A new ransomware family called ‘GwisinLocker’ targets South Korean industrial and pharmaceutical companies.
GwisinLocker ransomware
ReversingLabs researchers discovered a new ransomware family targeting Linux-based systems. The malware, dubbed GwisinLocker was detected in successful campaigns targeting South Korean industrial and pharmaceutical firm.
The name “Gwisin” (귀신) refers to the Korean term for a ghost or spirit.
When GwisinLocker encrypts Windows devices, the infection begins with the execution of an MSI installer file, which requires special command line arguments to properly load the embedded DLL that acts as the ransomware encryptor.
Analysis of GwisinLocker ransomware
The command-line arguments for the encryptor are listed below:
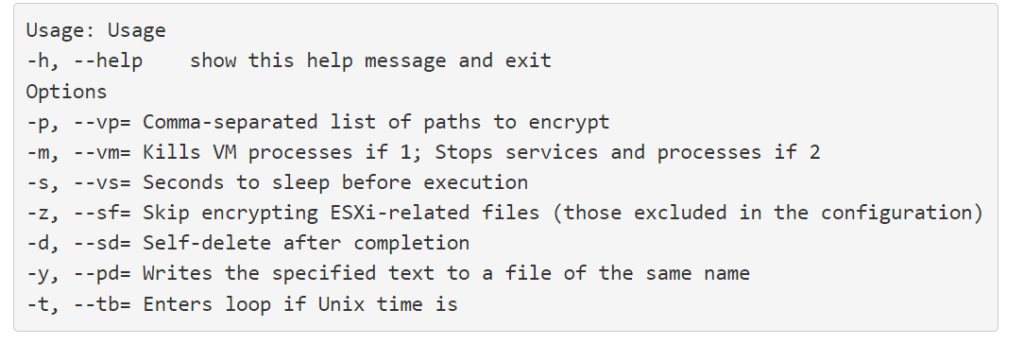
First, the malware redirects the standard input, standard output and standard error file descriptors to /dev/null to avoid outputting debug or error strings. Both the 32-bit and 64-bit samples used the file /tmp/.66486f04-bf24-4f5e-ae16-0af0fdb3d8fe as a mutex, writing a lock to the file. If GwisinLocker reads a lock set on this file, it exits immediately.
Next, the GwisinLocker.Linux ransomware decrypts its configuration data. GwisinLocker.Linux’s configuration is embedded in the malware, encrypted with a hard-coded RC4 key. The JSON configuration was the same in both samples and includes a list of excluded and targeted files.
Finally, the ransomware terminates several Linux daemons before initiating encryption to make their data available for the locking process.
Also, the attacks coincided with Korean public holidays and occurred during early morning hours, so Gwisin has a good grasp of the country’s culture and business routines.
Indicators of Compromise
The following are indicators of compromise (IOCs) assembled from GwisinLocker.Linux samples used in the wild.
The following hashes and strings correspond to files associated with active GwisinLocker.Linux variants and attacks.
| SHA1 Hash (Filename) | Description |
| (/tmp/.66486f04-bf24-4f5e-ae16-0af0fdb3d8fe) | Mutex |
| (!!!_HOW_TO_UNLOCK_MCRGNX_FILES_!!!.TXT) | Ransom Note |
| ce6036db4fee35138709f14f5cc118abf53db112 | GwisinLocker Ransomware (32-bit ELF) |
| e85b47fdb409d4b3f7097b946205523930e0c4ab | GwisinLocker Ransomware (64-bit ELF) |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment