Phishing attackers distribute email attachments with malicious HTML files designed to exploit users into running the code by prompting them to paste and execute it, leveraging social engineering.
A phishing campaign tricks people into opening harmful emails with urgent subjects like fee processing or operation instruction reviews. These emails contain fake Microsoft Word documents that are actually malicious HTML attachments.
When the attachment is opened, the user sees a fake message that looks like a Word document. It usually has a button labeled “How to Fix” or similar, which is used to trick the user.
Clicking the button triggers the intended exploit, likely leading to malicious activities such as downloading malware or stealing sensitive data. When the user clicks “How to Fix,” a malicious JavaScript file is downloaded. The file encodes a PowerShell command using Base64 and then instructs the user to either use a keyboard shortcut (Win+R, CTRL+V, Enter) or open PowerShell and run the command manually.
After following these instructions, the JavaScript decodes the Base64-encoded command, places it in the clipboard, and executes the PowerShell command, potentially harming the user’s system. The malicious email attachment triggers a PowerShell script download from the Command and Control server (C2), which wipes the clipboard and executes another PowerShell command also retrieved from C2.
The first PowerShell script downloads an HTA file before executing the second one, and an embedded Autoit executable within a ZIP file uses a compiled Autoit script to complete the infection chain.
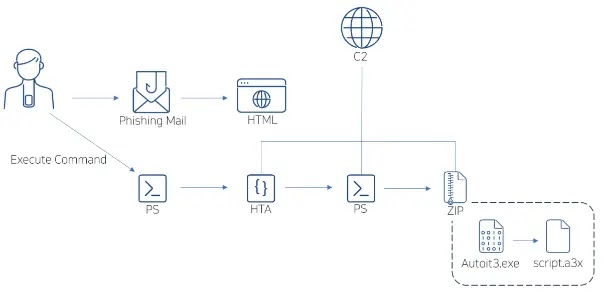
ASEC reports that DarkGate malware uses AutoIt scripts to avoid detection and maintain persistence, often obfuscating its code to evade detection, download, and execute the main payload. Due to DarkGate’s multi-stage infection process, traditional signature-based methods may fail. It is important for users to be cautious when dealing with files from untrusted sources, especially email attachments and URLs, in order to reduce the risk of DarkGate infection.
The system detected multiple threats, including phishing emails (HTML.ClipBoard.SC199655), malicious scripts (VBScript, PowerShell, HTA), trojans (AU3.Agent), and a potential execution of malicious PowerShell code (MDP.Powershell.M2514).
Files with the names header.png, qhsddxna, script.a3x, dark.hta, rdyjyany, script.a3x, 1.hta, and umkglnks were retrieved from suspicious URLs (hxxps://jenniferwelsh[.]com, hxxp://mylittlecabbage[.]net, hxxps://linktoxic34[.]com, hxxp://dogmupdate[.]com, hxxps://500 Internal Server Error: The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application., hxxp://flexiblemaria[.]com), indicating a potential phishing or malware attack.
Here are some simple mitigation steps to reduce the risk of phishing or malware attacks:
- Email Awareness: Educate employees about the dangers of opening attachments or clicking links from unknown or untrusted sources in emails.
- URL Filtering: Use web filtering tools to block access to potentially malicious websites and URLs.
- Antivirus Software: Ensure all systems are equipped with updated antivirus software to detect and remove malware.
- Regular Updates: Keep all software and systems updated with the latest security patches to address known vulnerabilities.
- Password Security: Encourage the use of strong, unique passwords and consider implementing multi-factor authentication for added security.
By following these simple steps, organizations can strengthen their defenses against phishing and malware threats.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment