within the cybersecurity community.
Arbitrary code execution vulnerabilities can serve as entry points and facilitate lateral movement within a network. When present in firewall software, they pose the risk of network protection misconfiguration or even complete disablement. This is particularly concerning as it can enable the creation of stealth communication channels within the compromised environment.
AFFECTED VERSIONS
Palo Alto Networks confirms the vulnerability exists in PAN-OS versions 10.2, 11.0, and 11.1. However, earlier versions and certain auxiliary software used with the firewall remain unaffected. Unfortunately, patches for the affected versions are currently unavailable.
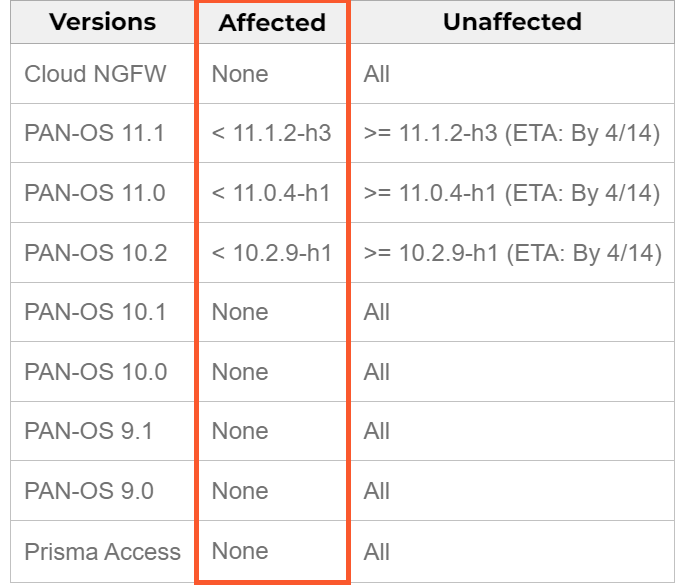
The company has committed to releasing fixes for all vulnerable versions on April 14, 2024. Additionally, they suggest a possible mitigation strategy, which involves disabling the device telemetry feature to reduce the potential impact of exploitation. For subscribers of their Threat Prevention service, Palo Alto Networks offers the ability to block potential exploitation attempts.
Vulnerabilities can exist in any software, including those from reputable vendors. Predicting which program will have a vulnerability is challenging, so reactive measures are crucial to mitigate attacks that exploit vulnerabilities.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment